Perfect Privacy Review in USA 2023
Perfect Privacy VPN has a perfect no-logs policy but isn't recommended for streaming. It is an expensive VPN but having a slow server speed. For the price of $9.99/mo, it manages to earn 2.4 stars rating.
- Updated: February 21, 2024
- 0 User Reviews
- Minnie J. Hamilton
| Based in | Switzerland [SAFE] |
| Price | $9.99/mo |
| Servers | 58 (26 Countries) |
| Logs | No Logs |
| Multi Login | Unlimited Devices |
| Refund | 7 Days |
| Recommended | No |
| Website | Perfect-Privacy.com |
Perfect Privacy is one of the most expensive VPNs in the industry, yet its users are growing in tandem because it is truly a ‘No-Log‘ VPN.
Perfect Privacy boasts some high-end security features that are hard to find elsewhere. That’s true too. Multi-hop and NeuroRouting features are one of its great strengths. You can check the best VPN recommended and tested by us which will provide high-end security at more affordable prices.
But its server speed and server count are both low. It has only 58 servers and brings you the slowest speed possible for streaming.
Unfortunately, it does not cater to iOS users, lacking a dedicated app for iPhone or iPad users. For iOS devices, we would recommend checking out top VPNs like ExpressVPN or Surfshark because they offer comprehensive support and features.
Read our Perfect Privacy review in detail.
Also, get the best value for the price you pay for a VPN on our VPN reviews guide.
Perfect Privacy Review – Rating Criteria
This is the list of 8 factors that I will be using to perform this review:
- Pricing – How much does Perfect Privacy cost?
- Security – Is Perfect Privacy safe?
- Jurisdiction – Where is Perfect Privacy located?
- Speed – How fast is Perfect Privacy VPN?
- Streaming – Perfect Privacy VPN Netflix & Other VoD Services
- Leaks – Does it leak IP, DNS & WebRTC?
- Trustworthiness – Logs and Customer Support
- Compatibility – Apps and Supported Devices
Pricing – How much does Perfect Privacy cost?
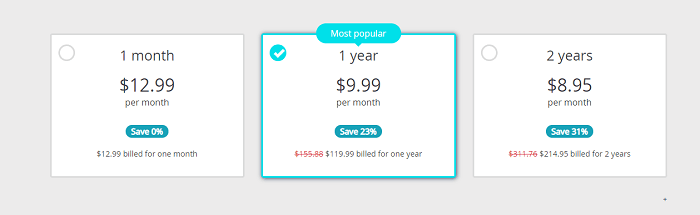
There is no doubt that Perfect Privacy is an expensive VPN service. These are the 3 different pricing plans. I have listed them below:
The promise of a superior VPN service aside, these rates are high enough to drive away many customers who would otherwise be interested in what Perfect Privacy has to offer.
So how did Perfect Privacy build such a massive customer base with ridiculously high prices? I’ll be discussing it in this Perfect Privacy review.
Payment Methods
Here is a list of payment methods being offered by Perfect Privacy VPN:
- Paymentwall (more than 60 options)
- PayPal
- Bitcoin

Under the payment wall option, it covers VISA, MasterCard, Amex, Mobiamo, and a lot of others.
Refund Policy
Perfect Privacy refund window extends to 7-days. Although it has a few standard clauses, there is no usage limitation or any other restriction in the company’s refund policy.
You could take the VPN for a drive for a week and get your money back if you did not enjoy the experience.
Security – Is Perfect Privacy safe?
Yes, Perfect Privacy is safe to use because it uses the strongest encryption, i.e., 256-bit, which is the industry’s highest.
It offers multiple protocols and encryption services, i.e., PPTP, OpenVPN, and IPSec.
Here are some top-notch security tools used by Perfect Privacy.
Perfect Privacy Proxies
Perfect Privacy offers Squid and SOCKS5 proxies that do not provide much privacy on their own but can temper with greater security.
To make your proxy connections much safer, you can:
- Connect proxies to the Tor network
- Connect to VPN via the proxy
- Apply an SSH Tunnel to the proxy
Perfect Privacy SSH Tunnel Feature
With an SSH Tunnel, you can transport some of your networking data through a secure SSH connection. It can also be used for bypassing firewalls that filter some specific content.
Multi-hop VPN
Connect to two different servers before your internet traffic is routed through a destination server. The multi-hop feature completely hides your online identity and IP.
Perfect Privacy NeuroRouting
It is a new advancement in multi-hop connection.
In NeuroRouting, a neural network evaluates routes to different sites and determines how to minimize the traffic outside of the VPN network.
The neural network uses Tensorflow, an open-source library for machine learning. This allows it to learn the best and the safest routes for different websites and servers.
Jurisdiction – Where is Perfect Privacy located?
Perfect Privacy is based in Switzerland. It is not a part of 5 eyes, 9 eyes, or 14 eyes country, but it does assist these countries in intelligence sharing.
So, you’re never safe using Perfect Privacy VPN. You always got to choose a perfect VPN starting with their jurisdiction.
Servers
It has 58 servers available in 26 countries. It also specifies the name of countries where its servers are available.
It also has servers in China, Israel, and Russia. These are the countries with the toughest internet restrictions. Hence, Perfect Privacy uses obfuscation servers to bypass restrictions.
You can also check out server loads from their website.
Speed – How fast is Perfect Privacy?
Perfect Privacy VPN speed is not the fastest. In fact, it has gives a poor internet speed when connected to its Amsterdam server.
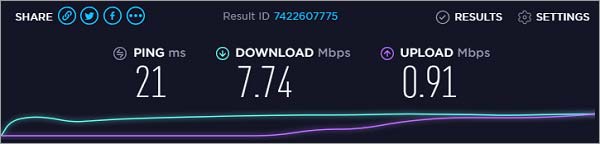
To review Perfect Privacy’s speed, I ran tests on its three servers using a 30 Mbps connection.
I could only get 7.74 Mbps speed when connected to Perfect Privacy.
Here is the test result:
Streaming – Perfect Privacy VPN Netflix & Other VoD Services
Perfect Privacy does not work with Netflix, nor does it advertise itself as the premier VPN for Netflix. Perhaps Netflix geo-dodging is not one of the VPN’s priorities.
The same happened when I tested the VPN for Hulu. My Netflix and Hulu tests were a dud. In the immortal words of Rolling Stones, ‘You can’t always get what you want.
The same goes for Kodi as well. This is because Perfect Privacy may not unblock geo-restricted content on Kodi.
Hence, you have to use the VPN XBMC service to securely watch geo-limited content on the famous platform.
Leaks – Does it leak IP, DNS & WebRTC?
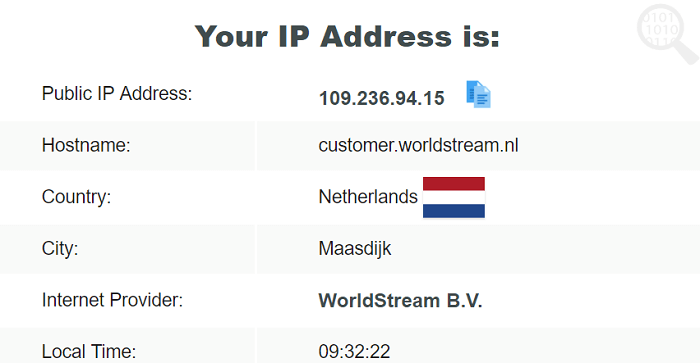
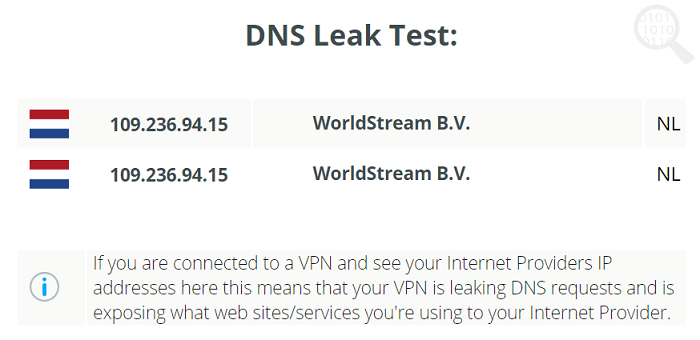
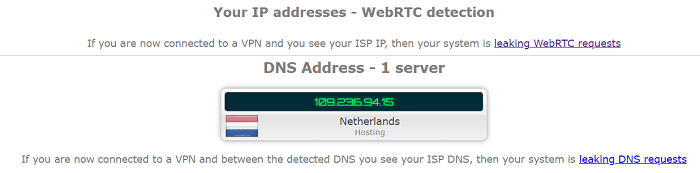
I tested for all kinds of leaks, and I was glad to know that it did not leak any IP, DNS, or WebRTC. I connected to its Amsterdam server.
Here are the test results:
IP Leak Test:
DNS Leak Test:
WebRTC Leak Test:
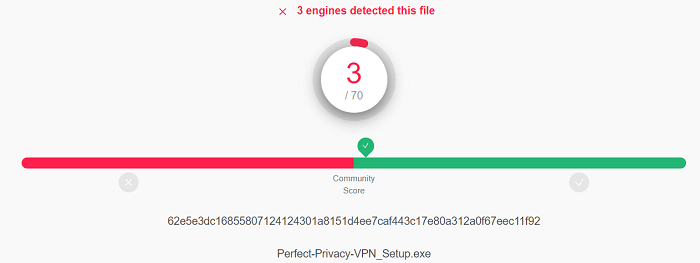
Virus Test:
I ran the virus test on its Windows client. I was glad to know that it had 3 viruses which is a bit of shocking news.
You can check out the results below:
Trustworthiness – Logs and Customer Support
I learned in our Perfect Privacy VPN review that it does not store any logs. The only data they collect are listed below:
- Login credentials
- Expiry date
- Email address
According to their statement from privacy policy:
“We do not store payment information such as credit card details. These are processed exclusively by the payment service providers.”
That’s a sigh of relief as they do not hold any payment details. Perfect Privacy has the usual No logs policy.
Customer Support
The customer support of Perfect Privacy is decent. You can contact their support staff with Ticket System and Forums.
You can also take help from their FAQs section and Manual Tutorials.
Compatibility – Apps and Supported Devices
Perfect Privacy Review has dedicated apps for Windows, Mac OS, Linux, and Android. It is also installed on routers.
Surprisingly, the iOS app is still in work, which means that iPhone users need a third-party OpenVPN app to access the service.
Perfect Privacy Windows Client
Windows users, too, have the option of using the VPN service with OpenVPN GUI, Viscosity, and IPSec/IKEv2, but I recommend a custom Perfect Privacy client for a more fulfilling experience.
Windows client of this VPN is stacked with security features. Also, it allows you the liberty of customizing it as per your liking.
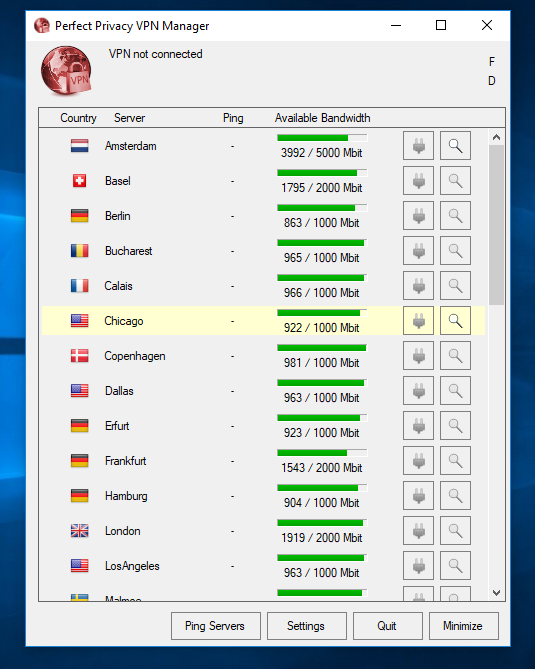
The setting allows you to configure a variety of options, including Auto-connect with the pre-selected server.
The client also includes some of the advanced kill switch, firewall, and leak protection tools.
Comparison between Perfect Privacy and ExpressVPN
Here is a quick comparison between the two service providers with their features and price. Let us know which one is the best:
| Features | ExpressVPN | Perfect Privacy |
|---|---|---|
| Price | $6.67/mo | $9.99/mo |
| Servers | 3,000 in 94 Countries | 58 Servers in 26 Countries |
| Compatibility | All Devices | Windows, macOS, Linux, Android & Routers |
| Jurisdiction | The British Virgin Islands | Switzerland |
| Logging Policy | Zero Log | No Logs |
| Customer Support | Live Chat & Email Support | Tickets & Forums |
| Trustpilot Score | 4.7 | 3.0 |
| Website | ExpressVPN | Perfect Privacy |
Alternatives
Suppose you are not quite satisfied with what Perfect Privacy has to offer, then fret not. There are other options available. Below are the reviews of some capable VPN services.
- Review ExpressVPN
- Review Surfshark
- Review Celo VPN
- Review PrivateVPN
- VPN Gate Review
- Review NordVPN
- Norton Secure VPN
- VIP72 Review
- Buffered VPN Review
- Review PureVPN
- Review Tor VPN
- Review Super VPN
Do I Recommend Perfect Privacy?
No, I do not recommend Perfect Privacy.
Perfect Privacy VPN isn’t perfect at all. It does a good job being a no-log VPN, but it is based in Switzerland, which actually has data retention laws.
It is also the most expensive VPN, and it isn’t worth spending money on the features it offers.
It has only 58 servers with the slowest speed and doesn’t unblock Netflix or other streaming services when I performed Perfect Privacy review.
It is not the perfect VPN I would recommend.