IT researchers at Google have declared NSO Group’s new ‘zero-click’ iPhone exploit as “Terrifying.”
Google’s Project Zero researchers Ian Beer and Samuel Groß shared details on the new exploit of the NSO Group as “terrifying” because it allows the user of the software to hack any iPhone without having the victim do anything.
Wow. Just wow. This NSO zero-click iMessage exploit is the most impressive attack code I’ve ever seen. A whole computer architecture built out of a few logic operators… in an EXPLOIT!
The talent of the individuals who came up and developed this technique is beyond impressive https://t.co/X3nVli3bOC
— Dmitri Alperovitch (@DAlperovitch) December 16, 2021
Last month the US Department of Commerce also added Israel-based tech company NSO Group to its ‘entity list’ as it was revealed that the smartphones of US State Department Employees were hacked by NSO firm’s spyware. NSO’s Pegasus Spyware was found targeting iPhones of prominent personalities, including the Arab royal family, news reporters, Jamal Kashoggi, and more.
Apple has also filed a lawsuit against the NSO group to ban the use of spyware on its devices. After all the allegations, Israel restricted the supply of spyware to a few countries only.
NSO’s New ‘Zero-click’ Exploit
Google’s research team has analyzed a new exploit that targets iOS 14.7.1 and is deemed as “one of the most technically sophisticated exploits” ever seen.
According to GPZ’s Ian Beer and Samuel Groß:
“The exploit creates an emulated computer environment within a component of iOS that handles GIFs but doesn’t normally support scripting capabilities. This exploit allows an attacker to run JavaScript-like code in that component in order to write to arbitrary memory locations – and remotely hack an iPhone. “
Previously, in the cases of one-click exploits, targets were sent links in the SMS messages, and the device was only hacked when the user clicked on the link.
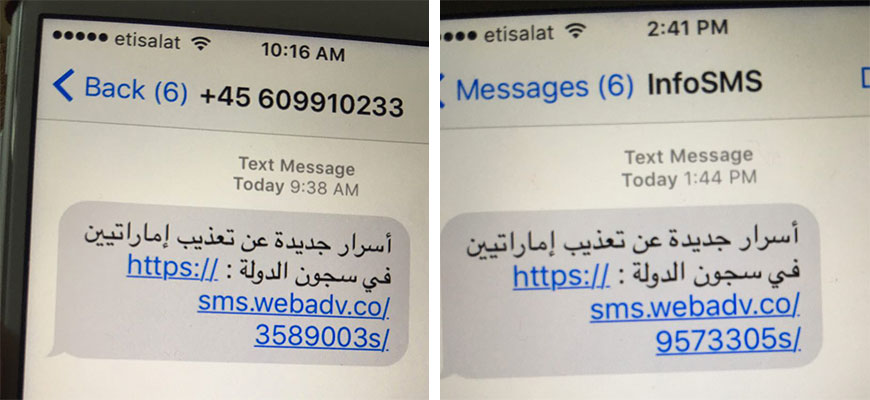
Screenshot of Phishing SMS in one-click exploits. (Image: CitizenLab)
One-click exploits have been changed to zero-click, where anyone can use the software to hack into iPhones without the user being aware of the intrusion. In zero-click attacks, no interaction is required from the user – meaning the exploit runs silently on the device in the background.
The initial entry point of the exploit is iMessage in iPhones so that the users could be targeted just by their Apple IDs or phone numbers. The vulnerability was further exposed when Apple introduced a new feature for GIF images as they are quite popular in meme culture. Apple started using a ‘fake gif’ trick that makes normal GIF images loop. The trick, however, also introduced over 20 image codecs, giving attackers a large attack base.
Apple said that they had removed the initial GIF code path starting from iOS 15.0, as the GIF decoding is taking place within BlastDoor now.
According to Google researchers, “NSO uses the “fake gif” trick to target a vulnerability in the CoreGraphics PDF parser.” The javascript inside PDFs makes the exploit development far easier – making PDS parser a prime target of NSO.
“The CoreGraphics PDF parser doesn’t seem to interpret javascript, but NSO managed to find something equally powerful inside the CoreGraphics PDF parser…” GPZ noted.
Among other crafty tricks, NSO also made use of Apple’s JBIG2 for compressing and decompressing images. Despite JBIG2’s lack of scripting, NSO emulated a computer environment that allows them to write memory addresses using a language, unlike Javascript.
“JBIG2 doesn’t have scripting capabilities, but when combined with a vulnerability, it does have the ability to emulate circuits of arbitrary logic gates operating on arbitrary memory,” explains Beer and Groß. This new exploit is as terrifying as the Pegasus spyware tool used for spying in various parts of the world.
