Cybercrimes on a Roll
As hard as it is to admit, there is absolutely no denying the fact that cybercriminals have overpowered the internet security agencies in 2014. The cybercrimes have not only increased by big numbers but they have exposed the loopholes in our online security as well.
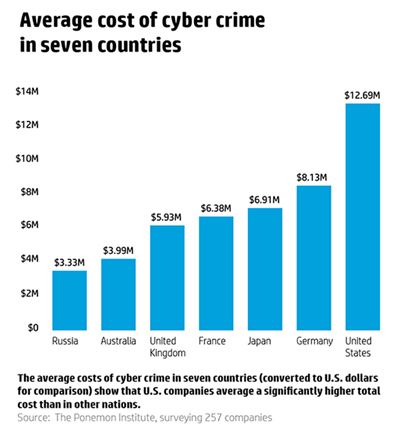
According to Poneman Institute, US, when compared with other countries, has spent more in strengthening its defenses against the cybercriminals and the cybercrimes. Have a look at the chart below to better understand how each country is investing the money to combat the cybercrimes.
We have further classified the cybercrimes into three different categories to give you a better idea of the impact of the cybercrimes in 2014. We will talk about the cybercrimes with respect to the industry, institutions and popular platforms and the damage they have inflicted upon the users to make you understand which sectors have been targeted the most.
The cybercrimes that took place globally are too many to list here. Therefore, we have selected the ones that have not only deeply affected the privacy policy of the internet users but have also raised the eyebrows on the performance of cybersecurity agencies all over the world.
Business Sector
The business sector has been a subject of devastating cyberattacks this year. We are going to list down some of the attacks that affected many people and were considered the deadliest in the history of the cyber-world.
(1) JP Morgan Chase Bank
- 76 million households were directly affected
- 7 million small businesses also lost their data
- Confidential Information of customers including but not limited to names, social security numbers, address, email addresses, phone numbers and type of accounts being operated were stolen
- Russia – the prime suspect according to the officials

(2) Attack on Citibank and Regional Financial Corps (RFC)
- The hackers who breached JP Chase Morgan also sneaked in the servers of Citibank and Regional Financial Corps.
- Both reported unusual activities in their servers
- Both claimed no information was stolen
- Russian hackers suspected for retaliating against the sanctions imposed on Ukraine

(3) eBay
- Massive breach in the servers of eBay
- Data theft of approximately 145 million users
- Confidential data of the users was stolen including their eBay passwords
- Employee credentials were used to gather the user data

(4) Home Depot. Hack
- Massive data breach reported in September 2014
- 56 million debit and credit cards at risk of being used for fraudulent activities
- Free credit monitoring services to the potential victims for one year
- However Home Depot claimed that no PIN codes of debit cards were stolen

(5) Dairy Queen Malware Attack
- A malware attack stole the credit card info. of the users of Dairy Queen all over the US
- Secret Service jumped in and confirmed the same pattern has been used to attack other businesses in the past
- An estimated 600,000 customers all over the US were affected by the malware attack

Govt. Institutions
The cyberwar between the North America and the rest of the world has been going on for some time now. The cyberattacks were anything but mere attacks, they meant more to the hackers and the North American institutions. Even the UK wasn’t safe from the mess of the cybercrimes.
(1) US State Dept. Email Hack
- Unusual activity was reported in US State Dept. unclassified email addresses
- US State Dept. had to shut down the classified email addresses as well
- The attack was followed by a series of attacks on other institutes as well
- Remains unclear if the Russian and Chinese hackers are involved or not
(2) Toronto Police Website Down
- Anonymous group claimed that they had hacked the website of Toronto Police
- The websites of Ottawa City and Supreme Court of Canada were also hacked in a span of 4 days
- The hackers claimed to have taken down the website on Twitter. But suspended their account afterwards
- The hackers threatened to hack the website of Parliament of Canada as well
(3) US Postal Service Hack
- The servers of US Postal Service were breached
- Confidential information of 80,000 employees was compromised
- The breach took two months before they were finally discovered
- Offering the credit card monitoring services to employees for free for one year
(4) Nottinghamshire Police Website Attack
- A pro-Palestinian group, AnonGhost, hacked the website of the police force of Nottinghamshire
- Unlike the Toronto Police Website attack, AnonGhost took the website down in an allegedly political move
- The hackers warned the UK to not to support any further action of Israel
- The website was restored back to its normal state within a few hours
(5) US Weather System Hack
- Four websites of the NOAA were hacked by an ‘internet sourced attack’
- The hacking was quickly linked with China
- NOAA took a month to discover the breach in their servers
- The servers were restored to their normal position as soon as they discovered the breach
Popular Platforms Hack Attacks
Not only the institutions and business industries, the popular platforms were also hacked. No one seemed to be safe from the wrath of cybercrime and it haunted even the giants of the tech industry!
(1) iCloud Leaks
- Massive server breach in the servers of iCloud were reported
- Private pictures of 26 celebrities were leaked online, including the pictures of Jennifer Lawrence, Kirsten Dunst, Rihanna and Kate Upton etc.
- The pictures were first leaked on 4chan.org
- Apple denied the claims of server breach in a reactionary press conference and claimed that it was more specific cyber attack
(2) Dropbox Users in a Bit of Bother
- Some reports suggested that credentials of 7 million users were stolen
- Dropbox insisted that the attacks were not directed at their servers
- Dropbox claimed that the email accounts were stolen from other services
- However it was recommended to the users to change their passwords
(3) Apple Malware Attack
- A malware named “Wire Lurker” is discovered in the Apple devices
- The malware is said to be transferrable through the USBs.
- Approximately 500 apps have already been infected with the malware
- The malware is confined to China for now
(4) Hack of Sony Pictures Entertainment
- Servers of Sony Pictures Entertainment were breached in a cyberattack
- The attack was so massive that the employees were instructed to leave the workplace until the problem was resolved
- The hackers got access to all the confidential data of the Sony Group including 5 unreleased pictures made under the banner of Sony
- They threatened to release them until the movie The Interview was not stopped from being released
- The hackers are being linked to North Korea because the movie criticized the President of North Korea. However, North Korea denied any sort of involvement in the hacking.
(5) Lizard Squad’s Attack on Gaming Platforms
- The servers of PlayStation Networks, Xbox Live and Twitch were breached in a cyberattack
- The Lizard squad was involved in disabling these gaming servers in DDOS attacks for hours
- The Lizard Squad also issued a false bomb threat to an American Airline that had a high official of Sony on-board
- The recent development suggests that they have claimed to have taken down the servers of EA Sports.
How an Average User Should Fight the Cybercrimes
We are talking about a general internet user and not limiting the scope to a certain region. A normal internet user does what he thinks will keep his device safe and secure. But that’s not entirely true. Installing an anti-virus doesn’t mean you are safe from the thorns of cybercriminals.
Similarly, it is not necessary that you’d be free from the unwanted online surveillance either by agencies or by cybercriminals. Therefore, it is always advisable to use a VPN service while surfing the internet because it cloaks your real IP address and tunnels all your traffic through an encrypted channel to make sure that it is safe.
| VPN Providers | Price ($) | Special Deals | More Info |
|---|---|---|---|
|
Overall Best VPN

ExpressVPN
|
$12.95
$6.67
Per Month |
Exclusive Offer
Save 49% today! |
|
|
Fastest VPN Service

Surfshark
|
$12.95
$2.49
Per Month |
82% Off
2 Year Plan |
|
|
Best for Geo-Unblocking

NordVPN
|
$11.95
$3.99
Per Month |
69% Off
2 Year Plan |
|
|
Feature-rich VPN

PureVPN
|
$10.95
$3.29
Per Month |
81% Off
Exclusive 2 Year Offer |
|
|
Best for Private Browsing

CyberGhost
|
$12.99
$2.03
Per Month |
83% Off
3 Years + 4 Months Free |
The Year 2015 holds for us…
More cybercrimes. Even though, we feel absolutely terrible to say that but the future of online security, as of now, looks very bleak.
That’s right; the ever-increasing rate of cybercrimes and the continuous online surveillance by NSA and GCHQ has paved the way for cybercriminals to sneak into our computers with more ease.
Gone are the days when you could have trusted the government agencies to keep you protected from the malicious hack attempts, now they use all the means to keep an eye on your online activities.
So, your online security rests upon your shoulders and the way the rate of cybercrime keeps growing every day, it comes as no surprise that the current rate is most likely to increase next year.

