Cybersecurity researchers discover a new malware called BotenaGo that uses more than 30 security vulnerabilities to attack the Internet of Things, threatening millions of routers and IoT devices across the world.
Researchers at AT&T Alien Labs detailed that Golang malware (BotenaGo) uses a number of methods to attack devices by creating a backdoor. “Deployed with more than 30 exploits, it has the potential of targeting millions of routers and IoT devices,” the researchers say.
Key Takeaways:
- Golang malware (BotenaGo) uses more than 30 different exploits to attack devices.
- The malware creates a backdoor and waits to receive a target from the remote operator or from someone else on the same machine.
- It is not clear who is behind the malware and the number of affected devices.
A new #BotenaGo #botnet targets millions of #IoT devices using 33 exploits.#CyberSecurity #infosec #cybercrimehttps://t.co/iZZVxDXD42 pic.twitter.com/ukmF6PSNQ2
— twelvesec (@twelvesec) November 14, 2021
Golang Malware Analysis
Golang is an open-source language designed by Google in 2007 used by developers to build software. According to recent researches, Go programming has increased in popularity among malware creators in the past few years. According to intezer, there has been a 2,000% increase in Go-written malware across the world.
According to BleepingComputer, one reason behind its growing popularity is that its code payloads are hard to detect. It creates two backdoor ports: 31412 and 19412 to receive the information and execute the attack.
"Newly surfaced #malware that is difficult to detect and written in Google’s open-source programming language has the potential to exploit millions of routers and IoT devices, researchers have found."#Google #GoLang #BotenaGo #zeroday #CVEhttps://t.co/yhZaQr4u08
— ScFrazer (@swisstfrazer) November 15, 2021
Researchers also find the malware as a variant of Mirai, an IoT malware botnet that was used in 2016 for DDoS attacks on large sections of the internet. According to AT&T researchers, only 6 out of 62 Antivirus engines on VirusTotal flag. Therefore, the malware has a very low detection rate.
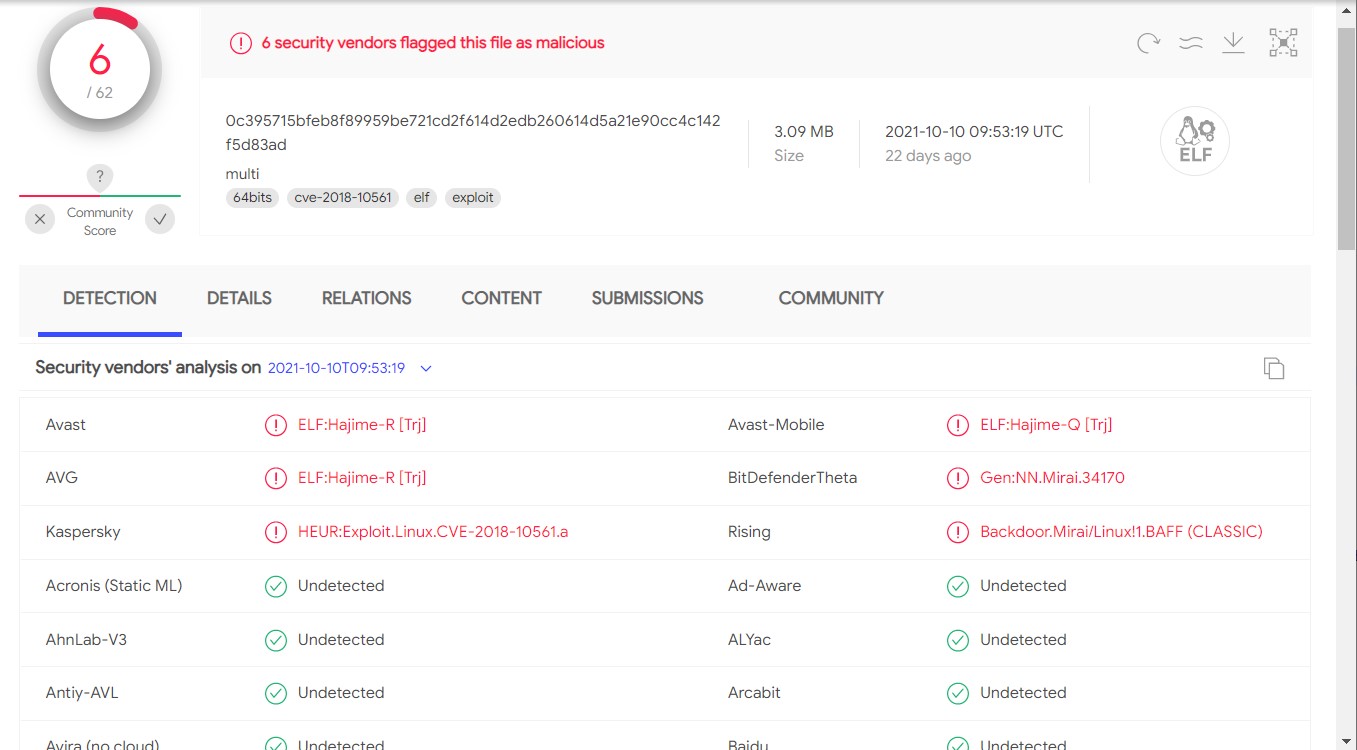
BotenaGo goes unnoticed by AV engines. (Image: AT&T)
BotenaGo Malware Targeting Millions of Devices
BotenaGo malware uses 30+ exploits to target various devices such as modems, routers, NAS devices, and IoT devices. Some popular devices vulnerable to this malware include routers for IOT devices, Netgear devices, Realtek routers, Tenda products, and many more.
Once the malware gets access to the device, it will be able to execute shell commands to turn the device into a botnet.
According to the AT&T research lab, if we search one Boa string in SHODAN, the results reveal almost 2 million IoT devices that are potential targets of the malware.
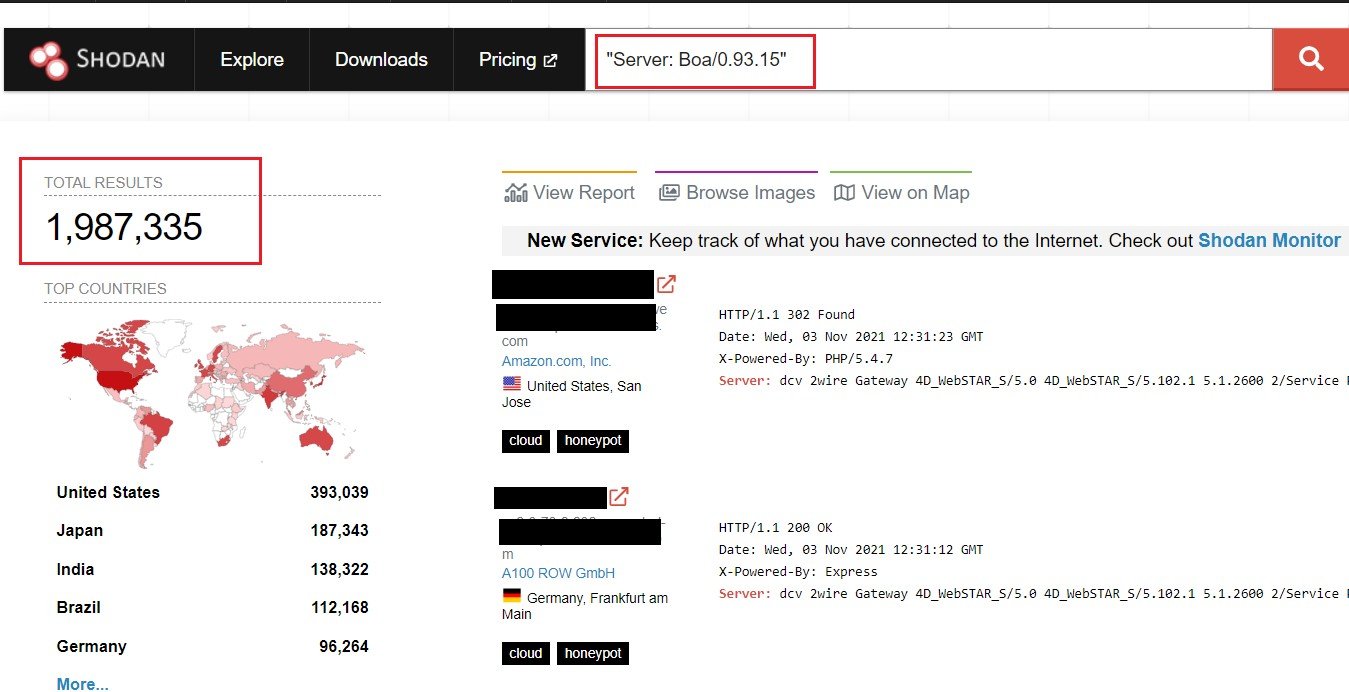
Shogan shows 2 million results on Boa. (Image: AT&T)
This IoT malware can potentially compromise millions of devices worldwide and is hard to detect. Currently, we don’t see any communication between the control and command servers.
According to Alien Labs, there are three options:
- First, BotenaGo is one module of a large malware suite that is dormant right now.
- It could be connected to Mirai, the IoT malware botnet.
- BotenaGo might still be in its development or beta phase and has been accidentally released.
Even if the malware is in-active, the number of security vulnerabilities exploited by this Golang malware is too high, putting millions of devices at risk of attack.
Due to BotenaGo malware’s incomplete status, we still cannot say how many devices it has affected as of today, but there is no doubt of its capabilities as it can use more than 30 exploits to target devices and remain undetected.
Fortunately, the botnet has been identified early so you can protect your devices beforehand. Make sure the software is updated and security updates are applied as soon as possible to minimize the opportunities to exploit new vulnerabilities in the system.
Make sure to deploy firewalls, VPNs, and other security measures to protect IoT devices against such attacks.
