Federal Bureau of Investigation (FBI) believes that FIN7, a Russian hacking group is behind sending USBs infected with ransomware to organizations. The hacking gang has previously been behind the operations of BlackMatter and Darkside.
According to the US intelligence agency, the packages were sent through United Parcel Service and United States Postal Service and seemed to be official organizations.
FBI warns hackers are sending USBs infected with ransomware to businesses https://t.co/MRAEKFwVfb pic.twitter.com/17dX3eWKfa
— New York Post (@nypost) January 9, 2022
In a recent flash alert, the FBI warned US-based organizations about these USBs and declared that the group FIN7 has been targeting the defense industry of the United States.
The packages mailed by the cyberattackers comprised Bad Beetle USB/BadUSB with the logo of LilyGO that’s generally available on the internet for sale.
They further added that the attackers pretended to be from Amazon or US’s Health and Human Services Department to trick their targets.
According to their statement:
“Since August 2021, the FBI has received reports of several packages containing these USB devices, sent to US businesses in the transportation, insurance, and defense industries,”
“The packages were sent using the United States Postal Service and United Parcel Service.”
“There are two variations of packages—those imitating HHS are often accompanied by letters referencing COVID-19 guidelines enclosed with a USB; and those imitating Amazon arrived in a decorative gift box containing a fraudulent thank you letter, counterfeit gift card, and a USB.”
REvil or BlackMatter deployed on Compromised Networks
The reports received to the FBI from August mentioned that considering the imitated entity, the packages contained phony gift cards, letters containing the guidelines of Covid-19, as well as falsified thank you notes.
As soon as the targets plug in the USB to their computers, it registers itself as a Human Interface Device (HID) Keyboard automatically and then initiates injecting keystrokes to download malware payloads to the infected systems.
The ultimate goal of FIN7 is to get access to a target’s system and infect it with ransomware (including REvil as well as BlackMatter) within the network through tools like Cobalt Strike, the Griffon backdoor, PowerShell scripts, and Metasploit.
FIN7 Attacks
These attacks follow a series of incidents that the FBI warned about around two years ago, including FIN7 impersonating Best Buy and mailing malicious flash drives to restaurants, retail businesses, and hotels.
The reports of these attacks started coming into the limelight from Feb 2020. Various targets of this incident reported that they were called and emailed by the hackers to plug the devices into their systems.
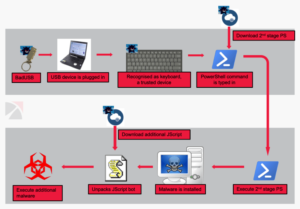
(Image Credit: BleepingComputer)
From May 2020, targets also received malicious parcels by FIN7 that contained items such as teddy bears.
The type of attacks FIN7 targets only becomes successful if the user plugs the USB/drive into their systems. Businesses can prevent attacks like these by allowing their employees to connect USBs and flash drives only after they are examined carefully by their security specialists or based on their hardware IDs.
Last year, FIN7 also formed a fake company and tried recruiting security workers for cyberattacks.
This breach is known to be the largest ransomware attack that reportedly hit around a million IT systems worldwide in 24 hours through targeting an American software firm, Kaseya’s systems.
