FIN7, a Russian hacking group, set up a fake security organization named Bastion Secure in early 2021 and used it to lure cybersecurity workers, hire them, and then trick them into aiding in ransomware attacks. The company claims to provide cybersecurity services to public sectors and private organizations across the globe.
A Recorded Future division, Gemini Advisory, conducted an investigation and revealed that the company is a cover for the FIN7 hacking group that used the website of Bastion Secure to post job ads on various Russian job portals, desiring to recruit technology workers for multiple positions.
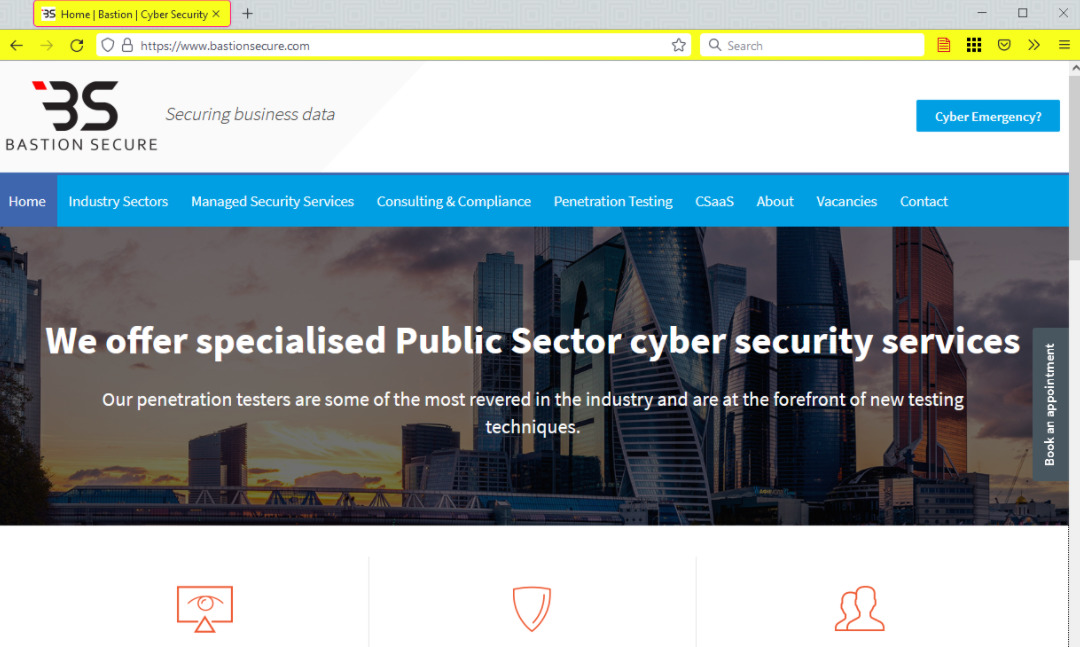
Image: The Record
As per the advertisements on its website, FIN7 hired PHP programmers, system administrators, Python, C++, and reverse engineers.
One of Gemini Advisory went through the entire recruitment process to study the company that all the people who applied went through an interviewing process including three phases:
Phase 1:
A basic interview was conducted in the first phase by an HR professional carried out via Telegram. After successfully clearing the interview, the applicants were asked to sign a contract and non-disclosure agreement (NDA), and install various virtual machines and open ports on their computers.
Phase 2:
The second phase included the applicants receiving some actual security tools from the organization for conducting multiple test assignments.
Phase 3:
The final phase involved applicants participating in the real deal, i.e. conducting an actual penetration test against a Bastion Secure customer.
While the interviewing process overall seemed a bit shady, the last phase actually gave it away. Gemini Advisory stated that there were no documents authorizing the penetration tests in the 3rd phase, which is usually customary.
Moreover, the representatives of the company asked the applicants to use only use the tools that won’t be detected by any security software and to critically look for file storage systems and backups once they access the network of the company.
According to the researchers at Gemini Advisory unit:
“It became immediately clear that the company was involved in criminal activity. The fact that the Bastion Secure representatives were particularly interested in file systems and backups signals that FIN7 was more interested in conducting ransomware attacks than [point of sale] infections.”
A researcher who was offered a position by the Bastion Secure company analyzed the tools that they were provided by the company. Both toolkits Carbanak and Tirion (Lizar) have been previously attributed to FIN7 and both can be used to deploy ransomware and hack PoS systems. We recently saw similar attacks by FIN8, FIN7, and FIN6. In September 2021, FIN8 backdoored US finance organizations with malware.
FIN7 Cybercrime Group Identified as Darkside Raas Operators
The tools that were shared by Bastion Secure with an applicant (Gemini Advisory’s member) were linked to malware strains and have been a part of FIN7’s arsenal, like Carbanak and Lizar/Tirion. The Gemini member also said that the tasks assigned to all applicants “matched the steps taken to prepare a ransomware attack.”
According to Gemini Advisory, the company installed two ransomware strains Ryuk or REvil, that have been a part of FIN7 cyberattacks in the past few years.
As per Microsoft’s security researchers, newer attacks would have deployed on the BlackMatter and DarkSide ransomware. BlackMatter has recently attacked Olympus, a tech giant, and US farmer cooperative, New Cooperative Inc.
Furthermore, Microsoft representative Christopher Glyer and Nick Carr declared that FIN7 didn’t just deploy the DarkSide ransomware, but also managed the Darkside RaaS (Ransomware-as-a-Service).
Today @cglyer & I are having an on-stage reunion to give the first public insights into our mysterious #MSTIC counter-ransomware unit.
We will share #ELBRUS 🌋 (overlaps: FIN7) ties to ransomware and expose their new front company.
20 minute talk @ 2pm ET: https://t.co/unQs5yE3DG pic.twitter.com/2xAEiHLWGp— Nick Carr (@ItsReallyNick) October 7, 2021
FIN7 operated Combi Secure Previously
Forming a security firm wasn’t a new tactic for FIN7. They used the same tactic back in 2010 when they set up a phony security firm named Combi Security.
However, at that time, the company was engaged in deploying Point-of-Sale malware. They used Combi Security to hire security workers to breach various retail organization networks after which they deployed PoS malware into the system to steal credit card details of customers from the hacked networks, according to a report from US DoJ.
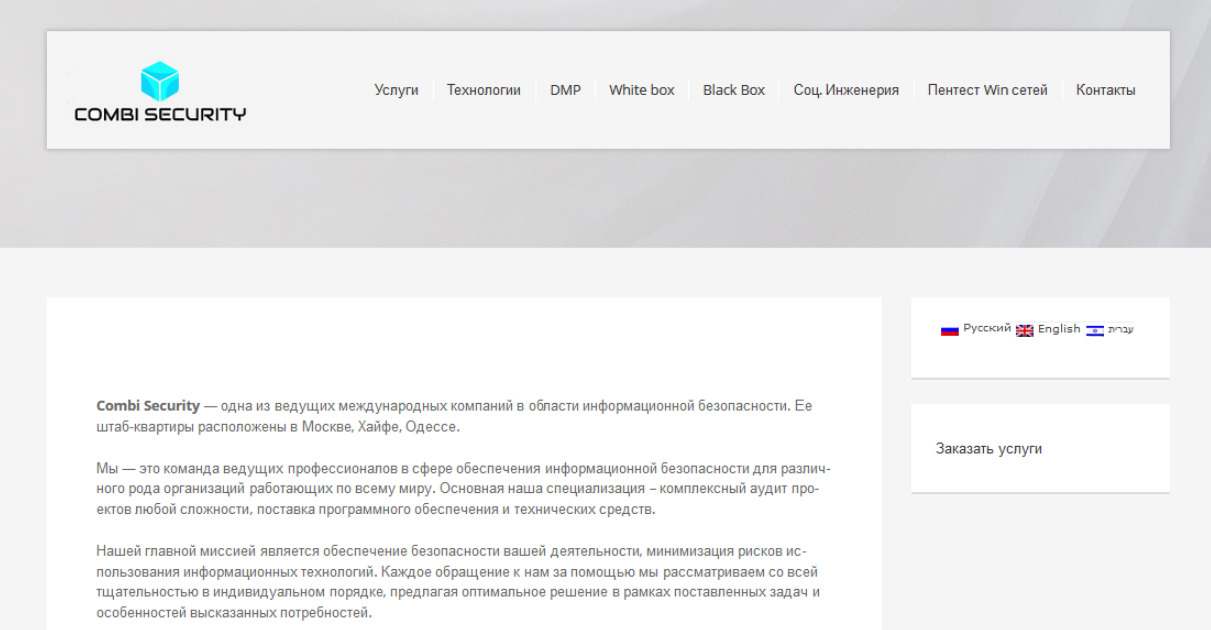
Image: The Record
Brett Callow, a ransomware expert at Emisoft that FIN7’s decision to hide behind Bastion Secure is likely to avoid unwanted attention from the law. He further said:
“It’s not at all surprising that a cybercrime operation would attempt to recruit via a fake company. Hiring from the dark web is problematic and risky. Ransomware gangs are less welcome on certain cybercrime forums than they once were, and applicants could potentially be law enforcement officers working undercover.”
According to Gemini Advisory, the reason why FIN7 went to such lengths as to create a fake company not only once but twice has to do with money and operational costs. What Callow said makes a lot of sense too, as hiring from the dark web is risky.
It is no doubt concerning as employees can be misled as to the nature of their job and will not be able to realize that they are being pen tested.
