Cybersecurity researchers have sounded the alarm on two severe authentication bypass vulnerabilities found in the open-source Wi-Fi software of Android, Linux, and ChromeOS devices. These flaws could potentially deceive users into connecting with malicious clones of legitimate networks or allow attackers to access trusted networks without needing a password.
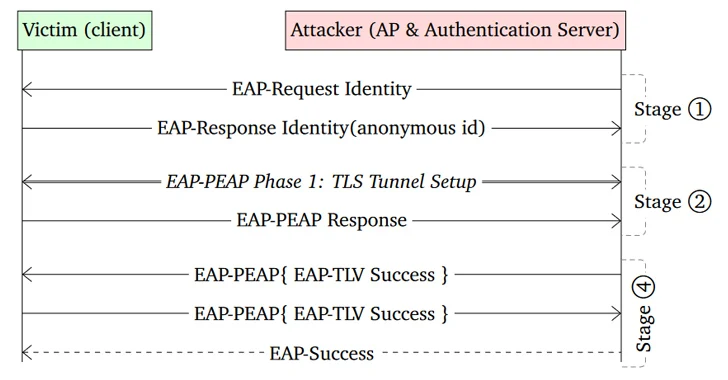
Identified as CVE-2023-52160 and CVE-2023-52161, these vulnerabilities were discovered in a thorough security assessment of wpa_supplicant and Intel’s iNet Wireless Daemon (IWD), respectively.
<strong>The flaws allow attackers to trick victims into connecting to malicious clones of trusted networks and intercept their traffic, and join otherwise secure networks without needing the password,</strong>
CVE-2023-52161 poses a significant risk by enabling unauthorized access to protected Wi-Fi networks, thus exposing users and devices to potential cyber threats such as malware infections, data theft, and business email compromise (BEC). This flaw affects IWD versions 2.12 and below.
Conversely, CVE-2023-52160, which impacts wpa_supplicant versions 2.10 and earlier, represents a more immediate concern, especially for Android users, as it is the default software for managing wireless network login requests. “This flaw only affects Wi-Fi clients that are not properly configured to verify the authentication server’s certificate,” whereas CVE-2023-52161 can affect any network utilizing a Linux device as a wireless access point (WAP).
The exploitation of CVE-2023-52160 relies on the attacker knowing the SSID of a Wi-Fi network previously connected by the victim, necessitating their physical proximity.
One possible scenario might be where an attacker walks around a company's building scanning for networks before targeting an employee leaving the office,
In response, major Linux distributions, including Debian, Red Hat, SUSE, and Ubuntu, have issued advisories addressing these vulnerabilities. ChromeOS has introduced fixes in versions 118 and later, but Android users are still waiting for a patch.
In the meantime, it's critical, therefore, that Android users manually configure the CA certificate of any saved enterprise networks to prevent the attack,
This discovery underscores the perpetual cat-and-mouse game between cybersecurity professionals and hackers. As digital threats evolve, so must our vigilance and protective measures.
Users of affected devices should take immediate steps to safeguard their data, including updating their systems and employing additional security measures such as using “Best VPN for Android” and “Best VPN for Linux” to encrypt their online activities and further shield themselves from potential cyber exploits.