Identity theft affects more than 14 million Americans annually and costs consumers over $1.7 billion. There are several methods to obtain personal information, and one of these methods is “Vishing.”
Vishing is a phone scam in which a scammer attempts to extort personal information or money from the victim. The word “vishing” is a combination of “voice” and “phishing,” which implies that a scammer is attempting to trick the victim into revealing their sensitive information such as usernames, passwords, or credit card details or download malware onto their devices.
The first stage of this attack focuses on verifying whether the phone number is still active or not. As for the second stage, the attack gets more personalized depending on the victim.
A typical vishing attempt follows a pattern:
Step 1 – Target: Scammers make calls to several people simultaneously. If someone answers, a real person comes onto the line.
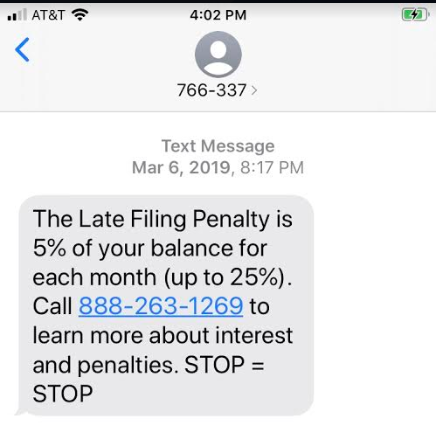
Step 2 – Information: Once the scammer is connected with a real person online, they pretend to be an authority figure like the Craigslist platform, such as a bill collector, insurance agent, the IRS, the social security administration, a computer repair technician, among others. They immediately raise an issue, such as an unpaid bill, to get their target to give up personal information. In the screenshot below, you can see a clear example of it but the method used here is called “smishing”.
Image Credit: Proof Point
Step 3 – Financial Damage: If the scammer successfully obtains the bank information, they may progress to transfer the funds out of the account. If they get their hands on credit card information, they will make as many purchases as possible before the card gets locked down.
After a successful scam, the scammer will usually disappear, never to be heard from again. Therefore, the chances of catching the culprit and prosecuting them are dubious.
Vishing scams are a severe threat, and the problem with social engineering
The reason behind the growing success of Vishing scams is the human’s ability to make mistakes. After all, it is just the ability of persuasion that is why social engineering lies at the heart of the scammer efforts. Social engineering is about mimicking a trusted authority – your bank, technology provider, the government, an IT helpdesk worker – and creating an environment of urgency or anxiety that revokes any natural feeling of caution or suspicion.
These techniques are applied in phishing emails and fake text messages (known as smishing). However, Vishers have various tools and tactics to make their scams more successful, including:
- Caller ID spoofing tools: Can be used to hide the scammer’s real location and even impersonate the phone numbers of trusted organizations.
- Multi-channel scams: Smishing text messages, phishing emails, or voicemails to encourage users to call a number.
- Social media scraping and open-source research: Provides the scammer with a stock of information on their victims.
Image Credits: WeLiveSecurity (Twitter)
The following statistics reveal why Vishing scams are considered to be lucrative businesses by attackers.
- In 2018, scam calls made up almost 30% of all incoming cellular calls.
- Proofpoint’s state of phish report released in 2020 revealed that 25% of total workers who participated in the survey could correctly define this term. Therefore, it shouldn’t be surprising to know that this term is being more widely recognized.
- 75% of scam victims confirmed that scammers already had some personal information about them. They utilize that information to target and extort more information from them.
- Out of the total Vishing scams involving government imposters reported, only 6% had lost money.
Tactics used by scammers to get victims attentions
Following are some of the tactics used by scammers to gain their victim’s attention.
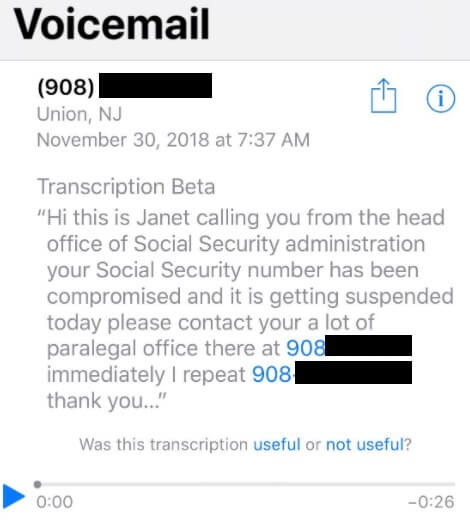
- The Social Security number has been compromised.
- The bank account has been red-flagged or hacked.
- Eligible for free COVID-19 testing or a vaccine.
- Charity requesting a donation for disaster relief or COVID-19 support.
- Credit card charge needs to be verified.
- IRS has discovered discrepancies in your tax return.
- Your vehicle is qualified for an extended warranty.
- The computer has been compromised and requires tech support services
- There is a warrant issued for your arrest.
- A friend or family member needs money to get out of trouble or was involved in an accident.
- You have won a free vacation, lottery, or giveaway.
How can voice vishing affect your family?
The ultimate goal of vishing scammers is to make off money from you. They can access your accounts by either stealing your bank account details or tricking you into handing over your personal information.
Here are a few typical scams:
Tech support scams: In these types of scams, victims are contacted by someone impersonating as their ISP or any hardware/software vendor. They’ll pretend to have found a non-existent problem with your PC and then extort payment (and your card details) to fix it, sometimes downloading malware in the process.
Wardialing: Automated voicemail messages are sent to several victims to scare them into calling back.
Telemarketing: Luring the victims into calling by claiming that they have won the lottery, vacation, or other fabulous prizes.
Phishing/smishing: Spoofed email or fake SMS, prompting the user to call a number. By calling the number, the victim will be connected with a vishing fraudster.
How to protect yourself from vishing attacks?
To decrease the chance of getting affected by vishing scams, you can follow some basic tips mentioned below:
- Make sure that your phone number is ex-directory. It means that your phone number will not appear in the telephone directory, and the telephone company will not give it to people who ask for it.
- While filling out any online form, make sure not to enter your phone number.
- Be cautious of any requests for your bank, personal, or other sensitive information over the phone. Do not hand out those details unless you are sure of the person’s authenticity at the other end.
- Do not engage or entertain any unsolicited callers, especially if they ask to confirm sensitive details.
- Better to not call back to a number left via voicemail and instead approach the organization directly.
- Use multi-factor authentication (MFA) on all online accounts.
- Ensure your email/web security is updated and start using security tools such as encrypted VPNs that include anti-phishing capabilities.