
WireGuard performs much better as compared to OpenVPN in USA. It offers reliable connections especially for mobile users because it can handle network changes better than OpenVPN. WireGuard is also easier to set up manually as compared to OpenVPN in USA. WireGuard is an excellent VPN protocol, but OpenVPN is also a great choice for privacy-conscious users.
OpenVPN has long been accepted as the industry standard tunneling protocol for VPN providers. With no other modern protocol to challenge the position of OpenVPN as the desired VPN tunnel in USA, it was easy for it to claim the top spot in terms of both security and performance among all the protocols.
Enter WireGuard, a nascent VPN tunneling protocol that promises to do everything better than the outdated PPTP, L2TP, etc. while hinting at supplanting OpenVPN in USA.
However, the question remains, which protocol works better between WireGuard vs OpenVPN in USA?
To short answer is – both protocols have their own pros and cons but WireGuard is a clear winner on account of speed, security, and audits in USA.
Without further ado, let us start comparing these VPN protocols in detail:
WireGuard vs OpenVPN in USA: Key Differences
Here is a summary of the major attributes of WireGuard vs OpenVPN in USA:
| Factors | WireGuard | OpenVPN |
|---|---|---|
| Speed | Fast | Moderate |
| Compatibility | Windows, Android, Linux, iOS | All devices |
| P2P File Sharing | Yes | Yes |
| Ease of Setup | Yes | No |
| Security | Strong | Strong |
What is WireGuard In USA?
WireGuard is an innovative VPN protocol striving hard to deliver more secure, simpler, and faster solutions to its users than prevailing protocols in USA. The protocol runs over UDP and offers a small code size of almost 3,700 lines.
Many of the key features of this protocol stem from this simplicity of code, which facilitates easy implementation, faster performance, and fewer bugs. We’ve covered the complete detail of WireGuard in USA in a separate post.
WireGuard Pros In USA
- It applies state-of-the-art cryptography to deliver secure online connections in USA
- It is relatively faster than the OpenVPN protocol in USA
- It may decrease battery consumption and enhance roaming support on mobile devices
- Uses modern cryptographic primers and has a small attack surface in USA
WireGuard Cons In USA
- It only supports UDP protocol and does not use the 443 port (HTTPS traffic port) in USA
- The protocol is considered a work-in-progress product in USA
- It only works well on Linux distributions
Which VPNs support WireGuard In USA?
There are only a handful of VPN services that have started supporting the WireGuard protocol In USA. Some of the best VPNs with WireGuard Protocol In USA are:
What is OpenVPN In USA?
OpenVPN is a VPN protocol cum software in USA that applies VPN techniques to protect point-to-point as well as site-to-site connections. Currently, OpenVPN provides the best balance of speed and security in USA. However, it is quite complex, having over 600,000 lines of code, and not easy to implement.
OpenVPN Pros In USA
- It is an established open-source VPN tunneling protocol that has the endorsement of a large number of security experts and auditors in USA
- It uses the OpenSSL encryption library and TLS as the primary cryptographic standard in USA
- The protocol delivers a decent performance in terms of speed and security in USA
OpenVPN Cons In USA
- Users may face connection issues due to strong encryption in USA
- The manual configuration of the protocol may become difficult at times on a few platforms in USA
- It needs third-party apps to run in USA
- Uses outdated cryptographic primers and has a very large attack surface in USA
Which VPNs support OpenVPN In USA?
Here are some of the best VPNs for OpenVPN protocol:
Although all of these VPNs support OpenVPN, I would suggest getting ExpressVPN. If you act fast, you can get a 49% discount. ExpressVPN is one of the best VPNs that work in Poland and many other countries.
View our latest chart comparing VPNs in 2023 in USA for more details.
Comparing WireGuard vs OpenVPN In USA
Both these protocols i.e. WireGuard and OpenVPN are free and open-sourced in USA. I will compare these protocols by focusing on the factors of performance, cryptography, ease of use, and suitability.
1. Performance
WireGuard performs much better than the OpenVPN protocol in USA.
| Factors | WireGuard | OpenVPN |
|---|---|---|
| Throughput | 1011 Mbps | 258 Mbps |
| Ping | 0.403 ms | 1.541 ms |
OpenVPN is not the best protocol out there in terms of performance. It is considerably slower than its earlier counterparts i.e. L2TP and PPTP, but this difference wasn’t really important until multi-threaded processing became practical. However, computers today are capable of supporting multi-threaded processing and higher throughput.
This is where OpenVPN is unable to keep up with the demand for faster speeds in USA because it is integrated into the user space, placing a limit on its throughput and CPU usage. WireGuard is integrated into the kernel space and is much less complex.
This allows it to be faster in USA and utilize the multi-threading capabilities of modern CPUs much more efficiently. As such, WireGuard can outperform OpenVPN in terms of pings and throughput in USA. Benchmark tests have revealed the real extent to which OpenVPN lags behind WireGuard:
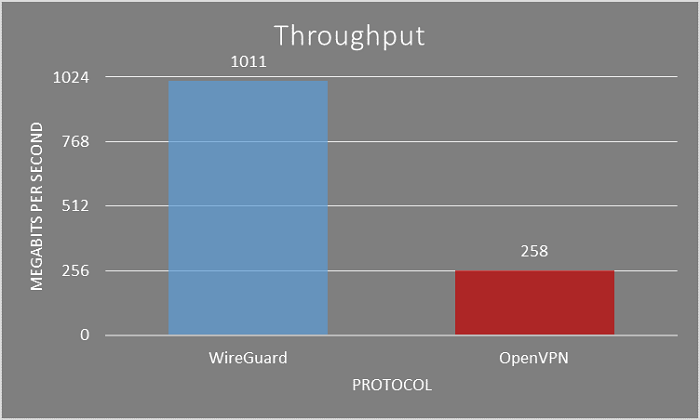
The difference is clearly outstanding in USA. Not only does WireGuard almost touches the 100% throughput of a 1Gbps connection, but it also does so without maxing out the CPU. On the other hand, a CPU running OpenVPN completely maxes out at a mere 258 Mbps in USA.
This is a testament to the superior efficiency of WireGuard. However, this is not the only metric on which WireGuard excels in USA. Take a look at the ping test below:
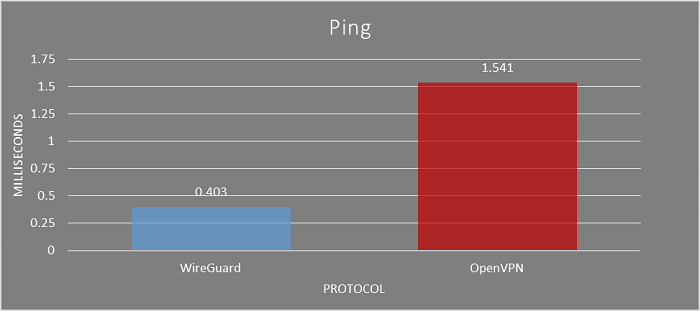
WireGuard records a ping time that is less than half of OpenVPN’s. The thing to note is that WireGuard is already producing excellent performance results even though it is still in the development phase in USA.
Therefore, WireGuard is seriously challenging OpenVPN on the performance front in USA.
2. Security
In terms of security in USA, WireGuard holds an edge over the OpenVPN protocol.
If we compare both these protocols in USA, OpenVPN uses secure encryption techniques. The OpenSSL library allows for a highly secure cryptographic primer.
Moreover, its usage of RSA and AES for data and control channels rules out the probability of brute-force attacks in USA. The maximum encryption key length that OpenVPN supports is 4096 bits. That is more than you’ll ever need. On the other hand, WireGuard supports a maximum of 256 bits of key length.
The difference is doubtless too great to be ignored. But we live in the realm of practicality and a 256-bit key length is more than enough as it is. Anything greater is simply overkilled.

As far as authentication goes, OpenVPN uses an HMAC authentication code in USA. For encryption, it uses AES and RSA. However, WireGuard uses a completely different set of encryption. These include ChaCha20, Curve25519, SipHash24, and BLAKE2s. Now comparing cryptographic primers and algorithms is by no means a simple matter.
But you can’t argue against the general rule that an algorithm is more secure the more modern it is. While OpenVPN uses strong encryption in USA, it is a little outdated. Moreover, it has a significantly larger attack surface as compared to WireGuard, owing to higher code length.
Since WireGuard uses more recent cryptographic methods that are trusted by cryptographers, it affirms its place as the more secure protocol of the two in USA.
3. Ease of Use
WireGuard is easier to set up in USA than OpenVPN manually.
OpenVPN is built on complex code with hundreds of thousands of lines. Modifying this code takes a lot of effort and time on the part of a developer. Moreover, its compatibility with certain platforms is wanting, especially on mobile phones (as iOS users might be well-aware) in USA.
In contrast, the lean code on which WireGuard is built allows for excellent usability and cross-platform compatibility in USA. Although it hosts a basic interface, it is nonetheless more powerful than any other existing protocol can offer.
Another important characteristic that lends superior usability to WireGuard is that it is a versioned protocol in USA. Compared to WireGuard, OpenVPN is a certificate-based protocol in USA.

The OpenVPN encryption can be modified based on user preference. For technical reasons in USA, this requires the use of security certificates. However, WireGuard disregards cryptographic agility, instead of focusing on versions specific to each type of encryption specifications.
This reduces overheads that result when a VPN connection is made as well as during re-connection. Since every version of WireGuard will have a specific encryption configuration, establishing a connection with servers will be twice as easy because the server would know in advance what to expect from the client in USA.
As a result, WireGuard is easy to implement and configure for different devices, rendering it considerably easy to use as compared to OpenVPN in USA.
4. Auditability
WireGuard is easily auditable in USA as compared to the OpenVPN protocol. This is the toughest attribute for this comparison in USA because OpenVPN is the most widely audited VPN protocol. OpenVPN has earned the trust of security experts and cryptographers by virtue of the various degrees of auditing it has undergone.
The protocol has been in existence in USA for 17 years now and that has given software engineers a lot of time to review, verify, and, audit it. Its open-source nature has played a great part in facilitating audits.
Although OpenVPN is the most well-audited tunneling protocol, it is also extremely complex considering how many lines of code are behind it. It takes a whole team to properly audit a code as large as OpenVPN in USA.

WireGuard, on the other hand, has not yet received the same degrees of rigorous auditing, but that is largely due to its infancy in USA. Considering the fact that WireGuard has a code that is simpler by a huge magnitude, it is many times more auditable than OpenVPN.
The code is so small that a single individual with the technical know-how can audit it independently in USA. This means that WireGuard will become the more widely audited protocol not long after its first stable version is released in USA. And with better audits comes fewer bugs, stronger security, and low vulnerability.
Despite the fact that OpenVPN is a well-audited protocol in USA, it is going to be really difficult for it to hold on to this status once WireGuard comes out. So, WireGuard takes the cake when it comes to audits, which is far superior in its case as compared to OpenVPN in USA.
Also, check our guide about comparing VPNs in USA 2023.
Wrapping Up
In comparison between WireGuard vs OpenVPN in USA, WireGuard is better than the OpenVPN protocol in terms of speed, security, and audits.
The VPN industry has benefited considerably from OpenVPN in USA, which is rightly considered the best overall tunneling protocol. But it has had its time. The flaws in OpenVPN call for an improved protocol, a call that has now been answered by WireGuard.
With excellent initial benchmark results and a highly efficient codebase in USA, WireGuard is well on its way to claiming its status as the most secure and high-performing VPN protocol when it finally sees the light of day.
Let’s hope WireGuard is able to live up to its expectations when it finally arrives and contributes towards a safer online world in the years to come. To benefit from WireGuard and OpenVPN in USA, we would recommend going for Surfshark. It is super affordable, costing only $2.49/mo - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee.

Which is better ?
Is that from a performance or privacy standpoint.
I’m sure there are more e.g. ease of installation, ease of use.
Post some I haven’t thought of, I’m curious
Mike
Hello Mike,
Thank you for reading our blog, and even more for leaving us with your generous comment.
It’s on the basis of both actually. I have compared the two on the basis of Performance (throughput), Security, Ease of use and Auditability.
You mention site to site but don’t really address whether both products support it and how they compare. Can you comment on WireGuard’s capability to support a remote user/site connecting and gaining full access to the remote network (ie. employee at home gaining access to the corporate network as if they were local)?
Hello Tucker,
For remote access, the VPN IP address should either be dedicated/static or should be allowed/whitelisted on the corporate network.
The VPN IP address can be obtained by using the WireGuard protocol.
is chacha20 as secure as aes256?
Hi Anonymous, yes, chacha20 is equivalently secure as AES-256 encryption. However, both modes of encryption are optimized for different platforms.
The fact that WireGuard uses more modern encryption algorithms does not necessarily make it more secure: one could argue the opposite, on the ground that those algorithms have yet to be subjected to the same level of scrutiny that older ones have – i.e. serious drawbacks may yet to be discovered in the newer algorithms once they have been subjected to deep and extended scrutiny.
True that Jay. We still need more time to nitpick vulnerabilities in newer algorithms.
Agree with Jay on this. Newer ≠ better …. it’s possible it is better, but only time will tell. Also, 256-bit is great, but it is much easier to hack than 4096-bit encryption.
But which one has a longer codebase?
Dear Nah,
Thanks for reaching out to us. The OpenVPN protocol has a longer codebase than WireGuard.
Cheers!!!