There is nothing new about encryption. It has a prolonged history. Ancient Roman and Greeks sent messages in secret language, only interpretable with a secret key.
In today’s modern world, the importance of encryption is more than ever and you will see its application across vast number of fields.
In order to understand what is VPN encryption and how does it work, this guide provides all the information in a simple language. Therefore, if you have little to zero knowledge related to encryption, then this guide is for you.
Table Of Contents
What is Encryption?
If you haven’t seen the movie “Imitation Game” yet, then you should watch it ASAP! It’s all about how the British M16 agency breaks the Nazi encrypted codes with the help of mathematicians in 1939.
The mathematics professor builds a team, which analyzed the encrypted messages of Nazis and then made a machine to decrypt those messages. This movie is the best way to develop an understanding about encryption process without getting bored.
But if you are looking for a quick simple answer, encryption is a process which converts the simple text into ciphertext (encrypted text) using algorithm codes and keys. Now the ciphertext is only interpretable if the receiver has the right code and key.
In this way, you are safe from hackers, as they are unable to steal your valuable data. To make it simpler, let see the pictorial example of the encryption process.

Various applications, such as WhatsApp and , use encryption process. Since it is very easy for hackers to steal your data and information, the process of encryption is the best way to protect anything communicated or store online.
What is Encryption in VPN?
When you use a VPN, the computer systems encrypt the data at each end of the tunnel. Still, a VPN requires an additional layer of security that allows it to apply encryption. In this case, the role of VPN encryption becomes crucial.
Encryption is a core component of VPNs irrespective of the you are using. The importance of encryption can be gauged from the fact that no form of VPN is ever without any mode of encryption.
Basic Concept
Have you ever heard a phrase “secret message”? You might have created that message in which you had to substitute one letter of message with another. The concept of encryption relates to secret message rule to certain extent.
Encryption Key Length
If you are using latest computer devices then you can secure your privacy through modern computer ciphers to another level. Likewise, you can measure the strength of a cipher through applied algorithm complexity hassle-free. Therefore, it becomes an impossible task for hackers to crack the ciphers if you have applied complex algorithms.
How Does VPN Encryption Work?
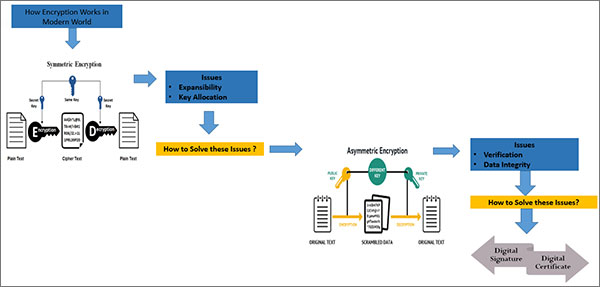
Until now, we think you get the general idea of what is encryption and why it’s a necessity. Now, it is time to explain how does it works in the modern world. For this, it is necessary to know how many types of encryption are available.
VPNs encrypt the senders’ traffic and allow the receivers to decrypt the sender’s traffic. Hence, the said end-to-end encryption secures the data to new heights and it passes through a VPN.
As the job of a VPN is to securely connect you to another server online, only the best methods of encryption can be considered so that your data wouldn’t leak. The VPNs that use the advanced encryption standard with 256-bit keys include NordVPN, Surfshark, and ExpressVPN.
The approach for encryption and decryption is based on protocols opted by the users.
Symmetric Encryption
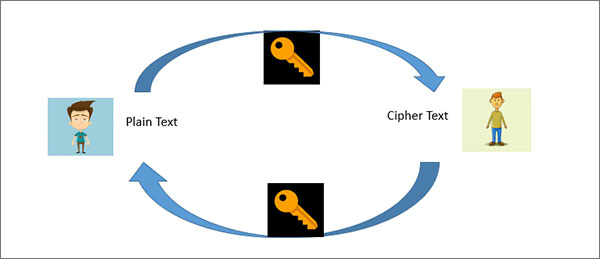
This type of encryption uses the same basic approach, it converts simple text into encrypted ciphertext by using a key. The receiver interprets the ciphertext message into simple text using the same encryption key. To make it simpler, apply this to our scenario.
When John sends the message to Mark, he coverts plain text into ciphertext with a symmetric encryption key. Now Mark gets the message, he converts the cipher text into plain text with a similar key. This way hackers cannot access the actual contents of the messages due to encryption.
The symmetric key is created per session and the same key is disabled for subsequent messages.
Issues
- Expansibility: The major issue with asymmetric encryption is expansibility. If 100 individuals were using an application to communicate with one another, all the participants would require different encryption keys to manage a safe channel.
- Key Allocation: If we suppose that both John and Mark would have symmetric key, so how do they obtain the encryption key in the first place? If John creates a key and forwards it to Mark, the hacker could attack the data if any further messaging occurs.
So, what is the solution to these issues?
Asymmetric Encryption
Although, asymmetric encryption uses the same basic encryption process similar to symmetric encryption, it uses two keys – a public key and a private key.
So, at first, the simple text is encrypted with a public key. Now the encrypted text is only interpretable (decrypted) with the related private key and the other way as well.
By using two encryption keys (public & private), users get over the issue of two symmetric keys (expansibility). But, the process of asymmetric encryption is slower than symmetric. So the developers use both together.
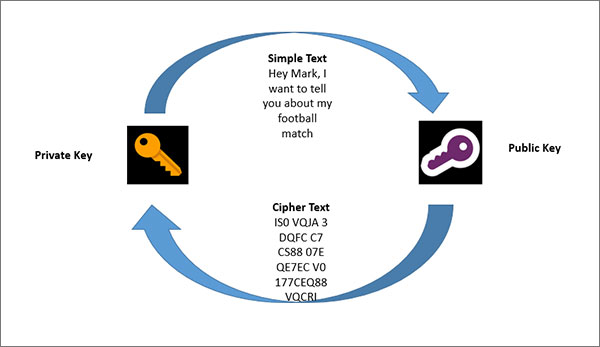
So how does the encryption process work? The public encryption key is available to every individual but the private encryption key belongs to the corresponding person only.
When John is going to text Mark, initially he produces a symmetric session key. In the next step, he encrypts it with Mark’s public encryption key. Mark obtains his own private encryption key. Now he is the only individual who can interpret (decrypt) the text.
Using this encryption process, the session key will be used to encrypt and decrypt text. The issue of key allocation is resolved without slowing the speed. This is because the asymmetric encryption process is used in beginning.
Even though this process resolves previous issues, they are not finished. It means your security and privacy might be comprised.
Issues
- Verification & Authentication: what is the surety if we are using public encryption key in the beginning? It is possible that the public key obtained can be from any hacker.
- Data Integrity: there is no way to find out that the text has customized at the time of sending process.
So what now?
Types of VPN Encryption
Luckily, you can avail your preferred type of encryption from the list of various kinds of encryption. Here is the list of VPN encryption that consists of:
- Blowfish
- 3DES
- AES-128
- IPSec
- MPPE
- Camellia
- AES-256
Blowfish
Blowfish is a pioneer VPN encryption level that uses 64-bit blocks. However, the said level of encryption does not secure larger amount of data of users. Interestingly, OpenVPN applies blowfish encryption method along with AES 256-bit military grade encryption.
3DES
3DES is one of the oldest encryption methods that allow you to secure your important data. Still, you cannot assume it as one of the most secure VPN encryption because Blowfish works faster than 3DES encryption.
AES-128
AES-128 bit encryption is much secure and faster than Blowfish and 3DES encryptions. The OpenVPN protocol also uses AES-128 bit encryption to provide protection and anonymity to its users. Furthermore, the compatibility features makes the above-described encryption an interesting choice for users.
IPSec
When it comes to attaining desired level of end-to-end encryption between sender and receiver, nothing comes close to IPSec. The L2TP (Layer 2 Tunneling Protocol) connection apply IPSec encryption. Moreover, it encrypts data on the level of IP packet to new heights.
MPPE
MPPE is referred as Microsoft Point to Point Encryption used in dial-up and PPTP connections. The said encryption level uses RSA algorithm and assists 40-bit and 128-bit session keys.
Camellia
Camellia is a brainchild of NTT and Mitsubishi. It performs quite similar like Blowfish and compatible with 128-bit, 192-bit and 256-bit keys. The OpenVPN protocol also uses Camellia encryption.
AES-256
There is no denying AES-256 has become one of the most used and secure encryption levels. Different protocols like OpenVPN, IKEv2, SSTP and others use AES-256 bit encryption level to provide next level security to users’ data.
Which is the Best VPN Encryption?
Choosing the best VPN encryption can become a daunting task for new netizens. You will have to consider different factors before selecting an appropriate type of encryption. Luckily, you have arrived at the right place. We have outlined some of the best VPN encryption types that include:
- AES-256
- AES-128
AES (Advanced Encryption Standard) has become a benchmark when it comes to exploring electronic data encryption standards. It consists of three main block ciphers like AES-128, AES-192, and AES-256. Therefore, you can assume AES-256 as the safest encryption level as it provides both anonymity and security to users.
AES-128 on the other hand is more convenient option as it does not need much resources. Still, if you do not want to compromise on your privacy, AES-256 is the right choice.
The Most Secure Type of Encryption
- AES-256 bit encryption
Encryption allows you to protect your crucial information and network connections to new heights. After exploring different encryption levels in detail, AES-256 bit encryption has all the required ingredients to be called as the most secure VPN encryption.
Why Do We Need VPN Encryption?
You cannot undermine the value of VPN encryption at any cost. It enables you to protect your different online activities from hackers. In addition, organizations use encryption methods to safeguard their confidential information.
Likewise, netizens avail different kinds of encryption levels to protect their digital identity from snoopers straightaway.
Why is Encryption Important in the Modern World?
When you use an online messaging application to communicate with your friends and family, it is important to keep your conversations private.
Without any security, when John and Mark message each other, there might be a chance that hackers and others alike could eavesdrop on what they converse.
These attackers can also customize the text you send and reroute them. In technical terms, this is known as Man in the Middle Attack. These attacks happen when the application channel passes the messages in simple text.
Because of these risk, most of communication applications and other programs use encryption to make your messages and data safe from hackers.
But in today’s high tech world, in order to make your data safe from hackers is not that easy even when you are using encryption process. For this, it is important to understand how encryption works.
VPN Encryption Protocols
A VPN encryption protocols decide how your data should pass through your computer and VPN servers. Furthermore, each VPN encryption protocol offers different specification criteria that deliver various benefits to the users.
Encryption concisely enables the receiver to decode the encrypted message in the right direction. Here is the list of VPN protocols offered by different VPN services that includes:
- PPTP
- L2TP/IPsec
- OpenVPN
- IKEv2
- SSTP
PPTP
PPTP is one of the fastest protocols but does not offer the required level of protection. However, it is compatible with all the major platforms. These platforms are Windows, Mac, Android, Linux, and iOS.
L2TP/IPsec
L2TP/IPsec is another tunneling protocol like PPTP that offers anonymity and protection both to users. Furthermore, it is compatible with operating systems like Windows, Mac, Android, and iOS.
OpenVPN
You can secure your identity and personal data through OpenVPN protocol to another level. This is because the said protocol uses 256-bit military grade encryption by default.
IKEv2
IKEv2 is another protocol like OpenVPN that offers online protection and speed under one package. Likewise, mobile users may avail this protocol to attain better performance when they are facing connectivity issues.
SSTP
SSTP is one of those protocols that provide next level compatibility to Windows platform. However, you can use it on other operating systems but its performance may vary considerably.
VPN Encryption Test
Fortunately, you can use two different approaches that allow you to check the performance of your VPN service in terms of encryption. Here is the list of VPN encryption test that consists of:
- Glasswire
- Wireshark
Glasswire
Glasswire is a freemium encryption-testing tool that allows you to check VPN encryption level in detail. Here is how you can do to achieve your mission:
- Launch Glasswire and connect it to your VPN after downloading and installing
- Download any file or watch any media content to generate traffic
- From ‘Usage’ option, chose ‘Apps’ view from submenu
- Search for ‘OpenVPN Daemon’ in the app list if you are using OpenVPN
- You should validate that active traffic type is ‘OpenVPN’
This is how you can perform VPN encryption test through Glasswire without any fuss.
WireShark
WireShark is another way of evaluating the encryption levels provided by your VPN services accordingly. It examines the actual data packets that are sent and received by your computer. In this way, WireShark offers accurate results as compared to Glasswire test results. Here is how you can do:
- Download and install WireShark and start your VPN connection
- Open WireShark and select your preferred network interface like Wi-Fi or Ethernet
- Begin recoding and search for packets labelled with OpenVPN protocol
- You should right click the OpenVPN packet and opt ‘Follow… UPP/TCP stream’
- Check the full stream to ensure it is encrypted
This is how you can perform VPN encryption through WireShark method straightaway.
How to Solve Encryption Issues?
Digital Signature and Certificates
The verification needs a reliable procedure. With the assistance of verified and reliable authority such as Certificate Authority (CA), it confirms that these public encryption key belongs to the specific individual. So, each application user verifies themselves (provides individual personal information) with CA.
Now, if John wants to text Mark, he can verify, with the assistance of CA that the public encryption key belongs to Mark. The same process is used by HTTPS on the internet. So, the issue of verification and authentication is resolved by using digital certificates.
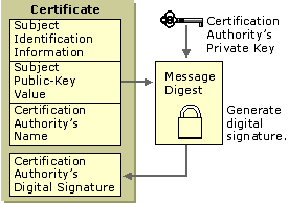
The next issue is data integrity. Digital signature resolves this problem. The procedure for solving this issue is a bit complex but we divide it into steps:
- When John wants to text Mark, he initially develops a session key and encrypts the Mark public encryption key with it. Now let’s name this Z1.
- Now he produces a hash text from available hashing algorithms. A hash text is used for one-sided communication from multiple large bytes to limited one It is impossible to get an actual text from the hash algorithm and it can never be the case that two texts have the same hash algorithm.
- Once the hash is developed, John encrypts it with his private encryption key. This process is known as a digital signature, as it provides the feature to verify the text sent by John without any customization.
- Now the actual text and digital signature is encrypted with symmetric key (session key), let’s name this Z2.
- Z1: John-Key (Public) > (Symmetric Key)
- Z2: Symmetric Key > (Text + Digital Signature)
- John sends both Z1 and Z2 to Mark. Mark is the only person who obtains the corresponding private encryption key. Therefore, only Mark can interpret (decrypt) Z1 and get the symmetric key to access Z2 (redeem the text and digital signature).
- Then Mark gets John’s key (public) to interpret the digital signature and recover the hash text. He measures hash text length and if it is same as in the initial step, it means there is no data integrity threat and the communication is secure.
Wrapping Things Up
We hope you get the deep understanding of what is VPN encryption and how does it work. The same process of encryption is used by VPN services. Top VPN services use AES 256 military-grade encryption, so in order to secure your data and information online, you can avail this kind of services.
If you have any query regarding encryption, just drop us a comment below.
