In the United Kingdom, the government’s Investigatory Powers Act and membership in the Five Eyes Alliance significantly impact user data privacy. This surveillance monitors and collects extensive amounts of data. Additionally, the UK is known for having numerous geo-restricted streaming platforms, limiting access to content based on a user’s location.
To address these concerns, I found that using the best VPN for UK is the perfect solution. The best VPN in UK protects online data from ISPs, hackers, and government agencies. Also, it provides access to geo-restricted streaming platforms like BBC iPlayer and ITV outside the UK while traveling.
In my quest for the best VPN service, I’ve personally tested over 50 VPN providers, evaluating their features, pricing structures, unlocking capabilities, and security measures, all from my base in the UK. Through this rigorous testing, I have identified ExpressVPN as the standout option. ExpressVPN provides a secure, fast, and reliable VPN service, making it the top choice for users in the UK.
However, in my testing, I discovered that other VPNs, in addition to ExpressVPN, effectively operate in the UK. These VPNs also offer a robust shield against government surveillance and overcome geo-restriction challenges. These alternative VPNs provide users with additional options to secure online activities and access restricted content.
Disclaimer: It does not encourage nor condone the use of VPNs for illegal activities, including copyright infringement.
Quick Overview – Best VPN for UK
Need a quick recommendation for the best VPN for UK? Here’s is a quick overview of the top UK VPN providers:
ExpressVPN – Overall theBest VPN for the UK in 2024:
Renowned for its superior speed, security, and extensive global server network, including numerous options in the UK. Ideal for seamless streaming and robust online privacy.
➔ Get a special ExpressVPN offer today: GB£ 5.36/mo (US$ 6.67/mo) - Save up to 49% with exclusive 1-year plans + 3 months free!
Surfshark – Budget-Friendly VPN for UK:
Offers an affordable yet powerful VPN solution with a strong presence in the UK. Known for its reliable speed, unlimited device connections, and strict no-logs policy.
➔ Get a special Surfshark offer today: GB£ 2/mo (US$ 2.49/mo) - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee!
NordVPN – Secure UK VPN with the Most Extensive Server Network:
Features a vast server network globally and in the UK, providing exceptional security with top-tier encryption and fast, reliable connections.
➔ Get a special NordVPN offer today: GB£ 3.21/mo (US$ 3.99/mo) - Save up to 63% with exclusive 2-year plan + 3 months free for a friend!
CyberGhost – Top-Tier VPN with Optimized UK Servers:
It stands out with its specially optimized servers in the UK, ensuring fast and secure access for streaming and browsing, with a focus on user privacy.
➔ Get a special CyberGhost offer today: GB£ 1.63/mo (US$ 2.03/mo) - Save up to 84% with exclusive 2-year plans + 4 months free!
Private Internet Access – Ultra-Fast VPN for Secure Torrenting in UK:
Known for its blazing-fast speeds and strong privacy measures. Offers a wide network of servers, including high-performance options in the UK, making it ideal for secure torrenting and streaming.
➔ Get a special PIA offer today: GB£1.7/mo (US$ 2.11/mo)
Detail Analysis of the Best VPN UK| FAQs
What to Look in a VPN for UK
Here are the main factors that you should look into when selecting the best VPN in UK:
| Privacy Tools | No-logs policy, independent audit |
|---|---|
| Security Protocols | Kill switch, Threat Protection |
| Tunneling Protocols | WireGuard |
| Optimized Servers | Obfuscated, RAM-only |
| Encryption Type | AES-256 |
| Unblocking Capabilities | Netflix UK, ITV, BBC iPlayer, Amazon Prime Video UK, and more |
Quick Comparison Table: Best VPN for UK 2024
Here’s a quick comparison table of the best UK VPN in 2024:
| VPNs |  |
||||
|---|---|---|---|---|---|
| Ranking for UK | 1 | 2 | 3 | 4 | 5 |
| No. of servers | 3000+ servers in 105 countries | 3200+ servers in 100 countries | 6000+ servers in 61 countries | 11651+ servers in 100 countries | 35000+ servers in 84 countries |
| UK servers Count | 25+ servers in UK | 50+ servers in UK | 440+ servers in UK | 1100+ servers in UK | 3 servers in UK |
| UK Server Locations | 4 server locations6 | 6 server locations | 4 server locations | 3 server locations | 5 server locations |
| Security | Passed | Passed | Passed | Passed | Passed |
| Average Speeds for UK | 89 Mbps | 85 Mbps | 83 Mbps | 75 Mbps | 65 Mbps |
| Multi-Logins | 8 | Unlimited | 6 | 7 | Unlimited |
| Streaming | Netflix UK, BBC iPlayer, Channel 4, ITV and More | Netflix UK, BBC iPlayer, Channel 4, ITV and More | Netflix UK, BBC iPlayer, Channel 4, ITV and More | Netflix UK, BBC iPlayer, Channel 4, ITV and More | Netflix UK, BBC iPlayer, Channel 4, ITV and More |
| Compatibility | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers |
| Price | GB£5.36/mo (US$ 6.67/mo) | GB£2/mo (US$ 2.49/mo) | GB£3.21/mo (US$ 3.99/mo) | GB£1.63/mo (US$ 2.03/mo) | GB£1.7/mo (US$ 2.11/mo) |
Best VPN for UK in 2024 [In-Depth Analysis]
Dive deep into our comprehensive analysis of the best VPN service UK providers. I examined each VPN’s server network, encryption standards, privacy policies, and ability to access popular streaming services. The in-depth reviews also include user experience, customer support quality, and pricing, ensuring you make an informed choice tailored to your needs.
1. ExpressVPN — Overall theBest VPN for the UK in 2024
- Ultra-fast servers in 105 Countries
- Excellent unblocking capability for Netflix, Hulu & more
- Best-in-class encryption trusted security, and advanced protection features that block ads, trackers, and harmful sites.
- Connect up to 8 devices simultaneously
- 24/7 customer support through live chat
- 30-day money-back guarantee
ExpressVPN to be the overall best VPN for the UK in 2024. It’s not just about the impressive speed and security; the reliability is what sets it apart. With ExpressVPN, I get a seamless online experience, whether I’m streaming or browsing in UK.
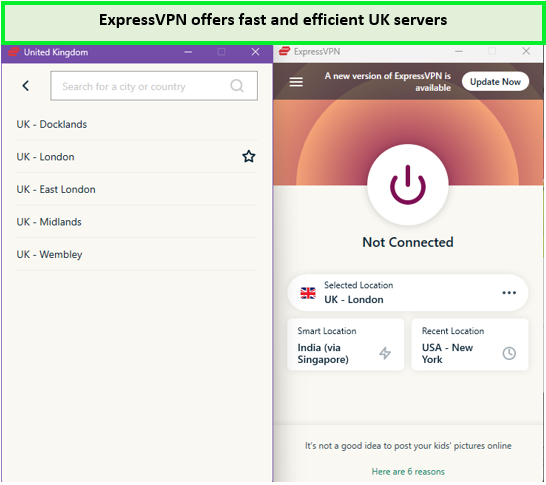
With a network boasting over 3000+ servers in 105 countries, including key locations in the UK like Docklands, Midlands, East London, Wembley, and London, it’s clear why it’s the best VPN for UK TV and other UK’s streaming platforms. This extensive network ensures I can always find a fast and reliable connection while I am streaming UK platforms. Also, the advanced server networks help use UK banking and other online services while abroad.
I am impressed with ExpressVPN’s ability to unlock a wide range of content. To test its compatibility, I connected ExpressVPN with Netflix in UK, and it worked perfectly without any buffering issues. It can also used to stream content from other platforms. You can watch ITVX, BBC iPlayer, Sky Go, or UKTV Play outside UK with ExpressVPN. The access to all of these streaming platforms is seamless with this VPN.
The fast speed and extensive server network of ExpressVPN makes it the best VPN for UK streaming for me.
The ExpressVPN speed test in the UK displayed impressive results, with download speeds of approximately 89.42 Mbps and upload speeds of 84.64 Mbps on a 100 Mbps connection. This level of performance is crucial for streaming and downloading large files.
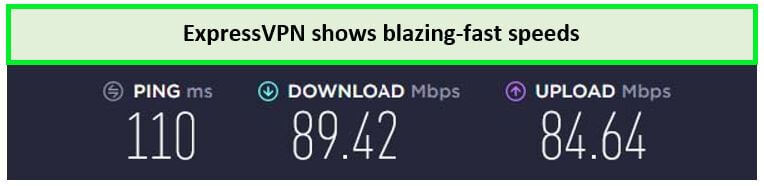
ExpressVPN London server offers the fastest speeds for streaming UK services.
The versatility of ExpressVPN extends to device compatibility. I could effortlessly set up ExpressVPN on Roku in the UK and seamlessly connect it with other operating system devices like iOS, Android, FireOS, and more. This compatibility means you can stay connected and protected on any device you use.
Security is a top priority for the VPN, and it doesn’t disappoint. The ExpressVPN Threat Manager in the UK guards against malware and unwanted trackers, enhancing my online security. Coupled with AES-256-bit encryption and a strict no-logs policy, my digital footprint remains private and secure.
Regarding costs, ExpressVPN offers value for its premium service. The ExpressVPN costs in the UK are reasonable, especially considering the quality you get. Plus, with the ExpressVPN free trial in the UK, which includes a 30-day money-back guarantee, there’s no risk in trying it out.
If you ever feel the need to change your VPN provider, canceling your ExpressVPN subscription in the UK is straightforward. But given its performance and reliability, as echoed in many ExpressVPN reviews UK, I doubt you’ll need to.
For a comprehensive look at this best VPN UK’s features and user experiences, I recommend checking out the ExpressVPN Review UK. It’s a great resource for understanding why ExpressVPN stands out as the best VPN choice for anyone in the UK.
Exclusive Deal
VPNRanks readers can enjoy a special ExpressVPN offer! GB£5.36/mo (US$ 6.67/mo) - Save up to 49% with exclusive 1-year plans + 3 months free
- Best VPN UK service for streaming platforms
- Unblocks Netflix, BBC iPlayer, Hulu, etc
- Superfast British VPN servers
- No-logs
- Bypass ISP throttling
- Slightly more expensive than its competitors
2. Surfshark — Best-Budget VPN for UK
- 3,200+ servers in 100 countries
- RAM-only servers (no hard disks)
- Unlimited simultaneous connections
- Unblocks Netflix and More
- 24/7 Customer Service
Surfshark is the best-budget VPN for UK, priced at just GB£2/mo (US$ 2.49/mo) - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee. It strikes the perfect balance between affordability and high-quality VPN service, making it an excellent choice for budget-conscious users like me.
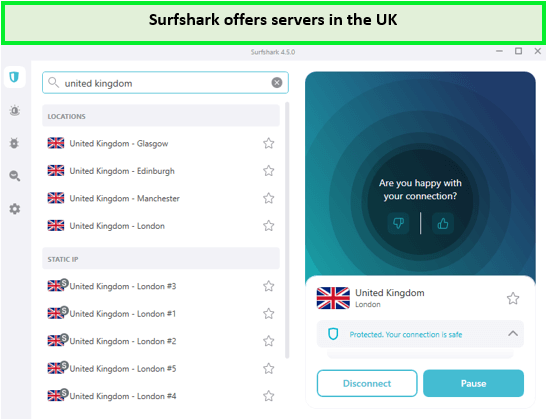
Surfshark’s network impresses with over 3200+ servers in 100 countries, including locations in London, Manchester, Edinburgh, and Glasgow. This robust server presence ensures that users can easily access global websites from the UK, all while staying within the budget.
I checked its compatibilities by unblocking the UK’s geo-restricted streaming platforms. For me, Surfshark stands out as a cost-friendly best VPN for 4Music UK and others. You can also use Surfshark Netflix UK at such a low price, which is remarkable. Not just this, you can also use Surfshark for ITVX, BBC iPlayer, etc, and explore a diverse range of content without facing geo-restrictions.
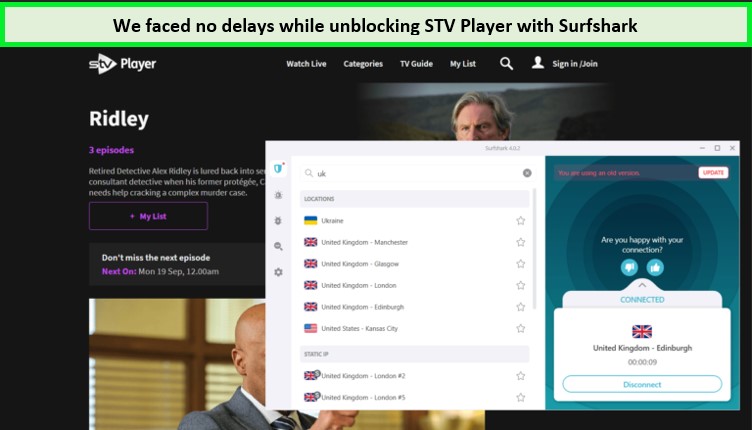
Surfshark’s Glasgow server works amazingly well with STV Players abroad.
During the Surfshark speed test in UK, I was pleasantly surprised by the results. The VPN delivered a download speed of 85.42 Mbps and an upload speed of 48.64 Mbps on a 100 Mbps connection. This performance ensures that I can enjoy HD streaming without any buffering.
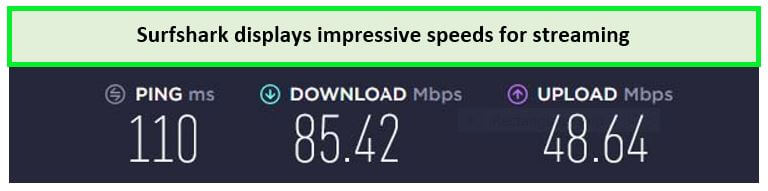
Surfshark delivered decent speeds to quickly access STV.
What enhances Surfshark’s appeal is its compatibility with a wide range of devices. I have successfully installed Surfshark on Firestick in UK, and it works seamlessly on iOS, Android, and Windows systems devices without skimping in the speed.
When it comes to security, Surfshark doesn’t cut corners. The inclusion of features like MultiHop, AES-256-bit encryption, and CleanWeb protects users’ privacy and security from troublemakers. Also, these features are particularly crucial for protecting important information from government monitoring policies.
Before paying the Surfshark cost in UK, if you are looking to explore the VPN’s features for free, then you can use the Surfshark free trial in the UK. This way, you can make an informed decision about whether Surfshark is the right VPN for you or if you should consider other options available in the UK.
Surfshark is not just a budget-friendly option; it’s a comprehensive solution for UK users. For those interested in more details, I recommend checking out the Surfshark Review UK for an in-depth analysis of its features and benefits.
Exclusive Deal
VPNRanks readers can enjoy a special Surfshark offer! GB£2/mo (US$ 2.49/mo) - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee
- British VPN that unblocks BBC iPlayer, Channel 4
- Works with Netflix, HBO, Hulu, and more
- Unlimited simultaneous connections
- Follow a strict no-logs policy
- 24/7 live chat support
- Smart DNS feature available
- No free version
- Provide limited servers than its competitor
3. NordVPN – Secure UK VPN with the Most Extensive Server Network
- 6000 servers in 60 countries
- WireGuard protocol (NordLynx)
- 6 Simultaneous Connection
- DoubleVPN
- 24/7/365 Live Chat Support
- 30 Days Money Back Guarantee
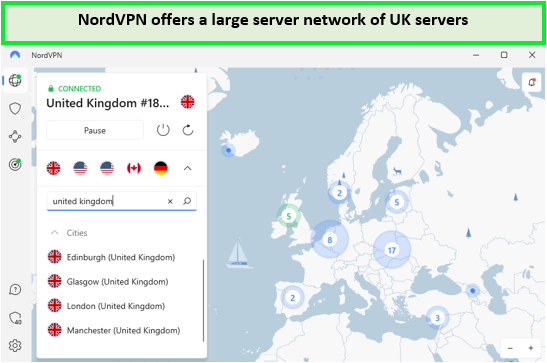
As someone who prioritizes online security, I’ve been particularly impressed with NordVPN, which I regard as the most secure UK VPN with an extensive server network. NordVPN stands out for not just its sizeable global server count, including over 440 servers in the UK, but also for its commitment to maintaining high-speed connectivity and excellent streaming capabilities.
NordVPN’s server network is truly extensive, boasting over 5500 servers in 60 countries worldwide. This expansive network ensures users have numerous options for connecting to a server that meets their specific needs, be it for streaming or security. The NordVPN server list in UK offers an impressive range of choices, solidifying its status as a VPN with one of the most extensive server networks available.
NordVPN excels in unblocking the geo-restricted streaming platforms in the UK. For instance, NordVPN with Netflix in UK allows me to dive into a wide array of Netflix libraries. Its ability to unlock content on Hulu, BBC iPlayer, and other platforms enhances my streaming experience, making it a reliable choice for accessing diverse global content from the UK. Moreover, you can effortlessly access UK streaming platforms from abroad by utilizing NordVPN’s UK servers.
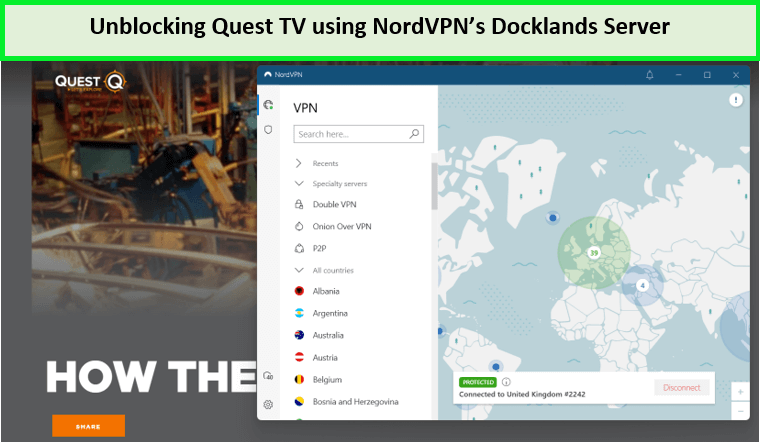
I used the NordVPN UK server to unblock Quest TV.
The performance of NordVPN impressed me during my tests. The NordVPN speed test in UK showed solid speeds, with an average download speed of 83.82 Mbps and an upload speed of 44.64 Mbps on a 100 Mbps connection. Although slightly lower than some other VPNs, these speeds are more than adequate for HD streaming.
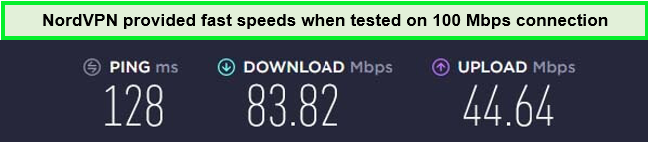
NordVPN UK servers performed incredibly well while unblocking the Netflix UK library.
NordVPN is compatible with all devices, including Roku, PS4, and others. This VPN is not limited to these devices; you can also connect NordVPN to FireStick in the UK to enjoy UK Netflix and other geo-restricted UK-based streaming platforms without issues.
NordVPN’s security features are particularly impressive. With cutting-edge technologies like NordLynx for lightning speed, a Double VPN, an Onion Over VPN, and an Automatic Kill Switch, subscribers feel confident about the confidentiality and security of their online activities. This is especially important in the UK, with its stringent surveillance laws.
NordVPN torrenting in UK is both safe and efficient. Its specialized P2P servers ensure that my file-sharing activities are secure and fast. With NordVPN, you can engage in P2P sharing without worrying about your activities being logged or monitored, which is a huge advantage given the UK’s digital landscape.
The affordability of NordVPN is another aspect that enhances its appeal in the UK market. NordVPN costs in UK are quite competitive, offering a balance between cost and quality. Additionally, the NordVPN free trial provides an excellent opportunity to test its features without any financial commitment.
For a more detailed analysis, I recommend looking at the NordVPN review in the UK. It provides comprehensive insights into why NordVPN is a leading choice for anyone in the UK looking for a secure and versatile VPN solution.
Exclusive Deal
VPNRanks readers can enjoy a special NordVPN offer! GB£ 3.21/mo (US$ 3.99/mo) - Save up to 63% with exclusive 2-year plan + 3 months free for a friend
- CyberSec (ad-blocker), Double VPN, and Onion Over VPN
- Supports 6 simultaneous connections
- Externally audited privacy policy
- Best VPN service UK for unblocking British channels, like Netflix, BBC iPlayer, Channel 4, & more
- Its desktop app takes up a lot of screen space
4. CyberGhost – Top-Tier VPN with Optimized UK Servers
- 11651 Servers Servers in 100 Countries
- 7 Simultaneous Logins
- 45 Days Money-Back Guarantee
- Strict No Logs Policy
- 24/7 Live Chat Support
- Strong Protocols & Encryption
As a frequent user of VPN services, I find CyberGhost to be a standout choice, especially for those new to VPNs. It’s a top-tier VPN with optimized UK servers, making it incredibly user-friendly. The streaming-optimized servers are a game changer, allowing easy access to global entertainment.
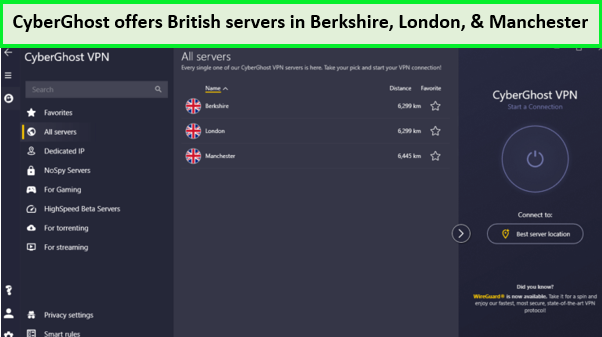
CyberGhost’s vast network, with over 11651+ server locations in 100 countries, including 781+ in the UK, ensures the user can easily bypass geo-restrictions. This expansive reach is crucial to watch Hulu in the UK and accessing a variety of other global streaming platforms.
Using CyberGhost Netflix in the UK is a smooth experience. Its servers are specifically designed for fast and reliable streaming, allowing users to enjoy their favorite shows on Netflix and other platforms like Amazon Prime Video and BBC iPlayer in high definition without any buffering issues.
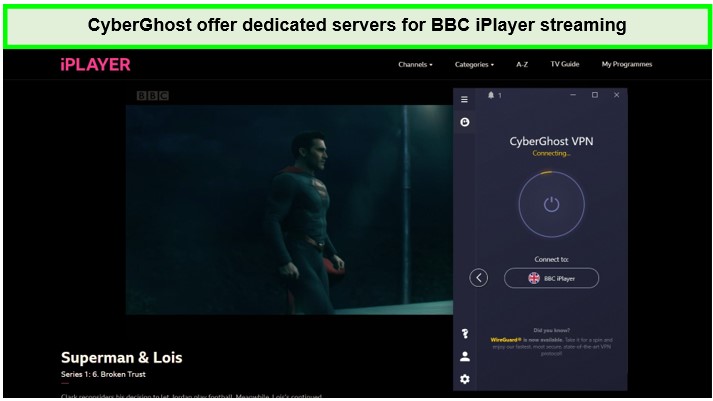
Watching Superman & Lois in Ultra HD was great with the CyberGhost BBC iPlayer server.
During CyberGhost speed test in the UK, the VPN offered a download speed of 75.47 Mbps and an upload speed of 69.34 Mbps on a 100 Mbps connection. This speed is more than sufficient for HD streaming.
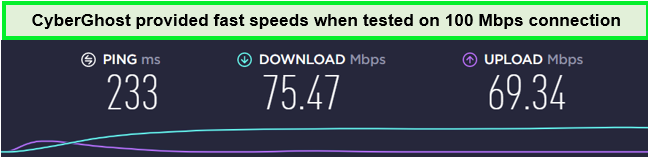
Enjoy decent streaming speed using CyberGhost’s UK servers.
CyberGhost not only excels in streaming and security but also in its compatibility with a variety of devices. It’s straightforward to set up CyberGhost on FireStick in the UK, and it works seamlessly with other operating system devices, like iOS, Android, Windows, and more.
CyberGhost’s security features, including OpenVPN, DNS leak protection, location spoofing, and a Kill Switch, provide robust online protection. This is especially important in the UK, where digital surveillance can be a concern.
CyberGhost’s free trial in UK offers a great opportunity to test its features without a commitment. This, along with its competitive pricing, makes it an attractive option for UK users.
For a more in-depth understanding of CyberGhost’s features and performance, I recommend reading the CyberGhost review in the UK. It provides valuable insights into why CyberGhost is a top choice for a VPN in the UK.
Exclusive Deal
VPNRanks readers can enjoy a special CyberGhost offer! GB£ 1.63/mo (US$ 2.03/mo) - Save up to 84% with exclusive 2-year plans + 4 months free
- British VPN with user-friendly apps
- Unblocks Netflix, Amazon Prime, Hulu
- Dedicated servers marked in the app
- Bypass government surveillance and ISP throttling
- Reliable speed
- 45-day refund policy
- Slow speeds on some servers
5. Private Internet Access — Ultra-Fast VPN for Secure Torrenting in UK
- Does Not Keep Any Logs
- 24/7 Customer Support
- 7 Days Money Back Guarantee
- 35000+ Servers in 84 Countries
- SOCKS 5 proxy
- Compatible with Leading Devices
As a dedicated user of VPN services for both security and entertainment, I’ve come to appreciate Private Internet Access (PIA) as an ultra-fast VPN for secure Torrenting in UK. It’s not just about the speed; PIA provides a sense of security that’s essential for torrenting in the UK.
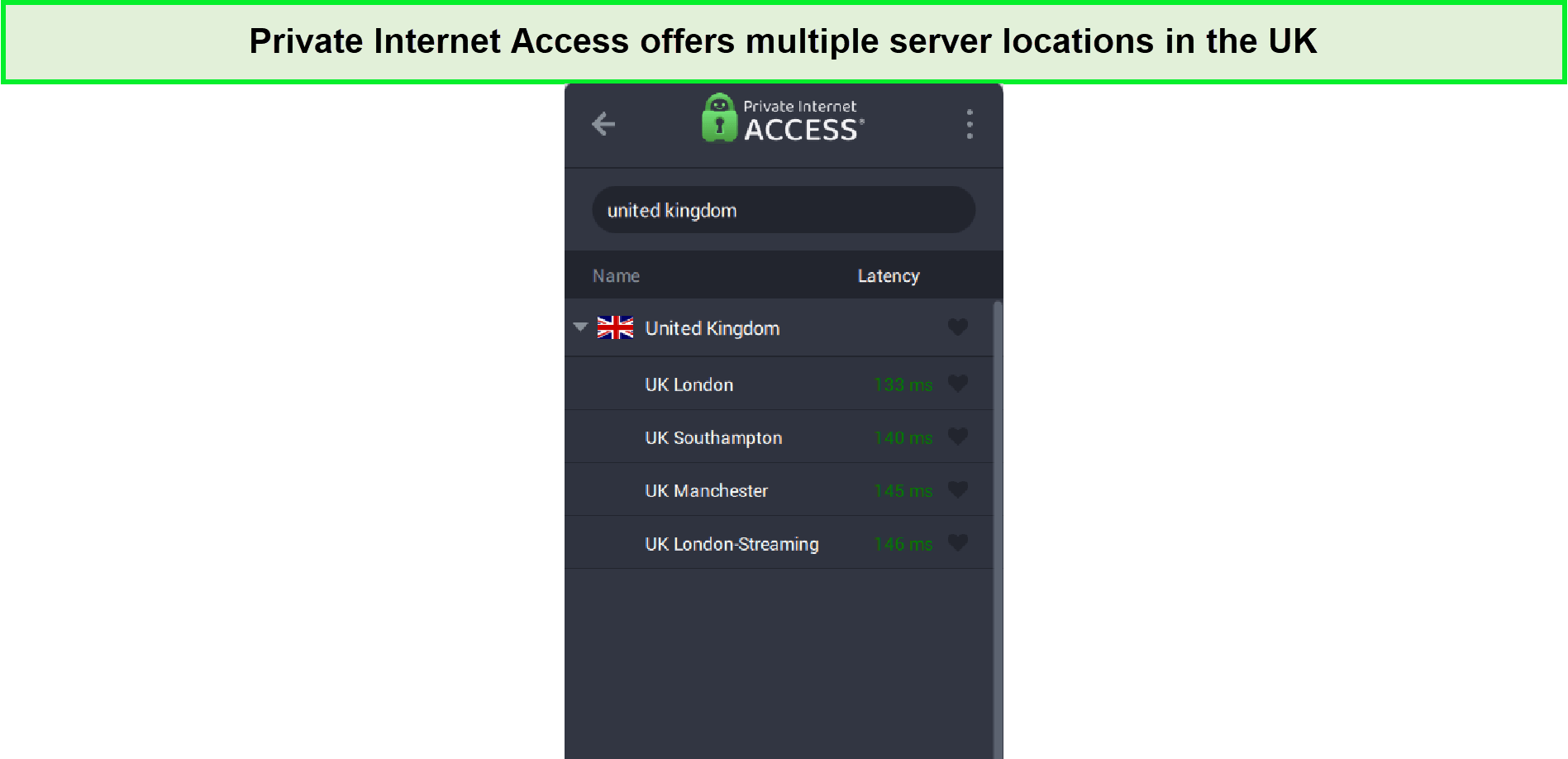
PIA’s extensive server network, with over 84 countries, including 3 server locations in UK, facilitates efficient streaming and torrenting. The servers in London, Manchester, and Southampton are useful for accessing a wide range of content without any hitches.
When it comes to streaming, PIA Netflix in the UK offers a seamless experience. I’ve enjoyed shows on Netflix, Hulu, and BBC iPlayer without any buffering issues. This makes PIA a reliable option for anyone looking to access a diverse range of streaming platforms.
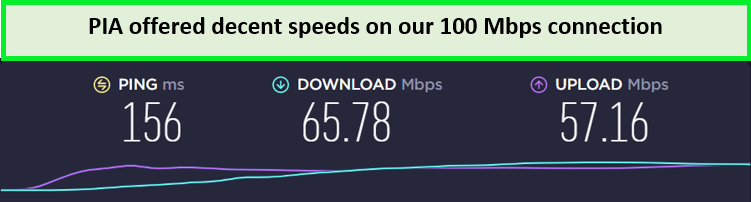
The results of the PIA speed test in the UK were quite satisfactory. With a download speed of 65.47 Mbps and an upload speed of 67.25 Mbps on a 100 Mbps connection, streaming and browsing are smooth.
PIA’s compatibility extends across various devices. Setting up PIA on routers in the UK enhances its versatility, allowing users to use it on multiple devices like Kodi and FireStick. This broad compatibility is a major plus for users with multiple devices.
Security-wise, PIA stands out with its robust protocols like Ad & malware blocking, AES-256-bit encryption, and advanced features like split tunneling, WireGuard protocol, and a kill switch. Additionally, IPv6 and WebRTC leak protection keep your activities private from UK surveillance.
PIA’s affordability is another highlight, offering competitive rates in the UK market. The PIA free trial in the UK is a great way to test the service before fully committing. This flexibility, coupled with its performance, makes PIA an excellent choice.
For a comprehensive view, the PIA review in the UK offers in-depth insights into its features and user experiences. It’s a great resource for understanding why PIA is a top-rated VPN for UK users.
Exclusive Deal
VPNRanks readers can enjoy a special PIA offer! GB£1.7/mo (US$ 2.11/mo)
- Extensive server network in the UK and abroad
- Great VPN England for torrenting
- SOCKS5 Proxy
- Offers unlimited multi-logins
- Unblocks a variety of geo-restricted content in the UK
- Inconsistent live chat support
How to Choose the Best UK VPN
To evaluate and rank the best VPNs for the UK, I conducted thorough tests on numerous VPN services, focusing on several crucial criteria:
- Privacy Policies: I meticulously reviewed each VPN’s privacy policy, ensuring they don’t log your browsing activities or IP address, with a preference for those with independently audited policies.
- UK Server Coverage: I investigated the presence of VPN servers in the UK, looking for those with a wide reach across various cities.
- Robust Security Measures: It was essential that each VPN included a reliable kill switch feature for security assurance.
- Streaming Effectiveness: Recognizing the importance of streaming, I tested VPNs for their ability to unblock popular services like Netflix UK and BBC iPlayer.
- Speed Testing: I used specialized tools to measure the performance of each VPN in terms of speed.
- Affordability: I prioritized VPNs that offer good value, ensuring affordability without compromising on quality.
This comprehensive approach helped me select VPNs that not only provide excellent service but also meet the specific needs of UK users.
Why do you Need a VPN for UK?
Using the best VPN UK is extremely important for various reasons, such as accessing global content and ensuring online privacy and security. VPNs work by encrypting your data, making it more challenging for others to track your browsing activity. This is crucial, especially when using public Wi-Fi or entering sensitive information like credit card details.
Moreover, the best UK VPN providers protect your identity by concealing your online activities and rerouting your connection to prevent tracking via your IP address. They enable access to geo-blocked content, allowing you to watch shows from different regions.
Additionally, UK VPN services can prevent ISP throttling, ensuring you get the speeds you pay for and protect against online tracking, thereby preserving your privacy and data security.
Key reasons for using the best VPNs UK include:
- Security: Encrypting data to protect browsing activities and personal information, especially on public networks.
- Privacy: Keeping searches, comments, and streaming activities private through encryption.
- Virtual Location: Allowing you to appear as browsing from another country is useful for accessing content restricted in your location, especially while traveling.
- Accessing Geo-Blocked Content: By changing your virtual location, VPNs enable you to access content from streaming services not available in your region, like US Netflix, while you’re in the UK.
- Avoiding ISP Throttling: VPNs can circumvent ISP throttling, which is especially important for uninterrupted streaming or torrenting, guaranteeing the internet speeds you pay for.
- Preventing Online Tracking: A robust UK VPN service, such as ExpressVPN, protects against ISPs and websites that track your online activities, thus preserving your privacy and data security.
Remember, while a VPN protects transmitted data, it doesn’t necessarily prevent tracking through cookies or other web trackers. It ensures secure communications but doesn’t affect application features like cookies.
How do I get a British VPN?
Getting a British VPN and acquiring a UK IP address is straightforward. Here are the steps in points:
- Choose and Register for a VPN: Opt for a reliable VPN service. I recommend ExpressVPN due to its fast speed and extensive servers.
- Download the VPN App: After registration, download the ExpressVPN app that’s compatible with your device.
- Clear Cookies and Restart Device: Clear any existing cookies to ensure a clean start, then restart your device.
- Launch the VPN App: Open the ExpressVPN app on your device.
- Connect to a UK Server: Within the app, select and connect to a server located in the UK.
- Enjoy UK IP Address: Once connected, you’ll have a UK IP address, allowing you to access British content as if you were in the UK.
Can I use a free VPN for the UK?
Yes, you can use a free VPN, but make sure that you must choose the best free VPN for UK, than it can be quite useful for accessing specific UK content and improving online privacy, particularly on public networks. Free VPNs like Windscribe and PrivadoVPN provide a cost-effective solution for secure browsing and accessing geo-restricted content.
However, it’s important to note that free VPNs often have limitations, such as data caps or restricted bandwidth, which might affect your browsing or streaming experience. They might also have fewer servers, leading to slower speeds or difficulty in accessing certain content. Additionally, some free VPNs may compromise privacy by logging user data or displaying ads.
FAQs – Best VPN for UK
What is the best VPN to change location to UK?
For changing your location to the UK, ExpressVPN stands out as a top choice. It’s known for its reliable UK servers and strong security features.
Following ExpressVPN, NordVPN is also a great option for obtaining a UK IP address. It offers numerous UK servers and is appreciated for its robust security. It also comes with a 30-day money-back guarantee. Another excellent choice is Surfshark, which provides good value for money and is an affordable alternative for securing a UK IP address.
Is there a free UK VPN?
Yes, there is a free UK VPN available. Windscribe and TunnelBear can successfully unblock various UK streaming platforms, including BBC iPlayer, making it suitable for streaming British TV.
However, it’s not as effective for accessing services like Netflix, Hulu, or Disney Plus. When connected to a UK server, these VPNs provide a British IP address, which can be quite useful for accessing content from British streaming services.
Is it worth using a VPN in the UK?
Yes, it is certainly worth using a VPN in the UK. Utilizing a VPN enhances security, especially on public Wi-Fi networks. It also helps in keeping your online activities hidden from your Internet Service Provider (ISP).
A VPN enables access to geo-restricted streaming content and can be useful for bypassing IP bans and accessing websites that are restricted or censored. These benefits make VPNs a valuable tool for both privacy and accessibility online.
Is it OK to use VPN in UK?
Yes, using a VPN in the UK is completely legal. In most countries, including the UK, the US, Canada, and much of Europe, there are no legal restrictions on VPN use. However, it’s important to note that some countries with tighter controls on their citizens’ freedoms also impose restrictions on VPN usage.
How do UK VPNs unblock Netflix?
UK VPNs unblock Netflix by allowing you to connect to a server located in the UK, or any other country where Netflix is available. By selecting the appropriate country in your VPN app and connecting to a server there, you can access the specific Netflix catalog for that region. This method effectively bypasses geographic restrictions, giving you access to a wide range of Netflix content from different countries.
Which VPN is fastest in UK?
ExpressVPN is the fastest VPN provider in the UK. With lightning-fast speeds and robust security features, it outperforms its competitors. Operating in the industry for years, ExpressVPN offers the fastest speeds with minimal throttling through its vast network of 3000+ a number of servers in 94 countries. This makes it the best choice for streaming, gaming, and P2P activities in the UK.
What is the best Cheapest VPN UK?
Surfshark, which costs less than £2 per month, is the top suggestion for the best and cheapest VPN in the UK. It not only provides excellent value for money, but it also provides a high degree of security. It is one of the best VPN services accessible, with an independently certified no-logs policy, an automated kill switch, and fast VPN connections.
Which is the best UK VPN app for mobile?
ExpressVPN is the best UK VPN app for mobile, offering excellent apps for both Android and iOS. While various VPNs are available, not all offer high-quality mobile apps. ExpressVPN’s mobile apps are quick to install, user-friendly, and allow seamless server connections and preference adjustments in just a few seconds.
Wrapping Up!
The use of the best VPN for UK is very important. They offer not only enhanced privacy and security against the strict government data monitoring policies but also open up a world of content by bypassing geographical restrictions. This makes them indispensable for both residents and travelers seeking to access a diverse range of services and websites.
The best VPN UK services operate by encrypting your internet connection and routing it through a server in a location of your choice. This process masks your IP address, making your online activities private and secure, and allows access to region-specific content seamlessly. For more information on how to access geo-restricted content and stay updated on the latest in the streaming world, visit StreamingRant.
Among the many options, ExpressVPN emerges as a standout choice for the UK. Its robust encryption, vast network of servers, including those in the UK, and consistent high-speed connections make it ideal for both streaming and security-conscious users. Its user-friendly interface and reliable customer support further solidify its position as the best VPN for UK users.