TOR (The Onion Router) keeps your online activity private by connecting to different TOR servers. It does keep you anonymous online, but it doesn’t keep your internet traffic encrypted. Your personal data might still be available to outside users. A VPN (Virtual Private Network) is the tool that not only keeps your browsing activity anonymous but also keeps your personal data intact from outsiders. That is why a VPN has an upper hand over TOR.
Both TOR and VPN are online privacy tools that hide your online traffic. If you want the best online protection, then read further as to which is better among TOR vs VPN.
Tor vs VPN: Key Differences
Here is a quick comparison of TOR and VPN:
| Factors | TOR | VPN |
|---|---|---|
| Speed | Slow | Fast |
| Compatibility | Windows, Android, Linux, iOS | All devices |
| Pricing | Free and Paid | Free and Paid |
| P2P File Sharing | No | Yes |
| Ease of Setup | Yes | Yes |
| Customer Support | No | Yes |
| Complete Anonymity | No | Yes |
| Protects online identity | Yes | Yes |
What is Tor?
Theoretically, Tor offers anonymity to its users just like a VPN service. It keeps users’ identities private over the internet. It doesn’t create an encrypted tunnel like a VPN, but it does not allow unwanted people to see users’ online activities.
When you have opted for Tor, you do not need to trust anyone else. This is because Tor makes you virtually anonymous. It would be next to impossible to recognize you over the internet.
Tor Advantages
- Tor does not accompany any price that user needs to pay in exchange – it is a FREE application
- Tor promises security by tunneling your traffic through a sophisticated network comprising divergent nodes
- Tor keeps you safe from hackers as the circuit or network formulated is tough to infiltrate
- Tor hides your IP – making you untraceable online
Tor Disadvantages
- Tor’s origin represents the efforts of US Naval Forces; therefore, it might be possible that the NSA monitors all the traffic passing through Tor’s network, and Tor may only be just another NSA’s backdoor
- Through Tor you can bypass geo-restrictions; however, not all barriers can be crossed
- Some ISPs and firewall structures such as the Great Firewall of China block requests sent via Tor relays
- Tor decelerates your Internet surfing experience because your requests transfer through a sophisticated path of nodes in a random pattern, which causes sluggishness of the process
- Tor’s circuit comprises different nodes where anyone volunteering an exit-node can access all your data and even monitor your online activities; it can be a hacker or the NSA itself.
How does Tor work?
Tor is a short form of “The Onion Router”. It is known as an “Onion” router because it is routed through several layers of online security before reaching its final destination. It protects users against “traffic analysis” that may expose your personal information including location too.
You can access the Tor network by downloading its free browser. After placing a request for information in the browser, it makes a contact with Tor server or node. Hence, the particular node forwards your request to the next node and the process continues.
As a result, you can send your request among different nodes before reaching its final point. The same process takes place when your data is passed back to you. These various “hops” enable you to keep your online identity anonymous.
It means each node knows the IP address of the previous node only. Therefore, it becomes an unattainable task for someone to identify the origin of the data. Sadly, your data resides on the exit node that makes your data highly vulnerable and insecure.
In case you are not using an HTTPS connection, chances are that online hackers can access your information.
How to Install Tor?
Step 1: First, you need to Download TOR Browser
Step 2: Run the installation
Step 3: Once the browser opens, click on the Onion icon at the top of the browser
Step 4: This would Turn ON the browser. Click again to Turn OFF.
What is a VPN?
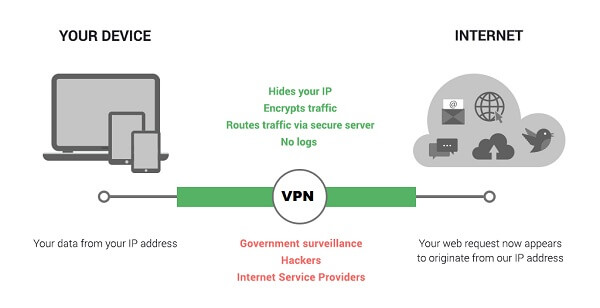
A VPN is an online privacy tool that hides your internet traffic through an encrypted tunnel and assigns you an alternate IP address. As a result, you are able to encrypt your online communication and all that you do over the internet. In simple words, users get the IP address of a VPN server that allows them to encrypt the connection between a VPN server and a user’s device.
You can use a VPN by simply downloading the app that can be used on multiple platforms such as Windows, Mac, Android, iOS, router, and more. Simply connect to one of many different VPN servers and start browsing the internet safely. If you want to know what is a VPN then explore our detailed guide.
VPN Advantages
- By using a VPN, you can bypass any geo-restriction and access any content you desire
- Your identity is protected with a VPN as it masks your real IP and makes you completely anonymous
- While being connected through a VPN, no one can trace your location through your IP address
- A VPN tunnels your data through a secure network – making it impossible for hackers or even the NSA to infiltrate your security
- A VPN is formulated through different protocols such as PPTP, L2TP/IPSec, SSTP, SSL and SSH etc
- The encryption supported by these protocols protects serves as a backup plan
- If someone somehow was able to penetrate into your security, he will get nothing but encrypted data only
Check out some best VPNs for Tor.
VPN Disadvantages
- A VPN comes with a price to pay
- You will have to purchase the service eventually from the service provider if you wish to continue
- A VPN deteriorates your Internet speed to a certain portion. Hence, your surfing experience can be a bit lethargic if you do not have a high-speed Internet connection
- Security and Internet speed are inversely proportional while using a VPN
- A VPN encrypts your data by using different protocols
- The most secure protocol selected while connecting a VPN can cost you a significant decline with respect to the Internet speed
How VPN works
A VPN hides your online activity by securing your data through a tunnel that remains encrypted via 256-bit encryption. Once you open a VPN app and connect to a US server, a VPN will assign you a US IP address. Your command to access any website will be first accessed by the US server and then your actual destination website.
How to Configure/Install a VPN?
Step 1: First, you need to subscribe to a good VPN such as ExpressVPN.
Step 2: Download and Install the ExpressVPN app for your device.
Step 3: Open the app.
Step 4: Enter Username and Password.
Step 5: Connect to any country server (for e.g. US server).
Step 6: You will be assigned a new US IP address upon connection.
Step 7: Now all your data remains safe and secure.
TOR Over VPN
TOR over VPN is used when you need to hide your internet traffic from your VPN provider. If you don’t trust your VPN service and you think it keeps logs, then you could use a TOR browser over a VPN. There’s a good chance that your personal information will remain hidden from ISPs and your VPN company.
How to Setup TOR over VPN
- Open VPN app on your device
- Connect to any server
- Now open TOR
- Click Connect and it establishes a connection
- Start browsing the internet safely.
VPN Over TOR
A VPN is used over TOR when you need to protect your internet traffic from malicious viruses that could emerge from exit nodes. TOR is vulnerable from its exit node that can be abused to monitor TOR traffic. It is also used to prevent your ISP from seeing your VPN traffic and also to unblock geographically restricted content.
How to Setup VPN over TOR
- First, connect to a VPN service so that your home network doesn’t flag you for using TOR
- You can connect to any VPN server
- Once connected, open the Tor browser
- Now press the Onion icon and start browsing the internet
VPN or Tor: Which one is better for privacy?
Both services would keep you anonymous over the internet, but since TOR is too slow it cannot be used for file sharing, streaming, or downloading torrents. For that purpose, you will need a VPN to do your job. VPN services have fast speed and keep your online identity secure. If ever you want to make a decision between TOR vs VPN, always go for VPN.

There is a way to use VPN and Tor together.The double protection of VPN Plus Tor provides the highest level of anonymity. In the case of a theoretical compromise of the Tor, you will be additionally protected by the threshold of VPN.
Yes, John. You’re absolutely right. That is exactly what I have explained in the above guide.