A virtual private network is a service that can help you connect to the internet securely in USA by routing all of your network traffic securely through encrypted servers. A VPN essentially hides your IP address in USA providing anonymity and privacy from hackers and snoopers. That’s essentially what traditional VPNs do.
SSL VPNs, on the other hand, are basically a subset of traditional virtual private networks. Secure Sockets Layer VPNs basically allow you to securely access services and application remotely in a convenient way via your web browser without having to download any additional desktop software.
That being said, finding SSL VPNs compared to other Reliable VPNs in USA is not easy.
So now that you know what an SSL VPN is, we’ll go over some of the best SSL VPN in USA you can get in 2023. So without further ado, let’s get started.
Best SSL VPN In USA in 2023
Essentially, finding best SSL VPN in USA is not an easy test. There are countless options available online. But which one should you get? Well, to make it easy for you, I’ve come up with a list of some of the best SSL VPNs in USA currently available in the market.
- Barracuda SSL VPN
- Cisco IOS SSL VPN
- Juniper Networks SA Series SSL VPN
- Citrix Gateway
- Pulse Connect Secure
How SSL VPN Works In USA?
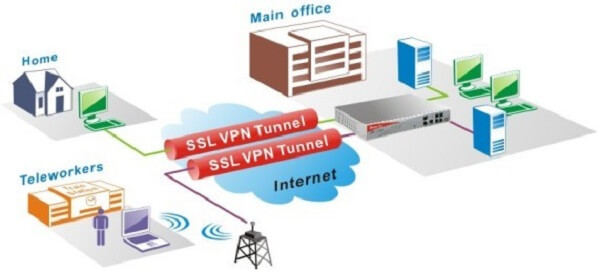
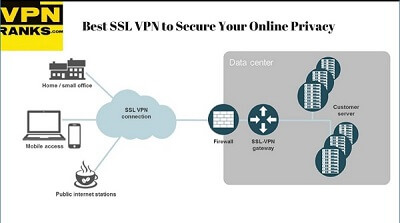
An SSL VPN works differently when compared to other VPN services in USA. It routes your information with the help of a secured tunnel. Moreover, it encrypts the data to enhance the protection level of the data.
Furthermore, the users do not have to install SSL VPN on their devices in USA. All they have to do is to use a standard web browser. By doing so, they can use this type of VPN according to their own terms.
SSL VPN Described
SSL (Secure Socket Layer) is a cryptographic protocol, designed to promote online freedom and secure our online interaction. Just like the preceding protocols you know of, SSL tunnels all the information you send via a secure network in order to boost data safety and security. SSL VPN is a virtual private network created by using the SSL protocol. There is not much difference between a virtual private network created by using SSL or any other protocol ( or /IPSec etc); but, the security level of a network created by using SSL in USA is much more sophisticated and invulnerable to breach.
All the data tunneled through a virtual private network is encrypted; but, we all know about this security measure – don’t we? SSL VPN upgrades this aspect as well. SSL VPN upgrades this security aspect as it uses X.509 certificates to facilitate data encryption which takes data security to a whole new level. Furthermore, SSL VPN allows you to establish remote-access network connections.
L2TP (Layer-to-Tunneling Protocol) is one of the most frequently used protocols by security concerned VPN users these days. Without a doubt, L2TP provides excellent security with up to 256bit encryption in USA facilitated through IPSec. However, some VPN providers would want to install their client software if you wish to create a VPN facilitated through L2TP (Layer-to-Tunneling Protocol).
This, however, is not the case with SSL VPN. Unlike other security protocols, SSL doesn’t require the installation of any client software. With an ordinary web browser, you can avail of every benefit associated with SSL VPN in USA.
A virtual private network created by using SSL protocol can correspond to single or multiple devices that can be accessed simply by using a standard web browser. There are two main types of SSL VPNs that can fulfill your security needs in USA.
Classification of SSL VPN In USA
Now that you know what an SSL VPN is and how it works, let’s go through the main classification of SSL VPNs in USA.
SSL Portal VPN
SSL Portal VPN is one of the networks formed through the Secure Socket Layer. Through this virtual private network, multiple network services can be accessed by a user though it allows a single Secure Socket Layer connection. The name portal VPN quite fits this kind of network because it works just like a single doorway that opens to many directions. This network provides remote access via the use of a standard web browser. However, as per the security precautions, a user in USA needs to go through a sophisticated identity verification process prior to accessing the gateway.
SSL Tunnel VPN
SSL Tunnel VPN is another form of a network formed via Secure Socket Layer that not only enables users to access several network services through a standard web browser but also other protocols and applications that are not web-based. The process is facilitated through a tunnel formed using a Secure Socket Layer that carries data requests securely from one end to another of the tunnel.
SSL Tunnel VPN is preferred by some users in USA; because, SSL Portal VPN doesn’t allow some functions to be accessed. SSL Tunnel VPN using a standard web browser in USA enables users to handle active content such as Flash applications, Active X, Java, JavaScript, and plug-ins, etc. Users don’t get such liberties from SSL Portal VPN.
Advantages of SSL VPN In USA
There are different advantages associated with best SSL VPN in USA. The network formed by using Secure Socket Layer (SSL) provides unbeatable security and invulnerability to unauthorized assaults. It protects your precious data from the cyber-goons at every corner of this digital universe. Furthermore, through SSL, you can form a protected network between remote users along with other internal resources. In addition, this network can be accessed remotely via a standard browser.
The network formed through SSL provides much more sophisticated security than traditional encryption protocols such as L2TP/IPSec. Furthermore, you don’t need client software to configure the SSL VPN. Perhaps, due to this reason, a network formed through SSL is also called Clientless or Web VPN.
You don’t download additional files or fulfill complex requirements to create a network through SSL. Unlike preceding security protocols such as L2TP/IPSec, SSL only requires an updated browser to establish a secure network. Furthermore, A best SSL VPN in USA liberates its users in USA to choose any web browser they prefer without putting on any restriction or obligation with respect to the operating system.
Disadvantages of SSL VPN In USA
Despite all the unbeatable benefits associated with SSL VPN, it also has a few vulnerabilities in USA. Irrespective of its security measures, the SSL network is vulnerable to spreading Spyware in USA, Malware, Trojans, Worms, and Viruses, etc. SSL networks can be remotely accessed by users, hence, any remote user having a device with unequipped with necessary security instruments can spread the malicious files from the local networks to an organization’s network. Therefore, it is strongly recommended to have an updated antivirus installed on your device if you wish to access the network.
SSL VPN’s split tunneling in USA can also be exploited by hackers and cyber-goons. When any user with remote access to the network shares network traffic simultaneously with public and private networks, he presents an opportunity to hackers and cyber-goons for an assault. Hackers can execute their assaults by targeting that particular user and using him as an intermediary in the attack. Host-based firewalls serve as an optimal remedy in this regard.
There are other disadvantages associated with SSL VPN in USA as well such as lack of host security software installed on public devices, physical access concerns, and keystroke logging issues. A SSL VPN can lead to a leak of sensitive information from endpoints. Furthermore, SSL networks can also be victimized through man-in-the-middle hacking assaults. While establishing a network through SSL, strong user authentication may be required, and meeting the standards of all other sophisticated security policies can be a hassle sometimes.
What is Secure Shell (SSH)?
The users in USA may assume Secure Shell a network protocol as Secure Socket Shell (SSL). The protocol offers the users a secure route by which they can access to the remote computer. In addition, it gives effective authentication and encrypted data communications between two computers.
As a result, the users can connect two computer systems on an unprotected network like the internet in a secure manner.
What is Transport Layer Security (TLS)?
Transport Layer Security (TLS) is another crucial security protocol that describes a procedure about privacy and data integrity. You can opt for the said security protocol in the web browser and other applications too.
Advanced Features of SSL VPN In USA
What makes an SSL VPN distinct from other online privacy services in USA is the availability of advanced features. Here is the list of various advanced features you can avail through a best SSL VPN in USA. The list consists of:
- Endpoint Security Compliance
The said feature needs a system to abide by some pre-defined rules. Otherwise, the users in USA will not be able to log in through the system. These rules include Windows configuration, file scanning, and antivirus updates.
- Source IP/Date/Time Restrictions
This benefit refrains users in USA from accessing particular websites in specific locations during the designated time slots.
- Cache Cleaning
The users in USA can keep their cache clean through the help of the cache cleaning feature.
- Virtual Sandbox User Environment
The said feature allows the subscribers in USA to avail of the automatic configuration benefit hassle-free. Thus, the users are able to secure their devices against unofficial or illegal access to their files and apps. Moreover, the virtual sandbox user feature removes the temporary files by default once a user logs out.
Wrapping Things Up
SSL VPN without a doubt is one of the most secure networks in USA with sophisticated safety measures. Unlike the predecessors like L2TP/IPSec VPN in USA, SSL VPN ensures maximum security with diverse additional benefits. You do not need client software to establish a network using SSL.
Nevertheless, despite all the benefits offered by a best SSL VPN in USA, there are some serious loopholes that need to be considered. SSL VPN’s strong feature is its security; ironically, this feature becomes its crucial weakness if mandatory requirements are not fulfilled or suitable precautions are not taken. In short, SSL VPN with all requirements fulfilled and all tools installed forms a network with unbeatable security.
