
WireGuard is the newest free and open-source tunneling technology in the world of Best VPN services.
It might come as a bit of a surprise to you, but the VPN industry hasn’t seen an upgrade in tunneling protocols since almost two decades ago.
This came in 2001 in the form of the open-source OpenVPN, which is a well-established protocol trusted by experts in the industry.
But WireGuard is all set to challenge the status of OpenVPN as the best VPN protocol in USA, addressing some of the issues endemic to it.
In this blog, I will explain as simply as possible what WireGuard is and how we can expect it to affect the VPN industry in USA.
WireGuard – A Game Changer in USA?
I can almost hear you asking “Is it really necessary to further complicate tunneling protocols with the release of yet another”?
That is a perfectly valid question. After all, WireGuard is just another protocol in the already long list that includes OpenVPN, L2TP, SSTP, PPTP, and IKEv2. These are the protocols that I commonly encounter when I am performing VPN reviews in USA.
So, what can WireGuard possibly offer in USA that these protocols can’t?
Let’s look at some of the most prominent attributes that differentiate this new protocol from the ones we are more familiar with in USA.
1. Simplicity
If there is one quality to define WireGuard by, it’s simplicity. And I mean it in more ways than one.
First off, WireGuard is much simpler than OpenVPN because it is leaner in terms of its code.
The more common VPN protocols i.e. OpenVPN and L2TP take up some 600,000 and 400,000 lines of code respectively.
In contrast, WireGuard takes up less than 4,000 lines of code!
That is a game-changing level of difference.

Smaller code has important advantages. For instance, the chances of things going wrong and bugs affecting functionality are much lower when your codebase is so small to begin with.
Moreover, the attack surface or how exposed to security threats a code is depends on the size of the code. The longer it is, the more vulnerable it will be to attacks.
So, lean code is advantageous from the security standpoint as well.
Finally, it is much easier and less time-consuming to audit code with fewer lines than one that is bulked up with thousands of lines more.
Tl;dr, simpler code means:
- The protocol is more likely to function smoothly with minimal hiccups in USA
- It is more secure because there are fewer vulnerabilities to exploit
- It can be audited by a single individual with less than half the time required to audit other protocols
It’s amazing how simplicity can improve so much at a single stroke. And that is the hallmark of WireGuard in USA.
2. Easy Implementation
The easy implementation of WireGuard stems from the fact that it is a versioned protocol.
That is, its upgrades will be released in the form of updated versions, each containing a single encryption specification unique from other versions.
In contrast, OpenVPN can change its cryptographic algorithms and ciphers at the request of the administrator.
This means there is no agreed upon standard between the client and the server for an OpenVPN user.
As such, it takes longer to form a connection as OpenVPN has to negotiate certain handshake and encryption standards with the server side every time a user connects.
On the other hand, a single WireGuard version will use a single specification, so the server can immediately recognize everything it needs to know about the encryption and other standards being used.
This speeds up the whole connection process, which is something that no other protocol has been able to do.
3. Faster Performance
WireGuard promises to offer significantly higher performance and speeds as compared to other protocols in USA.
This is courtesy of the fact that it operates in the kernel space which has a high speed-to-CPU usage ratio.
That is to say, you get more speed for a given level of CPU usage when compared to IPSec or OpenVPN.
WireGuard actually benchmarked throughput and ping times for WireGuard, OpenVPN, and two different variants of IPSec.
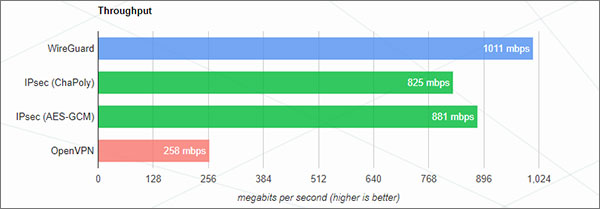
The graph shows the CPU maxing out at 258 Mbps, while WireGuard almost completely reaches the 1 Gbps rate of the Ethernet connection. This is a 98.7% throughput!
You can clearly observe the difference between all tested VPN protocols. The best thing about WireGuard is that the CPU usage didn’t max out even at the impressive throughput recorded.
Considering the fact that it is still under development and is not yet an optimized protocol, these results are incredibly impressive.
The same benchmark also tested the ping times of WireGuard as well as the other three protocols.
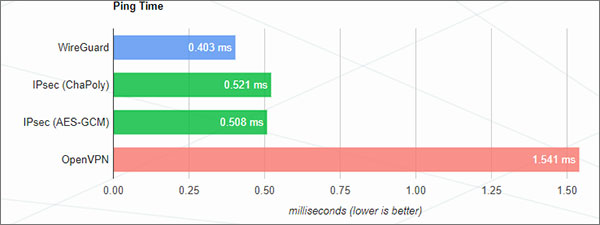
Once again, WireGuard bested the other protocols, the difference being the most prominent.
These results speak for themselves and are a glimpse into the power and overall performance of WireGuard in USA.
4. Secure Encryption
WireGuard goes against the grain in its use of encryption standards and algorithms as well. Most protocols use strong but outdated encryption algorithms to secure the VPN tunnel in USA.
WireGuard uses encryption algorithms that no other existing protocol support. These are:
- ChaCha20 (authenticated by Poly13045)
- BLAKE2s (hashing and keyed hashing)
- Curve25519 (ECDH)
- HKDF (key derivation)
- SipHash24 (hashtable keys)
However, the key length for encryption is limited to 256 bits. This may be concerning for some people, but let’s be real, 256-bit encryption is already an overkill.
This becomes evident when you realize that a 256 bit encryption length means 1.15 x 1077 different possible key combinations. The chances that some guy will randomly guess your correct key is 1 in 1.15 x 1077.
You are more likely to witness a scrambled egg unscramble itself than get your encryption keys guessed correctly.
What about brute-force attacks, though?

Assuming that you perform a brute force attack with a very fast computer and are lucky enough to land upon the correct key after exhausting half of the key combinations, you’ll still have to try 5.75 x 10^76 different keys.
If you generate 100,000,000 keys per second (which is far above the average capability of existing computer systems), you’ll have to wait 1.82 x 1061 years before you find the right key.

Except that the entire universe would be dead by then, not just you
So, key length is a factor that has importance only up to a point. After that, it becomes irrelevant, such as in the case of key lengths bigger than 256 bits.
The real question is the algorithmic strength and efficiency of the encryption that WireGuard uses.
Until security weaknesses are discovered in the encryption algorithms of WireGuard, there is no cause for alarm solely because it is limited to shorter key lengths.
Wireguard is up there with Mosh in terms of not leaking the network semantics into the user experience: I've had a Mosh session and a Wireguard tunnel open to my home server for days from home, to plane WiFi, to Italian tethering.
Other software, be more like Wireguard and Mosh.
— Filippo Valsorda @filippo.abyssdomain.expert (@FiloSottile) December 29, 2018
The fact that WireGuard has withstood the scrutiny of security auditors and cryptographers (which is still ongoing) is encouraging for anyone having doubts about the protocol’s security.
In fact, it is only going to be better than its counterparts, since it is using more recently developed cryptographic primers.
Therefore, from the security standpoint, WireGuard is way ahead of older VPN protocols in USA.
The Flipside
Okay, so we’ve seen all the important ways in which WireGuard is ready to pounce on existing tunneling protocols.
But let’s peek under the carpet and see some of the potential problems within WireGuard in USA.
A Work in Progress
WireGuard is a free open-source project that is still under development. No official stable releases have come out yet.
In its current form, you can’t really rely on this protocol, as they are likely to contain security vulnerabilities.

WireGuard Status: Under development
Don’t forget that the protocol has not yet been subjected to proper security auditing. All that is still a work in progress in USA.
While we know enough to be reasonably confident in the capabilities of WireGuard when it is officially released with a stable build that time is still some ways in the future.
No Windows Support Yet
The entire development of WireGuard is being conducted on Linux. Although its experimental versions are out there for macOS, Android, and iOS, no Windows client has officially been released yet.
However, some VPN services, as I will discuss below, are offering a windows app through third-party clients.
The developer of WireGuard, Jason Donenfeld, strongly advises against the use of supposed Windows clients:

So, heed this warning, guys. We will be getting Windows support soon, but not just yet.
Possible Problems with Certain Features
The VPN service Perfect Privacy published an article about WireGuard a few months ago where they mentioned that this protocol will not be able to support certain features such as NeuroRouting and TrackStop.
However, such problems won’t necessarily persist once the completed version of WireGuard is released. We may also expect variants of the protocol that will function better with certain VPN features.
Logging Issues
One of the main issues that stole my attention one raised by some VPN providers concerning the inability of WireGuard to be used without logging user information in USA.
If these concerns are valid, the desirability of WireGuard as a VPN protocol would be seriously under doubt.
According to AzireVPN:
… when it comes to WireGuard the default behaviour is to have endpoint and allowed-ip visible in the server interface, which does not really work with our privacy policy. We shouldn’t know about your source IP and cannot accept having it visible on our servers.
However, these guys were able to get over the logging problem with help from the creator of WireGuard code himself, Jason. He basically wrote a modified rootkit-like module that solved the problem.
Perfect Privacy also pointed towards the same logging problem. AirVPN, on the other hand, has shown interest in WireGuard, but also stated that they won’t be including it in their service until a stable, peer-reviewed, and well-audited release of the protocol has developed.

The common theme in all of these statements and concerns centers around the fact that the protocol is by no means a finished product.
But considering that some of the issues are already being addressed and the fact that the code is still experimental at this point, most of the highlighted problems will likely be resolved in due time as development of the protocol further progresses.
Future Implications
Despite the fact that WireGuard is still an experimental project, it is already turning out to be an exceedingly promising protocol in USA for a number of important reasons which include speed and security.
The initial benchmarking tests are definitely remarkable enough to attract the attention of VPN providers and users in USA.
Whether the finished product will be able to live up to the hype is a different question. But if the existing audits, third-party verification, and performance tests are anything to go by, the odds are aligned in the favor of WireGuard.
Currently, users in USA should stay away from the use of this protocol. It is pretty much only of interest to developers in its existing experimental form.
However, a stable release is not as far away from seeing the light of day as we might assume. It is very much possible that we’ll be seeing a WireGuard v1.0 in the next few months.
So, based on all we’ve discussed in this article, here is what we can expect when this protocol finally gets an official release:
- Easy implementation
- Fewer bugs
- Fast performance
- Low connection times
- High functionality
- Strong security
- Excellent cross-platform compatibility
VPN Providers with WideGuard Support in USA
Although Donenfeld has repeatedly warned that using this protocol can be dangerous and expose users to security threats, some provides are still offering WireGuard protocol in their VPN packages in USA.
At the time of this writing, these providers are:
- Mullvad
- IVPN
- AzireVPN
- Algo VPN
These could be of interest to you if you are a developer. Otherwise, I’d suggest you to show a little patience and wait until a tested and reviewed official release of WireGuard is here.
What experts are saying about WireGuard in USA
Ever since the project went underway, WireGuard has received considerable praise and admiration from coders and software engineers in USA.
Linus Torvalds, the creator of the Linux kernel, had this to say about it:
Btw, on an unrelated issue: I see that Jason actually made the pull
request to have wireguard included in the kernel.Can I just once again state my love for it and hope it gets merged
soon? Maybe the code isn’t perfect, but I’ve skimmed it, and compared
to the horrors that are OpenVPN and IPSec, it’s a work of art.
Greg Kroah-Hartman also didn’t conceal his excitement form the developing protocol, stating:
It’s been great to see Wireguard mature over the years into something that works really well. This past week it survived the LinuxCon/ELCE/Kernel Summit traffic thanks to Konstantin Ryabitsev and packet.net setting up a server for us to use…Hopefully after the networking conference next week there will be a clearer roadmap for merging it into the kernel tree. The crypto code in the kernel module will probably have to play nicer with the in-kernel crypto apis, which is to be expected, but really, the current in-kernel crypto apis do need a serious revamp one of these days, no wonder Jason wrote his own interface.
Even US Senator Ron Wyden weighed in by writing a letter to NIST (National Institute of Standards and Technology) recommending the adoption of WireGuard for government VPNs.
Recently, a new open-source VPN technology called Wireguard has gained prominence. To ensure security, its design emphasizes simple setup and minimizes the number of available options. Notably, Wireguard is now being incorporated into the Linux operating system, a clear signal of its widespread support in the technology and security industries…
… I urge NIST to work with stakeholders to evaluate appropriate security replacements, including Wireguard, for government use.
The Head of Privacy from Private Internet Access regularly contributes on Reddit. You can find him giving his expert opinion on VPN related subreddits.
In the following comment, he endorses WireGuard as a great idea, but also warned users from using it while it is still in the experimental phase:
Comment
byu/somethingtosay2333 from discussion
inVPN
WireGuard has turned enough heads to convince me that Donenfeld is up to something that’s simply incredible. I mean if US Senators are taking interest, it has got to be REALLY secure in USA.
Final Thoughts
WireGuard is surely shaking up things in the VPN industry, promising of modern cryptographic techniques, secure tunneling, excellent auditability, and smooth performance.
Some of the biggest names in the world of software development are extremely optimistic about this innovative VPN protocol.
But at the same time, a few VPN companies have raised a few concerns relating to logging issues and compatibility with certain proprietary features.
Although these concerns cannot be ignored, they are a little premature considering that there is a lot of work still remaining before WireGuard makes its appearance as a fully developed, reviewed, and audited protocol in USA.
And when that happens, we just might witness the start of new era of secure networking in USA.

Your claim that ALGO is a vpn provider is incorrect.
At the time of this writing, these providers are:
Mullvad
IVPN
AzireVPN
Algo VPN
Algo is a vpn protocol.
Regards,
Hello Unc Buk,
Algo VPN is not a protocol of its own. Rather, it simplifies the configuration of WireGuard and IKEv2.
Here’s the Github description of the program (copy-pasted):
“Algo VPN is a set of Ansible scripts that simplify the setup of a personal IPSEC and Wireguard VPN. It uses the most secure defaults available, works with common cloud providers, and does not require client software on most devices. See our release announcement for more information.”