How would you like your package to be delivered by the courier service? Do you want it to be delivered quickly or do you want it to be properly packed and safely delivered, even if takes longer than usual? In the world of VPN, those questions are answered by the data tunneling protocols.
While a wide variety of VPN protocols are available for commercial and individual users, the PPTP VPN type remains popular on account of increased functionality.
Let’s check out what PPTP is good for and what are some of the apparent flaws of the ever so popular PPTP VPN protocol.
What is PPTP?
PPTP is a VPN protocol that stands for Point to Point Tunneling Protocol. It had been the first VPN protocol to be introduced in Windows, which was first available for Windows 95. It is amongst the easiest VPN protocol to set up, and much easier to use.
PPTP is useful when you need a faster internet connection for streaming that works well with limited processors. However, PPTP has security vulnerabilities because it has weak VPN encryption of 128-bit. Its underlying authentication protocol i.e. MS-CHAP-v1/v2 is insecure.
Most VPN providers today offer protocols far superior to PPTP.
Point to Point VPN is available by default in Microsoft Windows, but also available for Linux and MAC OS X. While connected to a VPN, all your internet data flows under a VPN tunnel in the following two steps:
- When you launch the PPTP client, it then connects to the internet provider
- After, it creates a TCP control connection that is between the PPTP VPN client and the VPN server. With the help of TCP port 1723, it established a tunnel
The inherent weakness of the PPTP VPN protocol can ultimately lead to a VPN leak.
The Good Old Days
Many members of Generation Y will remember the days when the modem was at the heart of the internet connection as it controlled data transfer between the client and the remote server.
The Remote Access Service (RAS) protocol came forth to allow functionality over telephone lines. Do you remember the funny noises the modem used to make before establishing the connection? “eeen-aaan-kading-kadung……”
The first RAS protocol was the Serial Line Internet Protocol (SLIP). SLIP supported the initial network protocols (TCP/IP) but quickly became obsolete when the dawn of advanced protocols (IPX/SPX) demanded the development of the Point-to-Point Protocol, or PPTP as they are most commonly known.
What Is A PPTP VPN And What Makes It So Popular?
Even though newer VPN protocols like OpenVPN, L2TP, or IPsec may offer much better network security, PPTP still among the most popular and widely used network protocols out there.
The reason why this protocol is so popular is because of its speeds and ease of use.
That said, even though PPTP is quite fast, easy to set up, and compatible with a wide selection of desktop and mobile operating systems, it has some well-known vulnerabilities.
But despite that, it is still one of the most popular VPN protocols in the industry.
Here’s why…
- PPTP has been around for more than two decades.
- The configuration is dead simple.
- Different levels of encryption for every application.
- Fast performance is perfect for streaming.
- PPTP is compatible with Windows, Linux, Mac OS, iOS, Android, Tomato, and other operating systems.
Advantages & Disadvantages of PPTP VPN?
So we know that PPTP is super-fast but does have few known vulnerabilities. Let’s look at some of the major advantages and disadvantages of the PPTP VPN protocol.
Advantages
- Due to comparatively less encryption, PPTP is one of the fastest VPN protocols around.
- Thanks to the minimalistic setup process, anyone with a bit of technical knowledge can easily configure the PPTP VPN protocol.
- Since PPTP is compatible with all the latest operating systems, PPTP connection can be established on tons of platforms.
Disadvantages
- PPTP protocol is not as secure and known to have security vulnerabilities. In fact, the Five Eyes backed NSA has actually been able to crack the encryption of PPTP traffic.
- Due to less rigorous encryption, PPTP connections are prone to malicious attacks.
- PPTP is infamous for being blocked quite easily by firewalls.
- PPTP cannot be recommended for privacy-conscious folks.
Let’s break it down, PPTP is good for what?
Enough chit chat, let me tell you exactly why you should be using the PPTP VPN protocol…
Smooth uninterrupted data transmission
Since the PPTP protocol uses the General Routing Encapsulation (GRE) and TCP PPTP VPN port number 1723, data travels smoothly without any interruptions.
Offers decent encryption
By utilizing 128-bit encryption, PPTP does actually offer decent privacy.
Fast speeds
With low-level 128-bit encryption, the PPTP protocol offers leg speeds compared to other protocols.
The Roots of the Point-to-Point Tunneling Protocol
Dating back to the 1980s, the Point-to-Point Protocol (PPP) served as a bridge between the physical link at the user’s end and the Internet Protocol.
Responsible for establishing a two-way point-to-point connection, the PPP was popular for its simplicity and effectiveness. This was the first protocol to achieve formal recognition as a VPN protocol.
Subsequent developments in internet technology changed all that sooner than anticipated. The need for more security and faster data transmission led to the development of the Point-to-Point Tunneling Protocol. (Remember, tunneling begins with the encapsulation of data at the source, followed by the routing of encapsulated data packets and concludes with the decapsulation of data at the destination)
The All-Time Favorite – Point-to-Point Tunneling Protocol
The Point-to-Point Tunneling Protocol (PPTP) goes one step ahead of its predecessor, PPP, by establishing a virtual tunnel for an even safer transmission of encapsulated data packets.
Even though PPTP has native support from Windows, it is widely used on Mac and Linux platforms because of its speed and compatibility.
The PPTP borrows authentication protocols from the PPP and often comes under fire for being far too traditional and vulnerable if used without encryption.
PPTP VPN Protocol & Encryption – Hand in Hand
If used without encryption, publicly available services such as CloudCracker and browser add-ons like Firesheep can easily crack PPTP connections by using network sniffers (fish-net programs designed to capture low-level data packets).
Once your key has been extracted, the task of accessing all your data traffic transmitted across the network is as stealing candy from a baby.
Get a PPTP VPN that guarantees 256-bit encryption so you can stay secure!
For more information regarding PPTP and OpenVPN protocol. Read our blog.
Is PPTP still a Secure VPN protocol?
PPTP VPN security, is it still secure?
Now I’m not going to beat around the bush here. PPTP is no longer as secure as it used to be in the past.
Since the protocol hasn’t been updated to counter the latest security vulnerabilities, there are plenty of loopholes within the PPTP protocol that can be exploited.
Here are some of the known vulnerabilities of the PPTP protocol…
MS-CHAP-V1 vulnerability
Thanks to the MS-CHAP-V1 vulnerability, specifically designed tools can easily bypass the security mechanisms of PPTP and get a hold of the NT Password hashes from MS-CHAP-V1 authentication traffic.
MS-CHAP-V2 Is Not Safe Either
Even though PPTP can substitute the MS-CHAP-V1 with MS-CHAP-V2 for authentication, it is still not secure. In fact, MS-CHAP-v2 was also found to be vulnerable to dictionary attacks.
Known To have Been Exploited by the NSA
Due to weaker encryption, there is plenty of evidence available that the NSA has been successfully able to crack PPTP traffic. Even the five eyes have been speculated to maliciously weaken the encryption of the PPTP VPN protocol.
MPPE RC4 Stream Cipher Vulnerability
The RC4 stream cipher used by MPPE can easily be compromised by hackers with the help of bit-flipping technique.
Since there is no mechanism in place to authenticate the ciphertext stream, malicious hackers can easily decrypt the ciphertext.
Is PPTP Even Fast?
Long story short, yes! Since PPTP uses low-level encryption, it is quite lightweight and unburdened.
Unlike OpenVPN which does typically slow down your internet connection, PPTP is capable of offering fast connection speeds.
This is exactly why people prefer using PPTP for online streaming and gaming when both PPTP VPN vs OpenVPN are compared.
How to setup PPTP VPN on Windows 10
Step 1: Click on the Network icon.
Step 2: Now select Network and Internet Settings > Then select VPN on the left-side menu
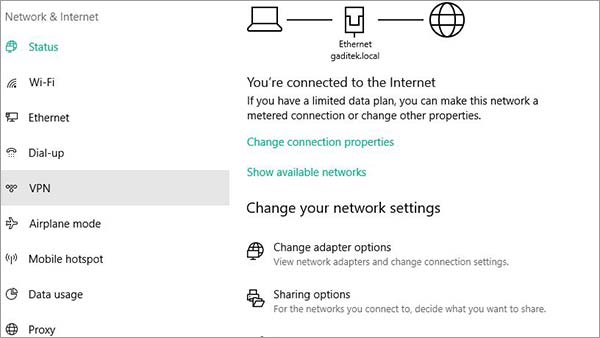
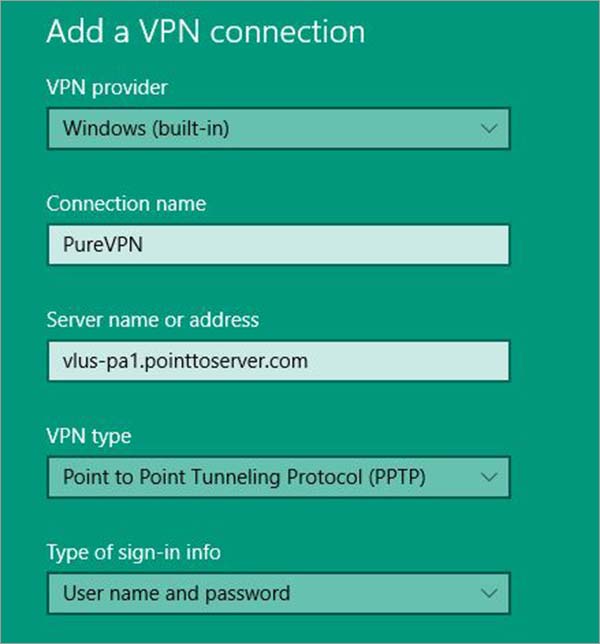
Step 3: Tap on Add a VPN Connection > Now enter the VPN Details.
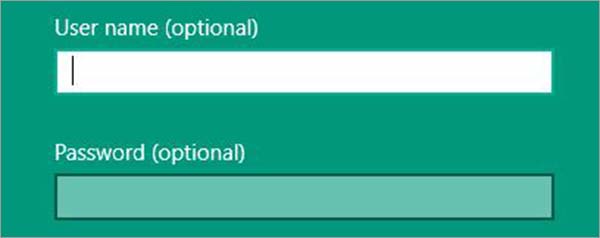
Step 4: Enter the Username and Password.
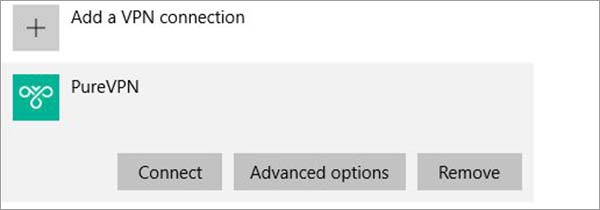
Step 5: Hit Connect
10 – Step Method to Use Free PPTP VPN on Your Computer?
So now that you have a bunch of free PPTP servers to fiddle around with, let me tell you how you can configure one on your very own Windows computer.
Note: The screenshots below might vary depending on what OS version of Windows you might have.
Let’s get started…
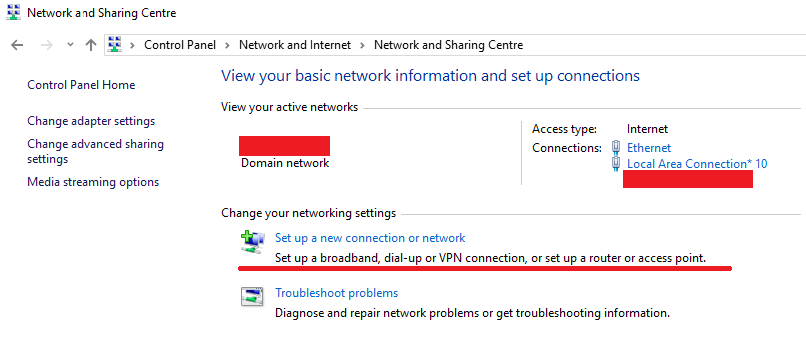
- First things first, open up the control panel on your computer and search for Network and Sharing Center.
- Next, click on the option that says, “Set up a new connection or network”.

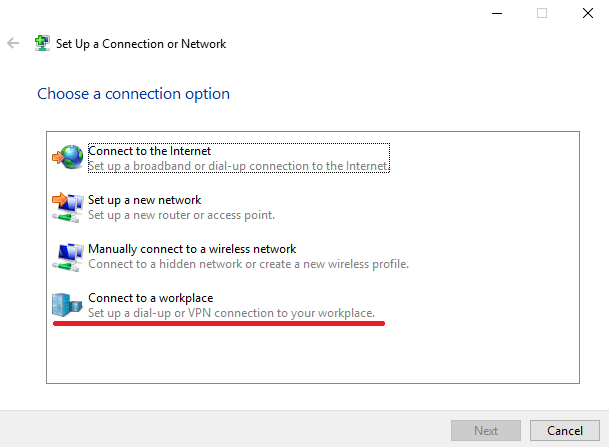
- Now you should see a new popup window with four options. From here, select the “Connect to a workplace” option to configure the PPTP protocol.

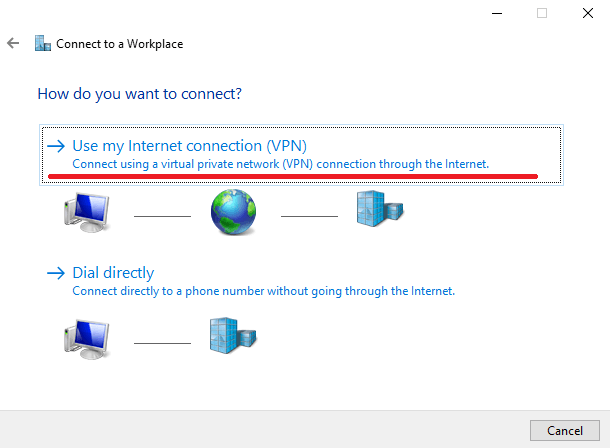
- Once you click next, you’ll have two options. You need to select the “Use my Internet Connection (VPN)” option to proceed.

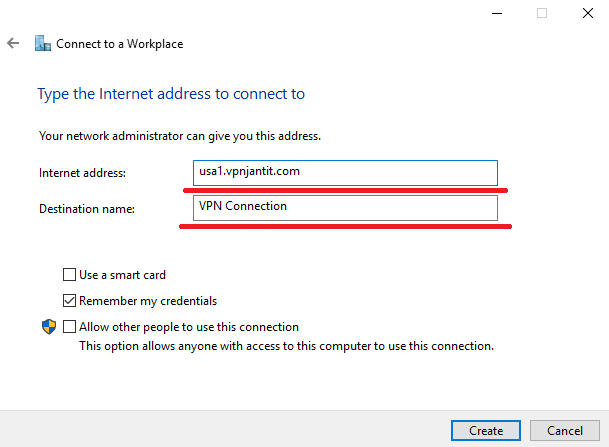
- Now within the new popup window, enter any server address from the list mentioned above in the Internet address You can choose any name for the Destination name.

- Now that you’ve successfully created a VPN connection, it’s time to tweak around some settings. To do that, head over to Control Panel > Network and Internet > Network Connections and access the properties of the VPN you just created by right-clicking it.

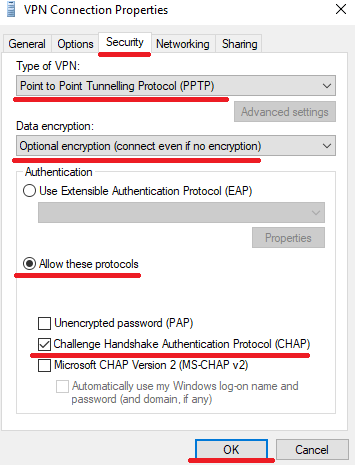
- Now within the properties menu, select the Security tab and tweak the settings as shown in the screenshot below.

- Once you’re done with the setting, save everything and return back to the Network Connections page, double click the VPN connection you just created, and click connect.

That’s it, you’ve successfully created and configured a free PPTP enabled VPN connection.
Not Cut Out For PPTP Configuration? Try an Easier Alternative
Messing around with settings can be quite frustrating, especially when you don’t have much technical knowledge.
If you don’t want to devil with manual PPTP configuration, you can always resort to easier alternatives. By that I mean just go for premium VPNs that offer plenty of customization and configuration.
Best of all, premium VPN providers don’t only offer a superb service, but also guarantee world-class customer support to enhance your VPN experience.
That’s something you’re surely going to miss if you decide to stick to manual VPN configurations.
When choosing your VPN protocol, make sure you begin by identifying your VPN use. To play it safe, make sure you pick a VPN provider that guarantees you access to the PPTP protocol.
Most VPN providers will limit protocol access depending on the pricing package you purchase. We recommend finding a VPN service provider that gives all-around protocol access regardless of the pricing plan. Here is the list of the best PPTP VPN providers.
| VPN Providers | Price ($) | Special Deals | More Info |
|---|---|---|---|
|
Overall Best VPN

ExpressVPN
|
$12.95
$6.67
Per Month |
Exclusive Offer
Save 49% today! |
|
|
Fastest VPN Service

Surfshark
|
$12.95
$2.49
Per Month |
82% Off
2 Year Plan |
|
|
Best for Geo-Unblocking

NordVPN
|
$11.95
$3.99
Per Month |
69% Off
2 Year Plan |
|
|
Feature-rich VPN

PureVPN
|
$10.95
$3.29
Per Month |
81% Off
Exclusive 2 Year Offer |
|
|
Best for Private Browsing

CyberGhost
|
$12.99
$2.03
Per Month |
83% Off
3 Years + 4 Months Free |
PPTP VPN Configuration on Multiple Devices
As I said earlier, premium VPN services support a lot of customization.
Instead of going through tons of settings or resorting to manual configurations, premium VPN services such as ExpressVPN, make it painstakingly easy to switch VPN protocols.
Here’s how simple it is to switch to the PPTP VPN protocol with ExpressVPN.
PPTP VPN Windows 10 and below
To switch to the PPTP VPN protocol in ExpressVPN, all you need to do is click on the menu (≡) button located at the top left corner and then click on Options.
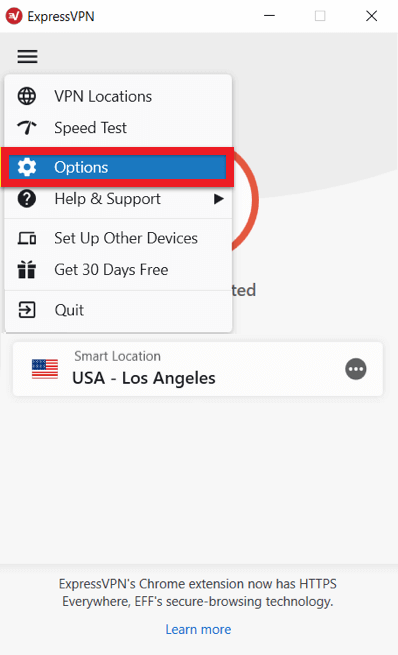
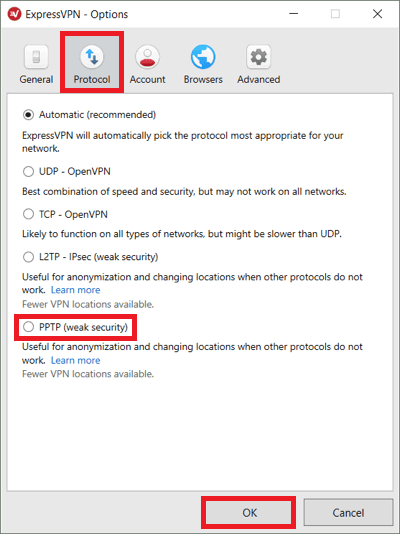
Now when the new window pops up, click on the Protocol tab, enable PPTP VPN server and click ok. That’s how easy it is to set up a Windows PPTP VPN.
Mac PPTP VPN
PPTP VPN Mac – it is just as easy as the Windows method I showed you earlier.
Simply head on over the menu (≡) button located at the top left corner and then click on Preferences.
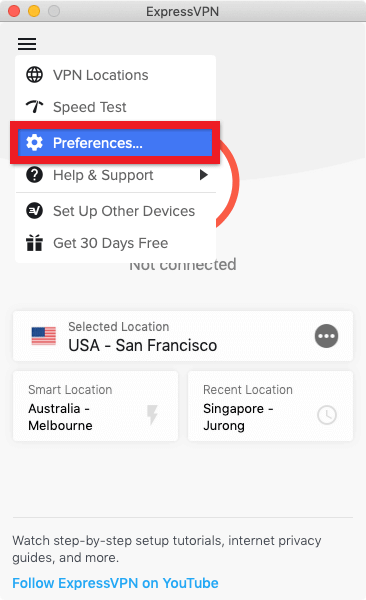
Now in the preferences window, simply click on the Protocol tab and select the L2TP-IPsec radio button.
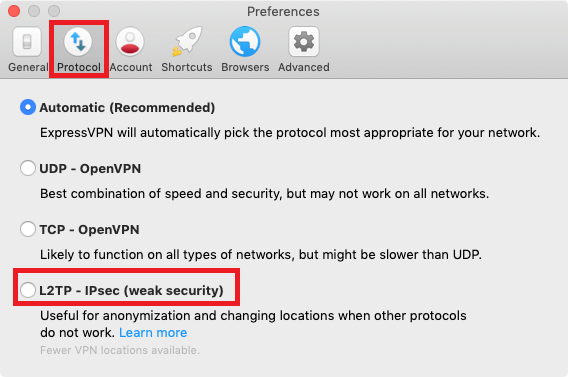
The reason why I told you to select the L2TP-IPsec protocol is that the Mac client of ExpressVPN doesn’t offer the PPTP protocol.
And since both L2TP-IPsec and PPTP offer similar security benefits, they can be substituted for one or the other.
That said, if you’re looking for a free PPTP VPN client for Mac, I suggest you refer to the free PPTP VPN list I’ve mentioned below.
PPTP VPN Android
Now let’s check out how to switch to the PPTP VPN protocol on the Android app of ExpressVPN.
Just like I showed you earlier, head over to the menu (≡) button located at the top left corner and tap on settings.
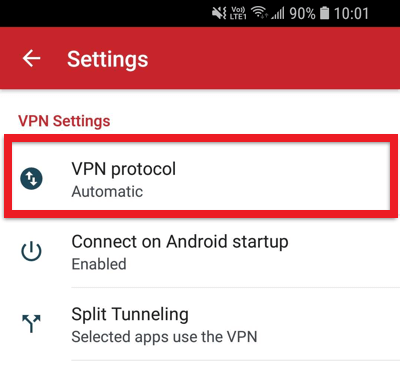
Now under VPN settings, tap on VPN protocol, and chose any protocol you desire.
IOS – iPhone PPTP VPN
Switching protocols on the iOS platform are essentially similar to the Android method I showed you earlier.
To set up PPTP VPN on iOS, simply head on over to the menu bar > settings > VPN protocol and then choose any protocol of your choice.
Don’t Feel Like Spending Money? Use My Free PPTP VPN Server List
Now I know not everyone wants to spend money on VPNs. Even though I recommend only using paid VPN subscriptions, I’m still sharing a list of free PPTP VPN servers you can use.
Now I went through quite a bit of trouble to come up with this list. I’d appreciate it if you would at least share this blog with your friend.
Shameful plugging aside, the list below includes PPTP VPN servers from Singapore, the USA, Canada, UK, and few other countries.
Enjoy….
Note: it’s still better to go for paid VPN services rather than gambling your luck with a free PPTP VPN server
| Server | Username | Password | Country |
|---|---|---|---|
| sg1.vpnjantit.com | vpnjantit.com | i0ryj | Singapore |
| sg2.vpnjantit.com | vpnjantit.com | i0ryj | Singapore |
| sg3.vpnjantit.com | vpnjantit.com | i0ryj | Singapore |
| usa1.vpnjantit.com | vpnjantit.com | i0ryj | USA |
| fr1.vpnbook.com | vpnbook | 88wxtet | France |
| it.vpnjantit.com | vpnjantit.com | i0ryj | Italy |
| us1.vpnbook.com | vpnbook | 88wxtet | USA |
| us2.vpnbook.com | vpnbook | 88wxtet | USA |
| ca1.vpnbook.com | vpnbook | 88wxtet | Canada |
| de233.vpnbook.com | vpnbook | 88wxtet | Germany |
| uk.superfreevpn.com | free | 7833 | UK (London) |
| ca.superfreevpn.com | free | 1251 | Canada (Montreal) |
| nl.superfreevpn.com | free | 2988 | Netherlands (Brabant) |
| us.websitevpn.com | websitevpn.com | freevpn | USA |
| us1.superfreevpn.com | free | 1596 | USA (Miami) |
| us2.superfreevpn.com | free | 2737 | USA (Chicago) |
| gr.vpnjantit.com | vpnjantit.com | i0ryj | Germany |
| uk.realfreevpn.com | realfreevpn | 25570 | UK |
| de.realfreevpn.com | realfreevpn | 93937 | Germany |
| fr.realfreevpn.com | realfreevpn | 76216 | France |
| 188.166.6.170 | contassh | abcd1234 | Netherlands |
| 188.166.155.99 | contassh | abcd1234 | Netherlands |
| 178.62.38.164 | sshagan | abcd1234 | UK |
| 46.101.79.161 | sshagan | abcd1234 | UK |
| 128.199.221.154 | contassh | abcd1234 | Singapore |
| 128.199.96.14 | contassh | abcd1234 | Singapore |
| uk.websitevpn.com | websitevpn.com | freevpn | UK |
| ca.justfreevpn.com | justfreevpn | Canada Free VPN Account | Canada |
| uspptp.hotfreevpn.com | free | 1234 | USA |
| 51.15.151.165 | pptp | ykDJYnCIirN | France |
| 192.241.184.169 | sshagan | abcd1234 | USA |
| 192.241.179.120 | sshagan | abcd1234 | USA |
| 139.59.237.15 | sshagan | abcd1234 | Singapore |
| 128.199.214.71 | sshagan | abcd1234 | Singapore |
| 138.68.140.197 | contassh | abcd1234 | UK |
| 138.68.64.68 | contassh | abcd1234 | UK |
| 159.203.111.101 | contassh | abcd1234 | USA |
| 139.59.244.147 | sshagan | abcd1234 | Singapore |
| 162.243.33.71 | sshagan | abcd1234 | USA |
| 162.243.15.104 | sshagan | abcd1234 | USA |
Alternatives to PPTP
As said earlier, PPTP is by far the easiest VPN protocol to setup. However, it is worth looking at the alternatives for the extra bit of security that they offer.
OpenVPN
OpenVPN has the highest level of security often recommended by VPN providers. It is normally built-in with the VPN services, but when it’s not, then it’s a complicated endeavor. It has an SSL 256-bit encryption by default but only manages to decrease the internet speed by 10%. Due to the reason select the best VPN for OpenVPN.
L2TP/IPSec
It comes second when we speak of the best VPN protocol. L2TP is a protocol, while IPSec is its encryption. If you only happen to see L2TP without IPSec, then avoid it if you can. The only vulnerability we could find is its slow internet speed.
SSTP
It is an upgraded version of PPTP which is also developed by Microsoft but far more useful. You will only find this protocol supported by Windows, otherwise, it is just as secure as L2TP/IPSec. It is easier to set up, but many VPNs do not support it.
IKEv2
Also a product of Cisco and Microsoft. Device compatibility is something to worry about since it is not available for many devices. Its greatest strength is to quickly reconnect when the connection drops and uses IPSec for encryption which is something to cheer about.
Key Takeaways
- PPTP VPN remains popular on account of increased functionality
- PPP served as a bridge between the physical link at the user’s end and the Internet Protocol
- PPTP was the first protocol to achieve formal recognition as a VPN protocol
- Besides Windows, PPTP is also used on Mac and Linux platforms because of its speed and compatibility
- The PPTP VPN protocol borrows authentication protocols from the PPP
- Once browser add-ons like Firesheep have extracted your key, you’re #virtuallydead
- Your PPTP VPN should guarantee 256-bit encryption
- Windows, Unix, Linux, and Mac OS clients are all capable of connecting to a VPN using PPTP