‘‘Every breath you take
Every move you make
Every bond you break
Every step you take
I’ll be watching you
Every single day,
Every word you say,
Every game you play,
Every night you stay,
I’ll be watching you”
Who knew that a song released in 1983 by Police would fit perfectly for National Security Agency (NSA)?
The lyrics of ‘Every Breath You Take’ quite literally dictate the antics of NSA. The powerful intelligence agency has a checkered history when it comes to preserving the privacy of netizens.
Therefore, to enlighten our readers, I have created a detailed guide that will explain all the steps taken by NSA to spy on its citizens, gather mass information about users, and monitor communications entering or exiting the US cyberspace.
So let’s dive in…
History
The National Security Agency (NSA) is one of the most powerful intelligence agencies of the United States that reports its activities to the Director of National Intelligence.
NSA in allegiance with different institutions and corporate giants is notorious for its vigilant and spying activities.
The National Security Agency has been using diverse tactics to spy our online and offline activities.
What we claim as a breach of our privacy – they call it mandatory security measures.
NSA, without our consent, monitors our activities.
There are several corporations that have joined the cause; however, we were completely unaware of the allegiance before Snowden’s revelations.
Edward Snowden – A Hero or a Traitor

Edward Snowden is a former CIA employee who worked with NSA as an Infrastructure Analyst.
Snowden was responsible for disclosing NSA’s confidential and top-secret documents to media causing one of the controversial leaks in history.
Snowden revealed NSA’s operational activities referring to their global surveillance program along with the tools used by the NSA to exploit our privacy.
Snowden affirmed that NSA works in allegiance with diverse commercial entities to invade the privacy of not only the citizens of the United States but the world.
Snowden revealed that the world’s privacy is being victimized by the Five Eyes Alliance consisting of:
- United States
- United Kingdom
- Canada
- Australia
- New Zealand
As per the Snowden’s revelations, there are several surveillance programs exposed such as PRISM, Upstream, Tempora and XKeyscore etc. which reflected not only the involvement of NSA but also GCHQ. Snowden also revealed that it all started at the domestic level.
Where many consider this whistleblower as their hero – some declare him as a traitor who should be treated no differently. Let’s have a look at House Speaker’s tough talk about Snowden.
NSA is blamed to spy on our activities and data via sophisticated measures and tools.
NSA has now been working with different telecommunication and IT giants to carry forward their surveillance programs.

Soon after Snowden’s revelations, NSA’s allegiance with GCHQ (Government Communications Headquarters) became center of attention for those who still consider privacy as a priceless asset.
However, despite severe criticism (national and international), NSA continued its operations – taking them to a whole new level.
The National Security Agency is supposed to have a long history with RSA. RSA – a subsidiary of EMC Corp is a tech giant renowned for its product related to Internet security.
NSA signed a $10 million deal with RSA instructing the tech giant to manufacture blemished Internet security tools.
These tools and equipment were to be used by NSA as a backdoor to serve their wicked intentions of spying.
Snowden Holds a Live Conference from Moscow
On January 24, 2019, Snowden showed up over video broadcast at Paris 1 Panthéon-Sorbonne University, from Moscow.
Within a matter of three minutes, the entire auditorium has a capacity of 500 was filled, while 7,000 people were on the waiting list.
The moment Snowden’s face was shown on the screen the crowd erupted with whistles and applause.
While Snowden would love to live in Paris, the French government it won’t offer him asylum. This is probably because they do not want to adversely affect its relationship with America.
In the conference, Snowden explained how he questioned CIA and NSA’s practices.
He further shed light on how everything today can be tracked electronically like parents can access their children messages and online activities. Get the complete news here.
The Regimes Discovered
Prism
Prism costs nearly a sum of $20 million to the United States government in the name of the surveillance activities initiated.
There are several multinationals and tech giants perceived to work in allegiance with the NSA under the Prism initiative.
Apple, Facebook, AOL, Microsoft, Yahoo, and PalTalk etc. are considered as NSA’s pawns in this game.
Upstream
The Upstream represents the bulk intercept programs initiated by the National Security Agency.
The Upstream program initiated by the NSA corresponds to the process of intercepting communications cables in order to extract the information via the target’s communication.
GCHQ is believed to work in alliance with NSA in this regard as their upstream programs are similar to that of the National Security Agency.
Cryptography
Under this program, the National Security Agency works in systematic alliance with the GCHQ to weaken the encryption systems and tools.
Furthermore, the prime objective of the NSA in this regard was to deteriorate the security measures adopted by users.

This program costs the NSA roughly $250 million per year. Under this program, NSA strives to flaw the software and even hardware we use.
With its allies (Tech Companies), the NSA has left our privacy vulnerable so that it can easily access, analyze and store whatever data it wishes to acquire from us.
During George Bush’s presidency, the word got out that the US has been collecting phone records of millions in name of national security.
The officials declared that the regime has been disavowed and we actually believed it – so naïve we are.
Meta Data Collection
Meanwhile, the National Security Agency was working aggressively at the backend – collecting Meta Data of not only American but the world.
The National Security Agency via this initiative is still collecting, analyzing and even storing contents of our business and private conversations via the calls we make.
If this continues to happen, the word ‘Privacy’ will vanish from the dictionary of generations yet to come.

The Controversies
Partnership with RSA
One of the many controversies associated with the National Security Agency is the deal with RSA.
After Snowden’s revelations, it was discovered that NSA had offered $10 million to RSA for blemish products.
The Verizon Conspiracy
The National Security Agency is also notorious for its allegiance with Verizon Communication.
With more than 95 million customers, Verizon is one of the renowned telecom giants.
In April 2013, the National Security Agency authorized Verizon Communication to record the conversations and every possible communication of their customers.
AT&T Conspiracy
The National Security Agency’s coalition wasn’t confined to Verizon only. Soon, it was discovered that the NSA had issued a similar notification to AT&T.
AT&T is even more popular than Verizon with more than 100 million clients whose privacy was violated on the basis of an undignified order.
Apple Conspiracy – Offering NSA a Backdoor
Another conspiracy represents Apple’s alliance with the National Security Agency.
NSA’s leaked documents revealed its allegiance with Apple where the secret agency was endorsing a built-in program in iPhones that can serve as a backdoor for the NSA. They called it ‘DropoutJeep’.
The program could facilitate the NSA to extract, analyze and store data in users’ iPhones.
NSA via this backdoor could access your pictures, emails, messages and even record your voice calls.
The program was however delayed; but, when there’s NSA involved – who knows – it might be currently operational.
NSA Agents Spy on World of WarCraft and Dota2
The growing popularity of MMORPGs among gamers facilitated yet another wicked NSA schemes.
The National Security Agency deployed its agents on different servers of World of WarCraft and Dota2 to engage in the MMORPGs.
The National Security Agency perhaps required insight into the gaming community.
These agents were strictly instructed to monitor and report any odd activity at MMORPGs servers.
Tailored Access Operations
The National Security Agency operates Tailored Access Operations also known as TAO.
TAO is a unit comprising 2000 workers dedicated to executing the hacks and cyber-attacks designed by the NSA for diverse purposes
The Quantum
NSA currently seeks a quantum computer that will decrypt any form of encrypted data.
Through the quantum computer, the National Security Agency will be equipped with the technology that can decrypt almost any known encryption in this digital universe.
This depicts a significant threat as the NSA with a quantum computer along with diverse backdoors and other spying tools would surely bring death to our privacy and security.
Top NSA Whistle Blowers who came before Edward Snowden
You may have heard about Edward Snowden, but have you ever heard about J. Kirk Wiebe, Mark Klein, and William E. Binney.
These brave men blew the whistle on the NSA much before Snowden and told us the truth about the NSA over a decade ago.

J. Kirk Wiebe

- Kirk Wiebe was one of the first few people who realized that the NSA was directing its resources to spy on American civilians without any probable cause.
The attacks of 9/11 served as confirmation that the NSA had failed to serve its purpose mainly because it was being utilized for misdirected surveillance.
Mark Klein

Mark Klein is a former AT&T employee who blew the whistle on the NSA’s domestic surveillance.
As a technician at AT&T, in 2002, Mark Klein became suspicious when he noticed the NSA’s increased involvement.
According to information leaked by Mark Klein, AT&T gave the NSA access to its San Francisco facility and thereby helped the NSA in tapping into countless email and internet records.
He worked for AT&T for 22 years up until he retired in 2004, after which he continued to draw attention to the NSA’s activities.
Mark Klein confirmed that:
“This splitter was sweeping up everything, vacuum-cleaner-style. The NSA is getting everything. These are major pipes that carry not just AT&T’s customers but everybody’s”
Mark Klein blew the whistle on the operation after former President George W. Bush insisted that the NSA only collects meta-data and that Americans are not the only target of this surveillance.
William E. Binney

William E. Binney worked for the NSA for over 30 years, and then he blew the lid off all the lying and data stealing that the NSA is doing.
According to William E. Binney:
“Where I see it going is toward a totalitarian state. You’ve got the NSA doing all this collecting of material on all of its citizens – that’s what the SS, the Gestapo, the Stasi, the KGB, and the NKVD did”
NSA’s Year of Online Surveillance: Revelations & Confessions
On the eve of Christmas, NSA ‘publicized’ hundreds of surveillance reports of the past decade.

The reports date back to 2001 and include the information that was once termed as “classified”. In all honesty, it was actually a Christmas confession by the NSA.
The reports were made public and released online on 24th December 2014.
The documents were heavily censored but they conveyed the message clearly i.e. the staff members of NSA were also involved in illegal surveillance of the citizens.
NSA’s Surveillance will not be Curbed – Senate
In historical polling in 2014, the Senate ultimately voted against the limitations on NSA’s surveillance.
The legislation needed 60 votes to be implemented but received only 58.
Had the legislation been implemented, bulks of phone numbers would have been deleted from the records of NSA.
Snowden Not Allowed Testifying Against NSA in Germany
The highest court of Germany has ruled out the proposal of the opposition parties to invite Edward Snowden to Germany to testify against NSA.

The parties were forcing the government to call him to Germany to speak freely against the “unethical and illegal” online surveillance done by NSA.
The court responded by rejecting the appeal of the opposition parties, stating that it would not risk the relationship with the US.
Snowden had earlier made it clear that he would only speak against NSA if he was allowed to do so in Berlin, Germany.
Operation AURORAGOLD Reveals NSA Snooping on Global Cellular Networks
According to the documents revealed by Edward Snowden, the top-secret operation “AURORAGOLD” was aimed to provide the NSA with the information of cell phone users all over the world.
The report was said to provide the NSA the loopholes so it could hack into the servers of global cellular networks.
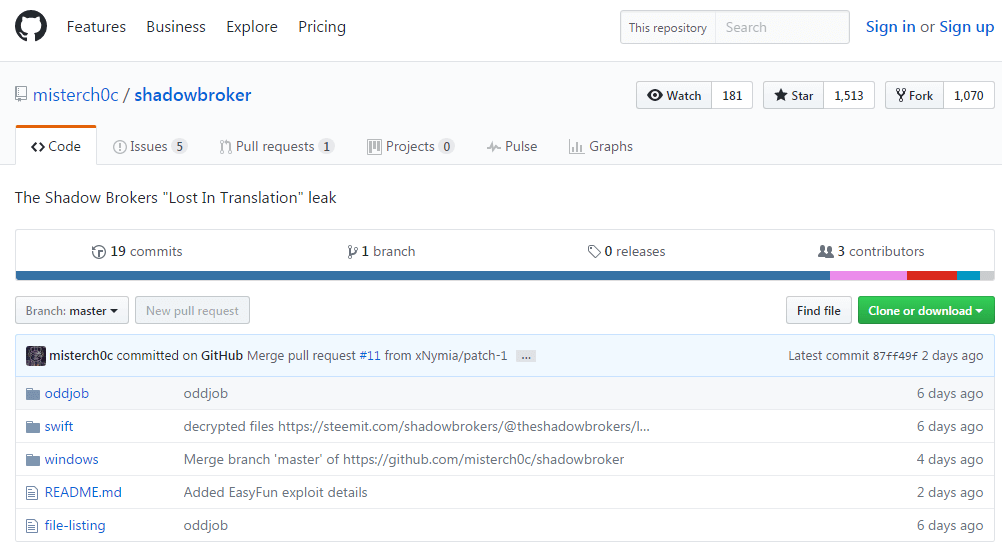
Shadow Brokers Expose NSA’s Spying Tools – Secure Your Privacy
The Russian vigilante hacking group “The Shadow Brokers” has exposed NSA’s secret tools that are responsible for breaching Windows and various financial networks including SWIFT Bank.
Below is a screenshot of breached NSA spying tools mirrored on GitHub:
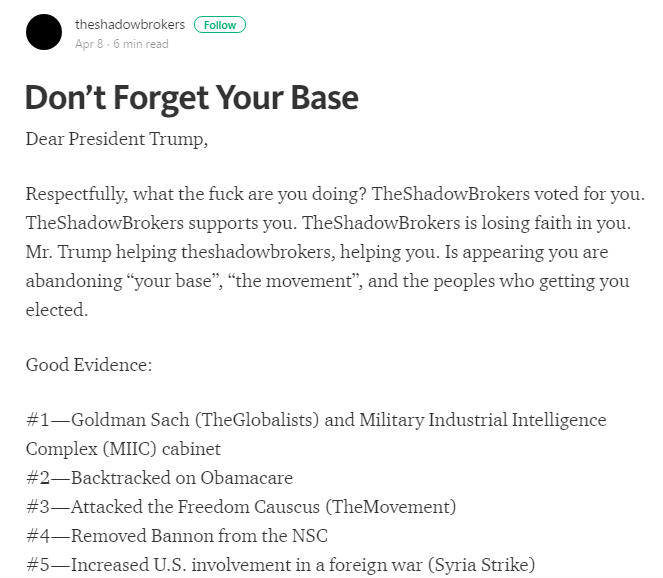
However, to clear any doubts, Shadow group has itself left users with an enigmatic message confirming breach as a protest against Republican President Donald Trump.
Over and above, the Shadow Group has stated the following reasons behind NSA expose:
NSA Hacked by Shadow Brokers; Snowden’s Take on The Issue
The hackers call themselves “Shadow Brokers” and demanded $568 Million in Bitcoin to auction the best cyber weapons and breached data.
The hackers have claimed that if the auction raises 1,000,000 bitcoins, then a large amount of breached information will be exploited publically. But the auction winner will still get exclusive files.

Edward Snowden’s Note about NSA Hack
3) This is how we steal their rivals' hacking tools and reverse-engineer them to create "fingerprints" to help us detect them in the future.
— Edward Snowden (@Snowden) August 16, 2016
Considering the hacking attack on NSA, famous digital privacy activist Edward Snowden has revealed surprising elements behind the hack. Moreover, the hack itself is not as surprising as how the hackers revealed about conducting it.
Quick review of the #ShadowBrokers leak of Top Secret NSA tools reveals it's nowhere near the full library, but there's still so… (1/2)
— Edward Snowden (@Snowden) April 8, 2017
What Has Been Breached So Far?
The prime target of the hack was the Equation Group which had been active in hacking for more than two decades, as reported by Kaspersky in 2015.
The organization has been alleged to involve in Regin and Stuxnet attacks. Shadow Brokers have already revealed some of the breached files on Tumblr.
This isn't a data dump, this is a damn Microsoft apocalypse. #0day #shadowbrokers
— hackerfantastic.x (@hackerfantastic) April 14, 2017
Beyond the American & Chinese Firewalls
Surprisingly, the leaked files contain sensitive information such as installation scripts and server configuration files which were created to breach the US manufactured routers and firewalls. The list of US manufacturer includes Cisco, Juniper, and Fortinet.
In addition to this, the hack also reveals information, showing that famous Chinese organization “Topsec” was among the targets of the Equation Group.
WikiLeaks Claims NSA Tapped Top German Officials for Years
According to WikiLeaks, the NSA kept a sharp eye on all the telephonic discussions of German Chancellor Angela Merkel and all her advisers.
WikiLeaks also claims that NSA’s phone tapping was not confined to her and her advisers only; the NSA had been doing the same tactics on her predecessors as well.
WikiLeaks further claims that phone numbers of 125 officials were being tapped in a long-term surveillance program.
The German government was quick to react and a spokesperson said that the authorities in Berlin were looking in the matter very closely.
He also made it clear that such actions are not acceptable since the two countries are supposed to collaborate for intelligence activities.
The US government, however, did not elaborate if it did tap the phone calls of Angela Merkel and her associates
NSA’s desire to have a skeleton key to everyone’s encrypted data
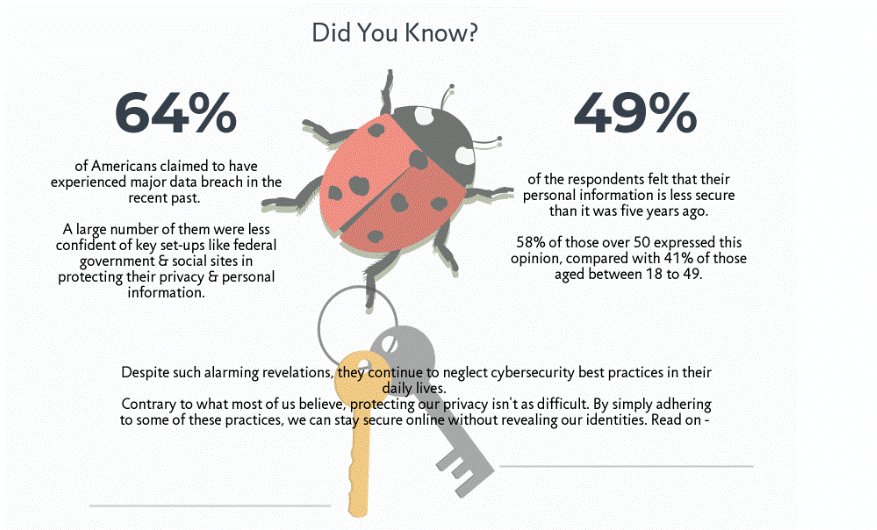
There are diverse security and privacy threats we face in our daily lives.
The rise of the digital era has enhanced the frequency of cybercrimes we acknowledge along with the concerns of cyber terrorism.
In order to cope with all these concerns, some vigilant agencies such as the National Security Agency started different regimes.
However, all these regimes and schemes were taken to the whole new level lately.
Sadly, you are your data. Therefore, you have to secure your data if you wish to protect yourself.
There is no denying encryption allows you to safeguard your online data next level.
Moreover, it also protects you from government intrusion. This is the reason the government wants to get the key to access your data.
But all hope is not lost.
You might be wondering how it is possible. Follow the below steps:
How to anonymize everything you do online
Interestingly, it is still possible to anonymize everything you do over the internet. Here is how you can do:
- Block third-party cookies
- Use incognito mode
- Give permissions to websites you visit
You can secure your privacy while practicing simple tips to a certain degree.
There is no harm in using a private browser if you want to improve your online security next level.
Likewise, it allows you to remove your online traces of internet usage session once you close the window.
How can I protect my privacy on Facebook?
Honestly speaking, this question needs a detailed answer. Here is the list of steps you should follow to achieve your mission:
- You should limit access to your Facebook posts
- Refrain non-friends from following your posts
- Your names should not be linked with ads
- Do not give Facebook apps access to your data
By following the above-described tactics, you can protect your digital whereabouts on Facebook hassle-free.
How can I protect my privacy on Twitter?
Luckily, you can attain your objective by following these simple below mentioned tips. These are:
- Do not allow Twitter to track your personal information
- You should stop sharing data while tweeting
- You should not allow Twitter to access your contacts
This is how you can safeguard your privacy on Twitter and at the same time, you can stay safe from NASA’s surveillance.
Any tips to disappear from the internet ?
byu/dgs84W8QTUrNwAHw inprivacy
NoSpyProxy the World’s First Data Center NSA Can’t Touch
The virtual world faces constant threats of cybercrimes and online surveillance. In the war between the hackers and surveillance agencies, the ordinary internet users are made the sacrificial lambs.

Cybercriminals and secret agencies have all the resources that are needed to sneak into users’ computers to access all their confidential information.
View our detailed review about the CyberGhost service to learn more about the provider.
Conclusion
There is much to be discussed and there’s more to be told – NSA’s story doesn’t end here.
There are countless regimes representing the agency and there are numerous conspiracies.
Some of them are known – thanks to Snowden – and the others still remain a mystery. We don’t know what NSA’s intentions are for the future.
It is high time to take your privacy and security seriously. The NSA with its diverse tools and sophisticated methods is all set to infiltrate your private moments, confidential data and monitor every move you make.
The best you can do to protect your data is to use a higher level of encryption that may be difficult for the NSA to decrypt.
So, even if your security is infiltrated and data accessed – they’ll gain nothing from it.
