On Monday, Italy’s Computer Security Incident Response Team issued an urgent alert. The point of the alert was to raise awareness about the high risks associated with cyberattacks against national institutions.
The Italian organization deciphered the cyberattack to be DDoS (distributed denial-of-service), which may not be that disastrous but it can still cause certain damages, financial or of any other kind because of disruptions and service outages.
The public alert said:
“There continue to be signs and threats of possible imminent attacks against, in particular, national public entities, private entities providing a public utility service or private entities whose image is identified with the country of Italy.”
The origin of these signs are posts on Killnet group’s Telegram channel, which said they intend to incite ‘massive and unprecedented’ attacks against Italy.
Killnet is a pro-Russian hacktivist group. They attacked Italy just two weeks ago. Although they used an old method, it’s still an effective DDoS method which is called ‘Slow HTTP.’
CSIRT proposed a defense mechanism to be launched with DDoS-related attacks. They also included various good security practices for safeguarding the public.
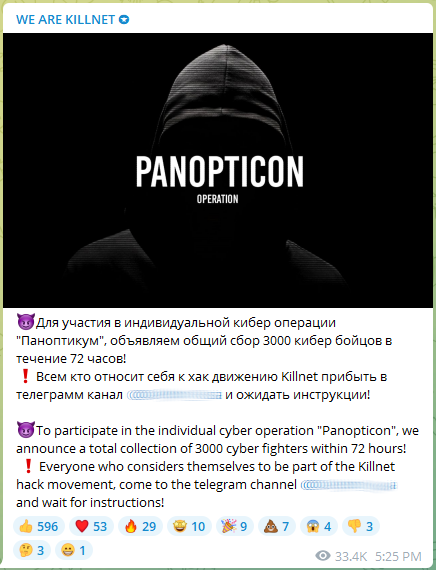
Operation Panopticon
Operation Panopticon was announced by Killnet last Tuesday. They called for 3000 “cyber fighters” to volunteer within 72 hours. The call to action was repeated several times last week by the group.
If you volunteer, a sign-up form requests information like your system, origin, age, and Telegram account. It also supplied you with the tools required to launch resource-depletion attacks.
Although Killnet’s primary goal is to carry out a DDoS attack, they may use it as a decoy to get the defenders to tackle service disruptions instead of taking on the cyberattacks as they come.
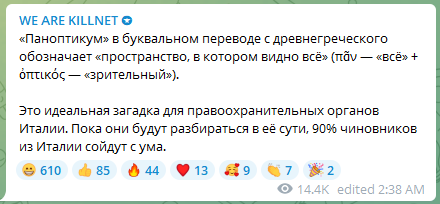
Just recently, Killnet shared an etymological explanation of the word Panopticon, in an attempt of data leaking innuendos. They warned that 90% of the country’s officials ‘will go crazy.’
Using machine translation, the text above reads:
Hacker Feud
As a pro-Russian hack group, Killnet has made the Italian organization its target because of its support for Ukraine’s resistance against Russia. As a result, Anonymous Italy decided to fight back by attacking Killnet, and even doxing some of its members by publishing photos on social media. Hence, Killnet also struck back.
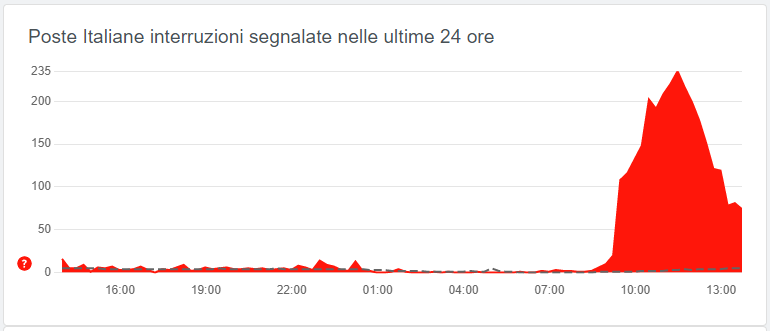
For a certain while, the CSIRT Italy website was inaccessible, however, the connectivity issues didn’t last long. Poste Italiane, Italy’s national postal service also suffered a multi-hour outage just this morning.
The Post Italiane told the outage was a result of a software upgrade that went wrong and didn’t have anything to do with Killnet.
According to other local media reports, upon closely following Italian sites, the portals of the State Police and the Ministries of Foreign Affairs and Defense, they also seemed to be irresponsive today.
Security Recommendations to Protect Against DDOS Attacks
The following recommendations were issued to help fight back the DDoS attacks and minimize damage to the systems:
- A response plan to counter the DDoS attack that’d include escalation protocols and a checklist of necessary tools.
- Securing the high levels of network security using firewalls, intrusion detection systems, anti-virus, and anti-malware are updated.
- Practice server redundancy by using distributed servers so if one were under attack the other won’t be affected.
- Keep a lookout for warning signs: poor connectivity, slow performance, unusual traffic, crashes, high demand for a single page, etc.
- Continuously monitor network traffic so that you are aware of real-time issues and can detect odd activities.
In this way, you’ll be minimizing risks associated with a DDoS attack and be able to restore systems through backups in case of an emergency.