According to research by Proofpoint, a new phishing attack is taking place where attackers are leveraging fear over the spread of the new COVID-19 strain, Omicron, to steal login credentials of accounts at several North American universities.
Proofpoint researchers said that the phishing attacks began in October, but they witnessed a sharp increase in November. The emails sent by attackers contain general information about the new COVID-19 variant Omicron and information about testing.
Cybercriminals have been using the concern about COVID-19 luring targets with phishing scams since January 2020.
Phishing Campain Details
In this COVID-19 theme campaign, attackers have targeted various North American universities. The students and faculty receive a phishing email that contains URLs and attachments that harvest login credentials when clicked upon. The landing pages imitate the university’s login portal. In most cases, attackers redirect users to a legitimate university portal page, after which the credentials are harvested.
Such emails are usually subjected as:
Attention Required – Information Regarding COVID-19 Omicron Variant
The email also contains a link to the university login page, as shown below:
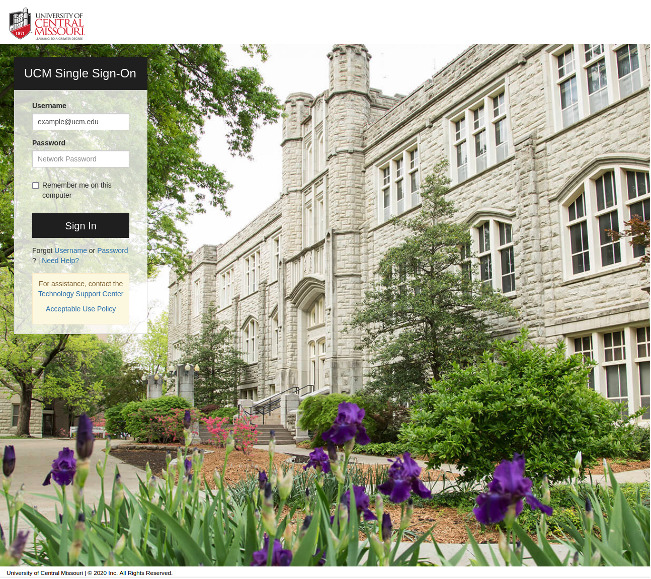
(Image: Proofpoint)
Some students have also received emails with COVID-19 test attachments as well. The attachment leads to the university login page, where the credentials are stolen.
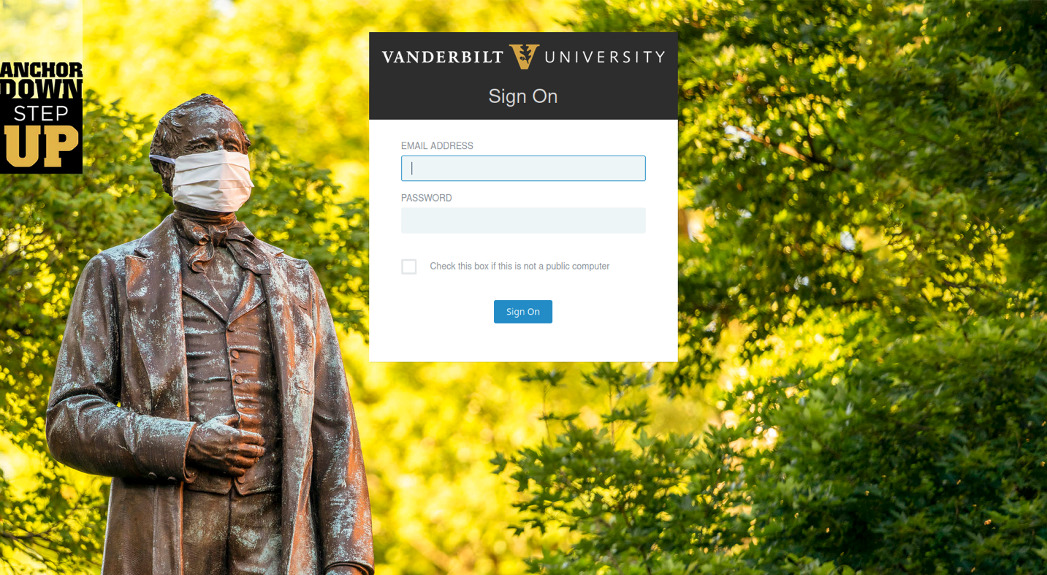
Credential theft page in phishing email spoofing Vanderbilt University. (Image: Proofpoint)
According to Proofpoint, threat clusters use different methods to distribute these campaigns. In this Omicron COVID-19 variant campaign, attackers are using actor-controlled infrastructure to host fake credential theft university websites using similar domain names. These include:
- sso[.]ucmo[.]edu[.]boring[.]cf/Covid19/authenticationedpoint.html
- sso2[.]astate[.]edu[.]boring[.]cf/login/authenticationedpoint.html
Similarly, attachment-based Omicron campaigns use compromised WordPress sites to capture credentials. These include:
- hfbcbiblestudy[.]org/demo1/includes/jah/[university]/auth[.]PHP
- afr-tours[.]co[.]za/includes/css/js/edu/web/etc/login[.]PHP
- traveloaid[.]com/css/js/[university]/auth[.]php
In some campaigns, attackers have also attempted to steal multi-factor authentication passwords, pretending to be Duo. Stealing MFA codes would enable the attackers to bypass the second layer of security.
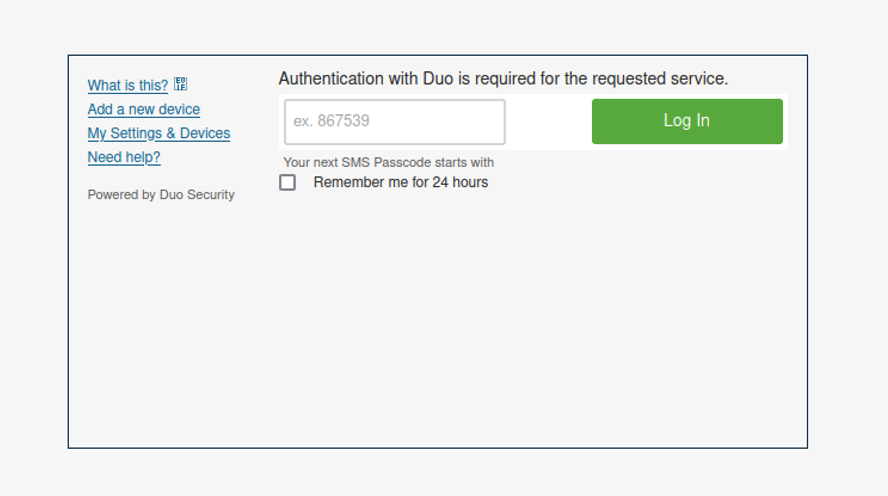
MFA Duo credential theft landing page (Image: Proofpoint)
Proofpoint has also observed that once the attackers get access to university accounts, they use those compromised accounts to spread the campaign and send emails. The compromised emails are also used to spread the same threat to other universities as well.
“It is likely this activity will increase in the next two months as colleges and universities provide and require testing for students, faculty, and other workers traveling to and from campus during and after the holiday season, and as the Omicron variant emerges more widely,” – Proofpoint researchers.
Some universities that have been targeted include the University of Central Missouri and Vanderbilt University. Hank Schless, a senior manager at Lookout, said that at the beginning of the pandemic, there was a lot of phishing activity luring targets with promises of government aid, free COVID-19 tests, information regarding government shutdowns, and more.
Schless said that his company saw an 87% increase in mobile phishing attacks in the first quarter of 2020. By 2021, attackers started luring people with promises of information regarding vaccines and reopening.
“Between Q4 of 2020 and Q1 of 2021, exposure to phishing increased 127% and remained at the same level through Q2 and Q3. Now, with questions around the Delta and Omicron variants, attackers are again using this as a way to convince potential victims to trust their communication and unknowingly share login credentials or download malware. Academic institutions make for ripe targets in the eyes of cybercriminals,” Schless said.
According to Schless, attackers can use credentials to steal research data of universities and projects that could lead to ransomware attacks. According to Proofpoint, the end goal of attackers is still unknown. However, according to Schless, these “campaigns are often starting point for more advanced cyberattacks.”
If you suspect that an email or text message you received is a phishing attempt:
- Do not open it. In many cases, the very act of opening the phishing email may end up compromising your personally identifiable information.
- Delete it immediately. This act will prevent you from accidentally opening the message in the future.
- Do not download any attachments. Usually, the attachments accompanying the message contain malware such as viruses, worms, or spyware.
- Do not click on the links that appear in the message. The links attached in the messages usually redirect you to fraudulent websites.
- Do not reply to the sender. It’d be best to ignore any requests from the sender.
If you get a phishing email, forward it to the Anti-Phishing Working Group at reportphishing@apwg.org. If you got a phishing text message, forward it to SPAM (7726).
You can also report the phishing attack to the FTC at ReportFraud.ftc.gov.
