
An IP fragmentation attack in Canada is a denial of service (DoS) attack in which attackers overbear a network by manipulating datagram fragmentation instruments. The consequence of this action is that it restricts genuine users from accessing a site/service.
To comprehend these attacks, you first need to know what is fragmentation. To summarise, it is a process in which IP datagrams are broken into small pieces, transmitted across a network, and then reconstructed into the original datagram once they reach their destination – a process called IP routing.
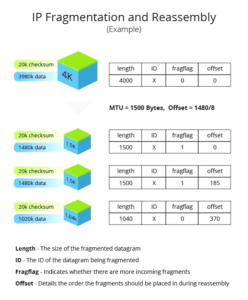
Each network has a certain size limit of the IP packets it can process, known as the maximum transmission unit (MTU). Any datagram larger than the defined MTU of a receiving server is broken into pieces so that it can be transmitted completely. That’s what a fragment is.
(Image Credits: Imperva)
In each datagram, the IP header contains multiple flags detailing if the fragmentation is allowed to take place or not. If there’s a ‘don’t fragment’ flag attached to the IP header, the IP packet is dropped, and the server disseminates a message saying that the ICMP datagram is too large to be transmitted.
The recipient device is explained by the offset the exact order in which the fragments require being reassembled.
Now you know what is an IP fragmentation attack in Canada, let’s look at its types.
Types of an IP Fragmentation Attack in Canada
There are various types of IP fragmentation attack in Canada. However, all of them are to deactivate devices and block services. IP fragmentation attack in Canada constitute disseminating datagrams with the intent of problematic reconstruction once they’re received.
Following are a few types of IP fragmentation attack in Canada:
1. Tiny fragment attack:
This miniature attack occurs when a tiny packet fragment lands on a server. This usually occurs when it cannot fit its header as it’s too small, causing problems in reassembly, which can potentially shut the server down.
Every IP packet contains a payload and header. The header contains information that directs the packet towards its destination. Meanwhile, the payload is a framework that carries data toward the header.
2. UDP and ICMP fragmentation attacks:
This frag attack includes the transmission of UDP or ICMP packets that are fraudulent and larger than the MCU of the network (mostly ~1500 bytes). Since these packets are fake and cannot be reassembled, the resources of the target server are consumed quickly, which results in the unavailability of servers.
3. TCP fragmentation attacks (Teardrop attacks):
These are known as Teardrop attacks. These attacks target the reassembly mechanisms of TCP/IP and prevent them from reconstructing fragmented data packets. As a result, the IP packets overwhelm and overlap victims’ servers, which causes them to fail.
Teardrop attacks result from a vulnerability in the older OS versions of Windows, including 95, NT, and 3.1. Even though the patches have been thought to stop these attacks, a resurfaced vulnerability in Windows Vista and 7 have made Teardrop attacks again a viable attack vector.
The vulnerability was repatched in the latest Windows versions, but operators still require keeping an eye out to ensure that it remains patched for all future versions.
How to Keep Yourself Protected from an IP Fragmentation Attack in Canada
You can use the following methods to reduce the risks of an IP fragmentation attack in Canada:
- Ensure that you’re using the updated operating system, which has installed all the latest security patches.
- Inspect all the incoming IP packets by using a firewall, router, proxy server, or other intrusion detection tools. However, please note that denial of service (DoS) attacks cannot be detected by a firewall.
- You can stop people from sending you fragmented packets by cutting your ties with them. However, a few benign connections like cellphones use fragmented IP packets. If you disable these packets, they might cause disruptions in your traffic.
It’s always beneficial to go for a multi-layer approach in this. We highly recommend combining the first two for a useful combination of connectivity and protection.
FAQs
How does a fragmentation attack work in Canada?
An IP fragmentation attack in Canada uses IP fragmentation to disrupt and disable services and devices. It involves sending datagrams that would be impossible to reconstruct after reaching their destination.
How common is IP fragmentation?
IP fragmentation is a pretty common concept and is being used on networks all across the globe. IP packets are broken into multiple packets, which are then sent through the network layer where they are reconstructed as part of routine communications.
Is IP fragmentation bad in Canada?
Well, we can’t say. But if the data rate of stream A is way higher than stream B, for example, the 64 fragments arriving from stream A might arrive in between stream B’s fragments, causing the B fragment to drop. So, even though IP fragmentation can minimise user headers by reducing overhead, it may cause way more trouble than it’s worth.
How is fragmentation avoided in Canada?
If you write a new file of the known size and if any empty holes are bigger than that, the OS can avoid fragmentation by putting those files in one of those empty holes.
Conclusion
IP fragmentation is quite necessary and is an essential part of the IP protocol. But, attackers have used it extensively for circumventing and bringing down proxy servers, firewalls, and other intrusion detection systems.
All the IP fragmentation attack in Canada mentioned above have been around for a long time now, but they can still pose threats if your operating systems are outdated and do not have the latest versions of service packs and packets.
We hope you got all the necessary details about an IP fragmentation attack in Canada. But that wouldn’t get you through all the knowledge you require of IP addresses. Other things you should definitely learn are IP filtering, IP routing, and IP encapsulation.
