
(Image Credit: Shutterstock)
Ubiquiti Inc., a major supplier of cloud-based devices like routers, security cameras, and video recorders disclosed that it was breached on January 11. The data breach involved exposure of customer information including account credentials. However, a security professional who helped the company respond to the breach claimed that Ubiquity downplayed the catastrophic breach in order to minimize its effect on the company’s stocks, reported by KerbsOnSecurity.
What’s upsetting about this incident is that Ubiquiti has been covering up the data breach, which puts its customer’s hardware at risk as the credentials can always be used for unauthorized access. The whistleblower wrote a letter to the European Data Protection Supervisor stating,
Ubiquiti did not respond to these claims as it should have. The source also wrote that the company “downplayed and purposefully written to imply that a 3rd party cloud vendor was at risk” stating that Ubiquity was a casualty during the attack and not the main target.
Ubiquity Data Breach – Details
In reality, however, the attackers gained access to Ubiquiti’s servers and databases at Amazon Web Services (AWS) that secures the underlying software and hardware. According to the source, the attackers were able to “get cryptographic secrets for single sign-on cookies and remote access, full source code control contents, and signing keys exfiltration.”
The whistleblower also stated that during the breach the attackers were able to get access to Uquibiti’s employee credentials and used it to gain root administrative access to Ubiquiti’s accounts at the Amazon Web Services. It gave them full access to all application logs, S3 data buckets, the entire database, credentials, and information required to create single sign-on (SSO) cookies.
With such information, the attackers could remotely access countless cloud-based devices of Ubiquiti. This is very concerning, as according to Ubiquity, it has shipped around 85+ million devices to over 200+ locations worldwide. All these devices left compromised due to the data breach!
According to the source, the attackers left a backdoor in the system, and that is how Ubiquity found out about the breach. When the backdoor was finally removed, the attackers approached the company asking for 50 bitcoin (~$2.8 million USD) in exchange for remaining silent about the data breach.
The intruders also said that they had stolen Ubiquiti’s source code and there is another backdoor in the company’s system that will be revealed only if their demands are met. However, Ubiquity was fortunate enough to find the second backdoor and they did not engage with the attackers.
Ubiquity’s response to the breach
Ubiquity finally made a public announcement on March 31 after 24 hours of silence saying that it “recently became aware of unauthorized access to certain of our information technology systems hosted by a third party cloud provider.” The company also said that while there was no evidence that the attackers got their hands on the customer data, they couldn’t rule out the possibility of compromised user names, emails, passwords, and phone numbers.
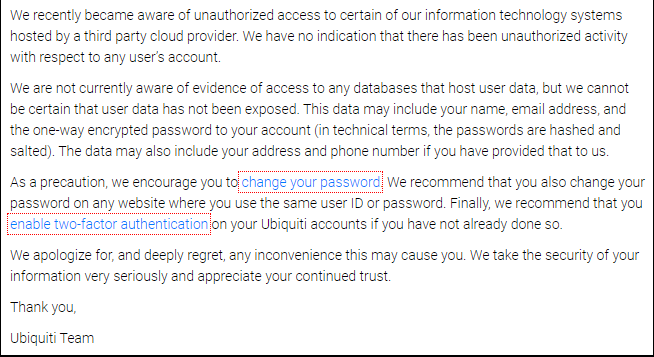
The most concerning thing is that instead of alerting the customers about the breach right away, Ubiquity only recommended its users change their passwords. Instead, they should have immediately invalidated all customer usernames and passwords and asked the users to start fresh. This incident is a huge wake-up call for all cloud-based device vendors, especially concerning security and encryption.
Therefore, if you have a Ubiquiti device, now would be the perfect time to change your username and password. It is also recommended to enable two-factor authentication and also delete any user profiles associated with the Ubiquiti device and create a new one with fresh credentials and a strong password.
