NordVPN Review 2024: How Secure and Effective this VPN is?
- Updated: January 30, 2024
- 64 User Reviews
- Gerald Hunt

NordVPN solidified its position as a leading VPN provider in 2024, acclaimed for its exceptional speed, advanced online security features, and comprehensive capabilities in streaming and torrenting. Its user-friendly interface, coupled with a focus on privacy, enables a secure and unrestricted internet experience. In my NordVPN review, I found these features meet and often exceed user expectations, highlighting its proficiency in offering a balanced and versatile VPN service.
Delving deeper into NordVPN’s offerings, the service has a NordLynx tunneling protocol that provides unparalleled speeds without compromising security. Advanced encryption standards and a strict no-logs policy further solidify NordVPN’s commitment to user privacy. Its applications are designed intuitively, offering features like the Meshnet at no additional cost, making NordVPN an attractive option.
Despite NordVPN’s overall firm performance, some users have reported minor glitches following software updates, which raises concerns. Moreover, investigations have revealed concerns regarding privacy and transparency. While these issues are not deal-breakers for many, they warrant consideration for those prioritizing absolute privacy and openness from their VPN provider.
I have conducted tests on VPN to address concerns about whether is NordVPN trustworthy. Based on my extensive research and the tests conducted, NordVPN is a secure and user-friendly VPN. Also, like other best VPNs, it offers strong privacy, blazing-fast speed, and an extensive server network.
Ranked #3 out of 56 VPNs
We have spent thousands of hours and days testing 160+ VPN services using our carefully curated testing process to recommend you the best VPN. Here are a few statistics:
-
 Total Hours of Testing1000+
Total Hours of Testing1000+
-
 Weekly Speed Tests110
Weekly Speed Tests110
-
 VPN Services Reviewed160+
VPN Services Reviewed160+
-
 Streaming Platforms Tested Daily50+
Streaming Platforms Tested Daily50+
-
 IP & DNS Leak Tests Performed100+
IP & DNS Leak Tests Performed100+
-
 How Much we have spent on testing$30,000+
How Much we have spent on testing$30,000+
NordVPN Review: NordVPN Pros and Cons
- RAM-only Server Infrastructure
- Unmatched Speed
- Bypasses ISP Throttling
- Meshnet Feature
- User-Friendly Apps
- Robust Security
- Streaming Freedom
- Torrent-Friendly
- Responsive Customer Support
- Cyber Protection
- Apple TV VPN App
- Competitive Pricing
- Risk-Free Trial
- No GUI for Linux
- Absence of a Free Plan
- Restrictions on Connections
NordVPN Review: Latest Updates
NordVPN’s commitment to progress is demonstrated through its continuous series of updates and enhancements. Here’s a timeline of recent significant updates in Nord VPN’s technology:
17th Jan 2024: NordVPN for Browser Extension 3.7
This update focuses on refining the app with subtle adjustments and minor bug fixes, ensuring a smoother browsing experience.
17th Jan 2024: NordVPN for macOS 8.15.1
The Meshnet feature in this update enhances file-sharing capabilities, making them resilient to connection losses. File transfers now resume from where they stopped once you or your recipient regain connectivity.
17th Jan 2024: NordVPN for Linux 3.17.0
This version allows you to personalize your Meshnet devices with custom nicknames, simplifying device identification and management.
12th Jan 2024: NordVPN for Android 6.24-6.26
Focused on user experience, this update brings improvements and fixes, elevating the overall performance of NordVPN on Android devices.
10th Jan 2024: NordVPN for iOS 8.21
An innovative feature lets you sort the country list by popularity, enabling quick connections to the most frequented destinations without the need to scroll extensively.
21st Dec 2023: NordVPN for Windows 7.17
This version sees Threat Protection Lite rebranded as “DNS filtering” under the “Web protection” umbrella. It continues to offer robust protection against online threats, with a name that more accurately represents its defensive capabilities.
Each of these updates reflects NordVPN’s dedication to enhancing security, functionality, and user experience, solidifying its position as a leader in VPN technology.
Quick Summary of NordVPN Features
Here is a quick summary of NordVPN’s features:
 |
|
| Servers | 6000 |
| Countries | 61 |
| NordVPN Price | $3.99/mo - Save up to 63% with exclusive 2-year plan + 3 months free for a friend |
| Money Back Guarantee | 30 Days |
| Free Trial | 7 Days on Mobile |
| Simultaneous Connections | 6 |
| Compatible Devices | iOS, Android, macOS, Windows, FireStick, Smart TVs, Gaming Consoles, routers |
| Speeds | 80+ Mbps (on 100 Mbps) |
| Keeps Logs | No |
| DNS Leak Protection | Yes |
| Kill Switch | Yes |
| Where is NordVPN based | Panama |
| P2P Support | Yes |
| Customer Support | 24/7 Live Chat Support |
| Other Features | Threat Protection, Meshnet, Incogni, Dark Web Monitor, SmartPlay, Presets |
NordVPN Pricing Plans – How much does NordVPN really cost?⭐8.5
NordVPN price structure is designed to accommodate a variety of user needs and preferences, offering different tiers for different levels of service. Here is how much is NordVPN costs:
| Standerd Plans | Plus Plans | Ultiamte Plans | |
|---|---|---|---|
| Monthly Plan | $12.99 | $13.99 | $17.99 |
| Annual Plan | $4.39 per month (paid annually) | $5.49 per month (paid annually) | $9.49 per month (paid annually) |
| Two-year Plan | $2.99 per month (paid every two years) | $3.99 per month (paid every two years) | $7.99 per month (paid every two years) |
| Password Manager for Cross Channels | No | Yes | Yes |
| Scanner for Data Breach | No | Yes | Yes |
| 1TB Encrypted Cloud Storage | No | No | Yes |
NordVPN costs start at $12.99, which is a higher price than other VPN services. This might be a consideration for those seeking a short-term VPN solution without committing to a lengthy contract.
However, NordVPN mitigates this by offering a 30-day money-back guarantee, ensuring a risk-free trial period for new users. For those looking into more extended usage, NordVPN presents attractive discounts on its annual and biennial plans, aligning with the best VPN deals available.
Additionally, NordVPN cost accommodates a variety of payment methods, making subscriptions more accessible. These include NordVPN PayPal, Apple Pay, Amazon Pay, and various cryptocurrencies.
Does NordVPN offer a free trial?
You can get NordVPN free trial across all platforms. However, it compensates for this by providing a 30-day money-back guarantee for all its subscription plans. This policy ensures that if you’re not satisfied with the service, you can request a full refund, provided that the request is made within 30 days of the initial payment.
For Android users, there’s an exception: NordVPN offers a 7-day free trial exclusively through the Google Play Store. This trial allows you to test the full capabilities of the VPN before committing to a purchase. It’s important to note that Google Play manages this offer, and you’ll be subject to its specific Terms and Conditions.
How do I get my 30-day NordVPN refund?
To initiate your 30-day NordVPN refund, simply reach out to the NordVPN customer support team. They are available to guide you through the refund process, ensuring it’s straightforward and hassle-free. If your purchase was made through Apple’s App Store, you would need to contact Apple customer support directly to process your refund.
It’s important to note that you are not required to provide a specific reason for requesting a refund. NordVPN is committed to customer satisfaction, and as long as your account has not violated any service terms and is in good standing, you will be eligible for a refund.
For more detailed instructions on how to cancel NordVPN and get a refund, follow the provided guidelines to ensure a smooth and swift refund process.
NordVPN Server Locations – How Many Servers Does NordVPN Have?⭐8.5
The NordVPN server is spread all over the glog. It boasts an extensive network of servers spanning over 6000 servers in 61 countries worldwide, ensuring users have access to a vast array of options for secure and fast internet connections.
Below, you’ll find the total count of servers available.
| Region | Number of countries | Server Count |
|---|---|---|
| Asia | 15 countries | ~450 servers |
| Americas | 8 countries | ~2400 servers |
| Europe | 39 countries | ~2100 servers |
| Africa and the Middle East | 4 countries | ~200 servers |
The NordVPN server list is quite extensive, which is great for finding a connection almost anywhere. But if you’re looking for coverage in a wide range of countries, you might also consider ExpressVPN, which has 3000+ servers in 105+ countries and over 160 locations.
NordVPN impresses with more than 5,000 servers available. What I find really helpful is how NordVPN breaks down the server info on their website. They clearly list how many servers are in each category, making it super easy to pick the right one for what you need.
NordVPN Security Test – Is NordVPN Really Secure?⭐9.0
NordVPN stands out as a highly secure VPN option, mainly due to its strategic headquarters in Panama, a country not affiliated with international surveillance alliances. This geographic advantage ensures that NordVPN operates outside the jurisdiction of the more invasive data retention laws found in other countries.
NordVPN commits to not tracking any user web activity or IP addresses, providing a solid layer of privacy for its users. The encryption standard AES-256 is top-notch and considered virtually unbreakable, making NordVPN one of the best secure VPN provider choices for those prioritizing their online security and anonymity.
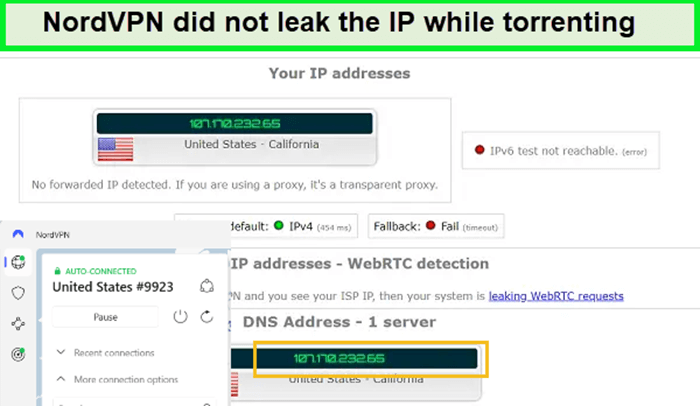
DNS, IP Leak, and WebRTC Leak Tests
DNS, IP, and WebRTC leaks are crucial for security. A VPN hides your DNS information, IP address, and WebRTC information, thereby ensuring your online activities and identity remain private.
A VPN that passes these tests provides strong assurance of maintaining a secure and private online presence. NordVPN, known for its robust security features, includes built-in leak protection, an essential aspect of its service offering.
NordVPN doesn’t leak DNS, IP, and WebRTC. Here are the NordVPN test results:
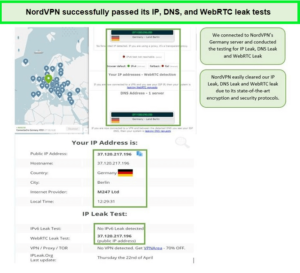
As you can see, the IP did not get leaked after connecting to its German server.
In my commitment to thoroughly test services before recommending them, I conducted DNS, IP Leak, and WebRTC leak tests using NordVPN. I specifically used NordVPN’s German server for these tests. The results were reassuring – no leaks were detected. This performance confirmed NordVPN’s claim of providing a secure online environment.
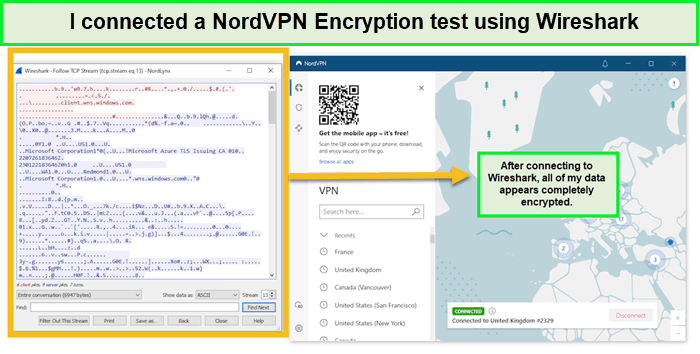
Encryption Test – How encrypted is NordVPN?
NordVPN employs AES 256-bit encryption, which is the same standard used by numerous government bodies, including the NSA. This encryption level is currently considered unbreakable with the technology available.
NordVPN also uses the AES-256-CBC cipher with a 2048-bit DH key, widely recognized as the industry’s strongest encryption. Additionally, NordVPN’s use of Perfect Forward Secrecy, which assigns unique keys for each session, adds an extra layer of privacy and security.
The test of NordVPN’s encryption, and here is the NordVPN result:
To verify the effectiveness of NordVPN’s encryption, I conducted a test using Wireshark for packet tracing. The test focused on examining the encrypted data traffic while connected to NordVPN. The results were as expected: the data appeared as indecipherable gibberish, thereby confirming the integrity of NordVPN’s encryption. This test not only assured me of NordVPN’s encryption capabilities but also reinforced my trust in their security measures.
What VPN Protocol does NordVPN Use?
NordVPN incorporates a range of VPN protocols known for their security and reliability, including IKEv2/IPsec and OpenVPN. In 2020, NordVPN introduced NordLynx, developed around the innovative WireGuard protocol, offering users a cutting-edge option for their VPN connections.
| Protocols | Key Features |
|---|---|
| OpenVPN | Versatile, all-around security |
| IKEv2/IPsec | Optimized for mobile devices, cellular/Wi-Fi data |
| NordLynx | Best option overall |
OpenVPN (UDP/TCP): A widely-used open-source VPN protocol, OpenVPN offers a secure, multi-platform solution. NordVPN allows you to select between TCP for reliability and UDP for speed, catering to your needs. This protocol is supported across all NordVPN applications.
IKEv2/IPsec: This protocol shines on mobile devices with minimal CPU impact and swift reconnection capabilities when transitioning between Wi-Fi and cellular networks. It’s compatible with various operating systems, including iOS, Windows, Linux, and macOS, offering user flexibility across devices.
For Ubuntu users specifically, this makes NordVPN an ideal option, securing its position as the secure best VPN for Ubuntu and ensuring reliable and efficient performance for on-the-go connectivity.
WireGuard (NordLynx): NordVPN’s custom adaptation of the next-generation WireGuard technology combines enhanced speed and security. NordLynx is an improvement over older protocols, offering superior performance, and is available on all NordVPN clients.
Note: When manually setting up a VPN connection on Windows, be wary of potential DNS leaks, especially with IKEv2 connections. Setting NordVPN’s DNS addresses as the default on my Ethernet and IKEv2 adapters resolved any DNS leak issues, a crucial step for those opting for a manual configuration. Ensure the use of NordVPN’s DNS servers to maintain secure and uninterrupted service.
What is SmartPlay on NordVPN?
SmartPlay is a feature offered by NordVPN designed to seamlessly unlock access to geo-restricted content, allowing you to enjoy a wider range of media securely. This technology integrates the capabilities of a VPN with smart DNS services to bypass content restrictions without compromising security or speed, making it an efficient solution for streaming international content.
What are the different specialty servers on NordVPN?
If you want to use NordVPN for a specific purpose, then its optimized servers are your best options. Here’s a brief description of NordVPN’s specialty servers:
- Double VPN servers – Double VPN is an advanced VPN security feature that routes your traffic through two VPN servers instead of one, encrypting your data twice. NordVPN has 90+ servers that offer a Double VPN security feature.
- Dedicated IP servers – A dedicated IP address is assigned entirely for your use. Unlike a shared IP distributed to many users, a dedicated IP is unique to your account — no one else can use it. NordVPN has 190+ servers for dedicated IP addresses.
- Standard VPN or Shared IP address – The shared IP address or standard VPN service is referred to the IP addresses or servers that the NordVPN subscribers share. You can use these servers on Six devices simultaneously. NordVPN has 6000+ servers for standard VPN.
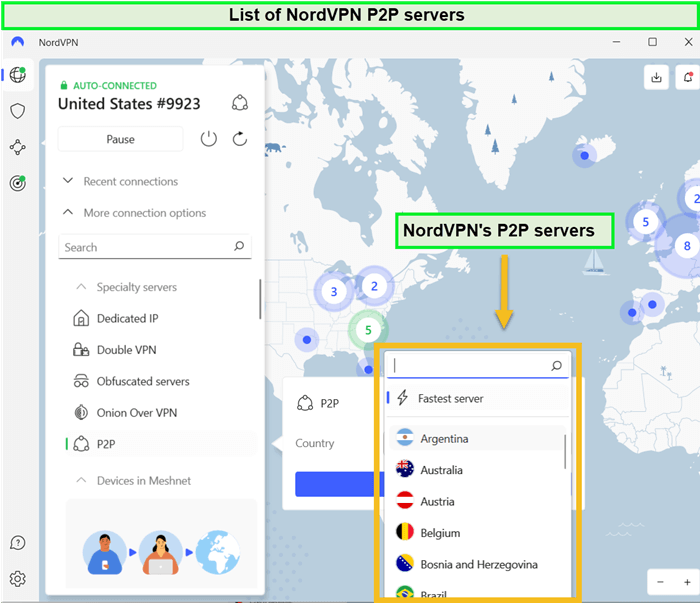
- P2P servers – These servers are specifically designed for P2P/Torrenting/File-sharing purposes. NordVPN offers special P2P servers for users. However, the precise number of servers is not provided.
- Obfuscated servers – These servers are fully capable of hiding the fact that you are using a VPN to reroute your traffic. They are quite handy in environments with heavy censorship restrictions, such as Iran, Russia, and China. NordVPN has 150+ obfuscated servers.
NordVPN Presets
A preset combines unique VPN connection settings with app or website shortcuts. This combination provides safe, VPN-protected access to your favorite online services from the NordVPN app.
You’ll find this feature highly useful if you’re using different VPN servers for different purposes. You can also utilize pre-made presets. Keep in mind that the Presets feature is only available for macOS.
What is NordVPN Meshnet?
NordVPN Meshnet is a cutting-edge feature. It allows users to create a private and secure virtual network that connects multiple devices directly, irrespective of their physical location.
This means that devices connected through Meshnet can communicate with each other as if they were on the same local network. The feature enables seamless file sharing, remote desktop access, and private communication between devices, all encrypted and routed through NordVPN’s secure servers.
The ability to link my devices directly has streamlined my workflow, especially in scenarios where remote access to files and systems is crucial. I’ve used Meshnet for accessing my home computer from work and for setting up a secure communication channel with colleagues located in different parts of the world. The setup was straightforward, and the connection has been consistently stable and fast.
NordVPN Security – Does NordVPN Offer any Advanced Security Features?⭐9.0
Yes, NordVPN offers advanced security features, including innovative Threat Protection. This feature enhances your online security by safeguarding your data and devices from malware, serving as a robust layer of protection even if you’re not using separate antivirus software.
Further, to check whether is NordVPN safe and secure, I used new features and wrote my reviews about these features.
Threat Protection
NordVPN’s Threat Protection feature is designed to shield users from various online threats. It actively prevents access to malicious websites, ensuring users don’t inadvertently visit harmful pages.
Additionally, it blocks intrusive online ads and trackers, thus enhancing browsing privacy. The feature also includes a malware scanner for downloadable files, and it’s available across all NordVPN applications, including as a standalone feature for browsers.
The NordVPN Threat protection feature has significantly improved my online browsing experience. The ad and tracker-blocking capabilities have made web browsing smoother and more private. The malware scanning functionality provided peace of mind when downloading files. Overall, this feature has been a valuable addition to NordVPN’s suite of security tools, offering comprehensive protection in a convenient package.
Dedicated IP
NordVPN offers a Dedicated IP service, which allocates a consistent IP address to a user. This feature is particularly useful for those who need stable and predictable online access, as it offers the benefits of a VPN without frequently changing IP addresses. It can be particularly beneficial for accessing certain online services that require IP consistency.
While I typically prioritize anonymity in my VPN use, the Dedicated IP option from NordVPN has been a game-changer for certain activities. It’s proven invaluable for accessing online services that require a consistent IP address. The seamless process to acquire and use a Dedicated IP through NordVPN’s official site has added a level of convenience to my VPN experience.
Kill Switch

NordVPN did not leak actual IP due to automatic Kill Switch future
The Kill Switch feature is a crucial aspect of NordVPN’s service. It automatically disables internet or specific app access if the VPN connection drops, protecting the user’s IP address and location from being exposed. NordVPN offers both a system-wide and an app-specific Kill Switch, providing tailored protection for different devices and use cases.
The NordVPN Kill Switch has been a key factor in maintaining my online privacy. I’ve found the app-specific Kill Switch particularly useful, as it allows me to control the protection for certain apps without disrupting my entire internet connection. This feature has consistently worked seamlessly, ensuring that my sensitive data is never exposed, even during brief connection losses.
Split Tunneling
Split Tunneling allows users to choose which apps use the VPN connection and which connect directly to the internet. This functionality is especially handy for using trusted applications without VPN interference. NordVPN supports Split Tunneling on Windows and Android platforms, balancing usability and security.
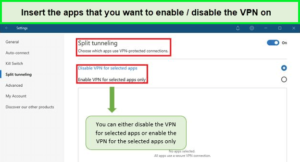
I easily enabled the NordVPN Split tunneling feature on my device
NordVPN Split Tunneling feature has significantly enhanced my VPN experience. It’s particularly beneficial when I need a direct connection for certain apps while keeping others protected. The ability to customize which apps bypass the VPN has made a noticeable difference in both the speed and functionality of my internet use.
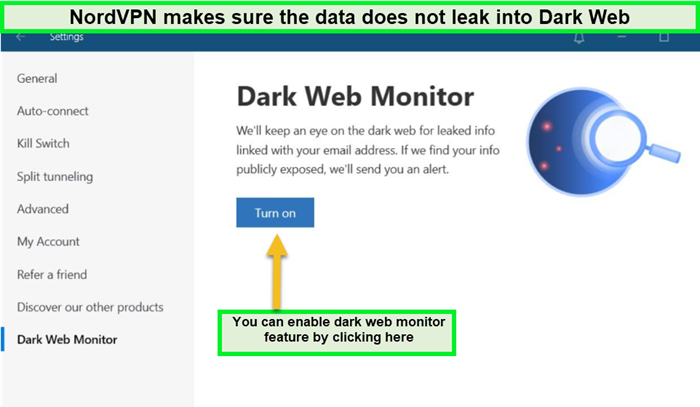
Dark Web Monitor
The Dark Web Monitor is a proactive security feature from NordVPN. It alerts users if their personal data is detected on dark web marketplaces, indicating a potential security breach. This feature is available across iOS, Android, Windows, and macOS, adding an additional layer of preemptive security to NordVPN’s offerings.
Cyber Protection
Launched in December 2023, NordVPN’s Cyber Protection integrates insurance-backed security features within its Ultimate bundle. This package offers up to $1 million in reimbursement for online identity restoration and up to $100,000 for cyber extortion expenses. It highlights NordVPN’s commitment to providing extensive protection for its users.
The introduction of Cyber Protection has significantly elevated NordVPN’s value proposition. The insurance-backed features, especially the substantial coverage for identity restoration and cyber extortion, provide an unprecedented level of security. This package has made NordVPN not just a VPN service but a comprehensive online protection tool.
Pausing and Auto-connect
NordVPN’s auto-connect feature simplifies connectivity by automatically engaging the VPN upon device startup, ensuring uninterrupted protection. The pause functionality allows temporary direct access when needed, providing flexibility and continuous security.
NordVPN App’s Security Audit
It’s not the first time the company has carried out a third-party audit. In fact, after the no-logs policy audit conducted in 2018, the VPN decided to carry it out for the 2nd time through one of the Big Fours in May 2020. After the exhaustive testing procedure carried out by professionals, the results were positive. The practitioners ensured that the VPN doesn’t compromise on its no-logs promise in any way.
Previously, this VPN carried out another audit in October 2019, but for its apps. An independent auditing firm named VerSprite specializes in finding vulnerabilities, risks, and threats in application software and performs penetration tests based on real-world attack scenarios on NordVPN’s iOS and Android apps.
According to Laura Tyrell, Head of Public Relations at NordVPN, the vulnerabilities pointed out by the auditing firm were addressed, and a few changes were made accordingly. This shows NordVPN’s commitment to maintaining a flawless VPN service.
NordVPN Security Breach Incident
Despite a security breach in October 2021, NordVPN has maintained its status as one of the industry’s most secure VPNs. The incident led to strengthened security protocols, including the Dark Web Monitor, ensuring NordVPN remains a trusted choice for secure online activities.
| Security Features | NordVPN | ExpressVPN | Surfshark |
|---|---|---|---|
| CyberSec | Yes | Yes | Yes |
| Automatic Reconnect | Yes | Yes | Yes |
| Internet Kill Switch | Yes | Yes | Yes |
| Split Tunneling | Yes | Yes | Yes |
| Custom DNS | Yes | No | No |
| Obfuscated Servers | Yes | Yes | Yes |
| Invisibility on LAN | Yes | No | No |
NordVPN clearly takes the win as it provides multiple additional security features for its user’s online privacy and anonymity.
While I always root for services that offer multiple security features to their clients, one thing I particularly appreciate is having a separate place for the ‘connection protocol’ selection. Beyond this, I don’t believe they need to do anything else.
NordVPN Privacy – Does it Protect your Online Privacy?⭐8.5
NordVPN stands out as one of the most reputable providers in the VPN market, dedicated to enhancing your online privacy. It secures data transfer with AES-256-bit encryption, ensuring a high level of security for your online activities. Additionally, NordVPN provides a comprehensive suite of privacy-boosting features, making it a robust choice for protecting your online presence.
Where is NordVPN located?
NordVPN is strategically headquartered in Panama, far from the intrusive jurisdictions of the 5 EYES, 9 EYES, 14 EYESintelligence alliances. Panama’s absence of mandatory data retention laws means NordVPN is not required to store logs, reinforcing its commitment to user privacy and making it an exemplary choice for those concerned about international surveillance.
Does NordVPN keep logs?
NordVPN has undergone independent audits to validate its commitment to user privacy. These audits have consistently confirmed NordVPN’s adherence to its no-logs policy, ensuring that users’ online activities remain private and untracked. This commitment reflects NordVPN’s dedication to maintaining user confidentiality and trust.
The independent audit results have reinforced my confidence in NordVPN logging policy. Knowing that NordVPN is not logging my online activities is crucial for my peace of mind, especially in an era where digital privacy is increasingly important.
What is NordVPN Warrant Canary?
The NordVPN Warrant Canary serves as a transparent indicator that the company has not received any secret government or law enforcement requests for user data. It’s a testament to the commitment to data privacy, assuring users that their information remains secure from government surveillance.
As of 2024, we:
- We have NOT received any National Security letters;
- We have NOT received any gag orders;
- We have NOT received any warrants from any government organization.
NordVPN hasn’t received any warrants so far as of 2024. You will find this information at the very bottom of their about us page.
Privacy Feature Comparison: NordVPN, ExpressVPN, and Surfshark
Here’s a comparison table about the privacy features of NordVPN, ExpressVPN, and Surfshark.
| Privacy Features | NordVPN | ExpressVPN | Surfshark |
|---|---|---|---|
| Jurisdiction | Panama (Safe) | The British Virgin Islands (Safe) | The Netherlands (Safe) |
| No-log policy | Yes | Yes | Yes |
| Warrant Canary | Yes | No | Yes |
| AES-256-Bit Encryption | Yes | Yes | Yes |
I’ll be honest: I had my doubts regarding NordVPN’s privacy due to the security breach incident that occurred in the past. However, after seeing the security test results and the establishment of NordVPN’s Warrant Canary, I now believe they are safe and completely capable of protecting my online privacy.
NordVPN Speed and Performance – How Fast is NordVPN⭐8.0
In my evaluation, NordVPN stands out as one of the fastest VPNs available based on comprehensive testing. I subjected it to a rigorous examination on my 100 Mbps internet connection, spanning various server regions. Remarkably, NordVPN consistently delivered blazing-fast download speeds, averaging an impressive 85 Mbps.
Breaking down the results by region, it becomes evident that NordVPN meets and exceeds expectations, outperforming many other high-speed VPN providers. With NordVPN, I can confidently engage in streaming, downloading, and browsing activities without concerns about potential ISP throttling compromising my bandwidth.
My extensive NordVPN speed test clearly demonstrates its unwavering stability and commendable speeds, particularly when tested on a 100 Mbps connection in one of my US-based testing labs.
NordVPN’s Double VPN Speed Test
When connecting to NordVPN’s Double VPN servers, I experienced a substantial drop in speed, nearly 50%. Initially, without the Double VPN feature, I achieved a maximum speed of 96.92 Mbps. However, upon connecting to the US > Canada server with Double VPN enabled, my download speed peaked at only 53 Mbps.
Surprisingly, this drop in speed persisted when I switched to the Switzerland > Sweden server, where I still reached a maximum download speed of only 51.14 Mbps.
| Server Location | Download Speed | Upload Speed | Speed – (%) Drop |
|---|---|---|---|
| Australia | 70 Mbps | 73.25 Mbps | 30% |
| Brazil | 79.92 Mbps | 75.5 Mbps | 20.08% |
| Germany | 82 Mbps | 80.67 Mbps | 18% |
| Hong Kong | 69 Mbps | 71.09 Mbps | 31% |
| Israel | 78.09 Mbps | 73.75 Mbps | 21.91% |
| Japan | 71.25 Mbps | 73.41 Mbps | 28.75% |
| Singapore | 75.59 Mbps | 79.09 Mbps | 24.41% |
Speed Comparison : NordVPN, ExpressVPN, and Surfshark
When evaluating VPN services, one of the critical factors for many users is speed. In the comparison of NordVPN, ExpressVPN, and Surfshark, each has its strengths, but it’s important to consider how these services balance speed with security.
NordVPN, known for its robust security features, including the Double VPN option, shows commendable performance in speed tests. Although using Double VPN can reduce speed by about 50% due to the extra layer of encryption, the speed reduction is a reasonable trade-off for the increased security it offers.
This slight dip in speed is understandable and acceptable, especially considering the multiple security features NordVPN offers that are not readily available with other providers.
| Server Location | NordVPN | ExpressVPN | Surfshark |
|---|---|---|---|
| Australia | 70 Mbps | 79.25 Mbps | 75.36 Mbps |
| Brazil | 79.92 Mbps | 80.5 Mbps | 80.15 Mbps |
| Germany | 82 Mbps | 80.67 Mbps | 81.27 Mbps |
| Hong Kong | 69 Mbps | 71.09 Mbps | 70.39 Mbps |
| Israel | 78.09 Mbps | 73.75 Mbps | 75.65 Mbps |
| Japan | 71.25 Mbps | 73.41 Mbps | 72.71 Mbps |
| Singapore | 75.59 Mbps | 79.09 Mbps | 76.72 Mbps |
In terms of raw speed, ExpressVPN and Surfshark both offer competitive performance. However, when choosing a VPN, one must consider the balance between speed, security, and other features like server availability and user interface.
For those who prioritize speed in their VPN selection and are looking for detailed comparisons with other providers, I have conducted extensive reviews. If you’re considering alternatives to NordVPN for speed-optimized VPN services, the following comparisons might help in making an informed decision:
NordVPN vs Hotspot Shield: This comparison delves into how NordVPN stacks up against Hotspot Shield, particularly in terms of speed, server availability, and overall performance.
NordVPN vs Proton VPN: Here, I explore the differences between NordVPN and Proton VPN, focusing on speed metrics, security features, and user experience.
NordVPN vs. Surfshark: This detailed review compares NordVPN with Surfshark, analyzing aspects such as speed and security protocols and their impact on streaming and torrenting capabilities.
ExpressVPN vs. NordVPN: This review outlines NordVPN and ExpresVPN’s compatibilities, analyzing speed, server range, security protocols, and their impact on streaming and torrenting capabilities while maintaining robust security protocols.
NordVPN performance with other protocols
I tested NordVPN’s varying speeds with different VPN protocols using a 100 Mbps internet connection as my base speed. Here are the results:
- NordLynx: Achieved a download speed of 91 Mbps and an upload speed of 54 Mbps.
- OpenVPN (UDP): Recorded a download speed of 79 Mbps and an upload speed of 65 Mbps.
- OpenVPN (TCP): Showed a download speed of 44 Mbps and an upload speed of 35 Mbps.
- IKEv2: Delivered a download speed of 83 Mbps and an upload speed of 77 Mbps.
Notably, NordLynx provided the fastest speeds, while the older protocols still offered fast speeds, with IKEv2 coming close to NordLynx. The speed drop varied from 9% to 88%, depending on the protocol and server distance. OpenVPN (TCP) showed considerably slower speeds compared to OpenVPN (UDP).
Here’s a summarised version:
| Protocol | Speed | Security | Connection Stability |
|---|---|---|---|
| NordLynx | Fastest | High | Stable |
| OpenVPN (UDP) | Faster | Medium | Stable |
| OpenVPN (TCP) | Slow | High | Fluctuates |
| IKEv2 | Faster | High | Good enough |
Overall, NordVPN is quite fast, especially if you’re near the connected server, where speed drops are minimal. However, for optimal performance, consider using NordLynx, which consistently provides the fastest speeds.
How does NordVPN work?
With NordVPN, it’s as simple as a click on the Connect button after logging in. This action swiftly conceals your IP, replaces it, and secures your data in an encrypted tunnel. This means no one can track your online activity – not your ISP, not the government, and not third parties. NordVPN’s strength extends to effortlessly unblocking geo-restricted content, making it perfect for streaming and more.
All the essential features, from robust encryption to optimized tunneling protocols, are conveniently found in Preferences. NordVPN’s user-centric design removes technical complexities, providing comprehensive protection within a few clicks. It’s available on various platforms, ensuring a consistent, user-friendly experience across devices. Below, discover guides for effortless NordVPN setup and usage.
Is NordVPN Good For Gaming
Yes, NordVPN is excellent for gaming, and let’s delve into the standout features that not only position it as a top choice but also address the question of how good is NordVPN truly is:
Encrypt your traffic: NordVPN uses top-notch encryption algorithms to protect your data, ensuring a secure gaming experience and shielding you from snoopers.
Avoid bandwidth throttling: Some games may suffer from unencrypted sensitive content, but with NordVPN, you can take charge of your data security. NordVPN encrypts your online traffic, providing a protective shield against potential threats.
Easy interface: NordVPN boasts a user-friendly interface, making it incredibly straightforward to use. Connect to your preferred server with a single click or utilize the Quick Connect option to let the app choose the best server for you, ensuring a hassle-free gaming experience.
Protect your whole network: Tired of setting up a VPN on every device? NordVPN simplifies this by allowing you to safeguard your entire network. Install it on your Wi-Fi router, and all connected devices in your home will enjoy 24/7 protection.
From a user’s perspective, NordVPN not only ensures secure gaming but also effortlessly unlocks access to region-locked gaming lobbies. This elevates its status among the best VPNs for gaming, making it a top choice for avid gamers.
My gaming experience with NordVPN has been outstanding. The encryption ensures secure gameplay, and I’ve noticed a significant reduction in bandwidth throttling. The easy-to-use interface and the option to protect my entire network are particularly beneficial, allowing me to game without worrying about security or performance issues.
Is NordVPN Good for Online Streaming⭐9.0
Yes, NordVPN is indeed one of the best VPNs for streaming, offering a range of impressive features to enhance your online streaming experience.
NordVPN ensures lightning-fast connection speeds, delivering a seamless streaming experience without lags, buffering, or drops in video quality.
| Streaming Platforms | Unblocking Ability |
|---|---|
| Netflix | ✔ |
| Hulu | ✔ |
| Amazon Prime Video | ✔ |
| BBC iPlayer | ✔ |
| Disney+ | ✔ |
| HBO Max | ✔ |
| Hotstar | ✔ |
| CBS | ✔ |
| NBC Live | ✔ |
| SonyLIV | ✔ |
| ESPN+ | ✔ |
| Spotify | ✔ |
The VPN combo of NordVPN Lifetime, ABC Channel, Sling TV, and ESPN+ offers fast speeds and reliable unblocking capabilities, making it the best VPN for streaming.
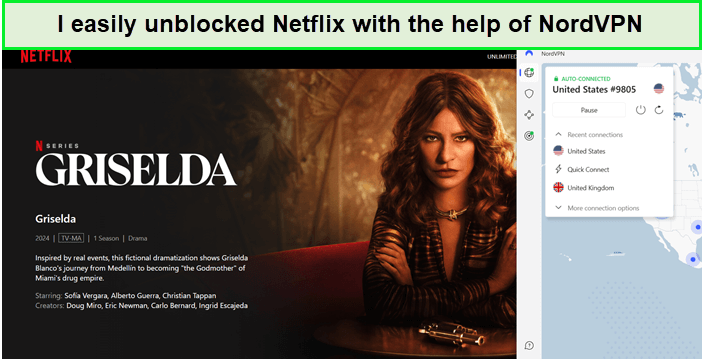
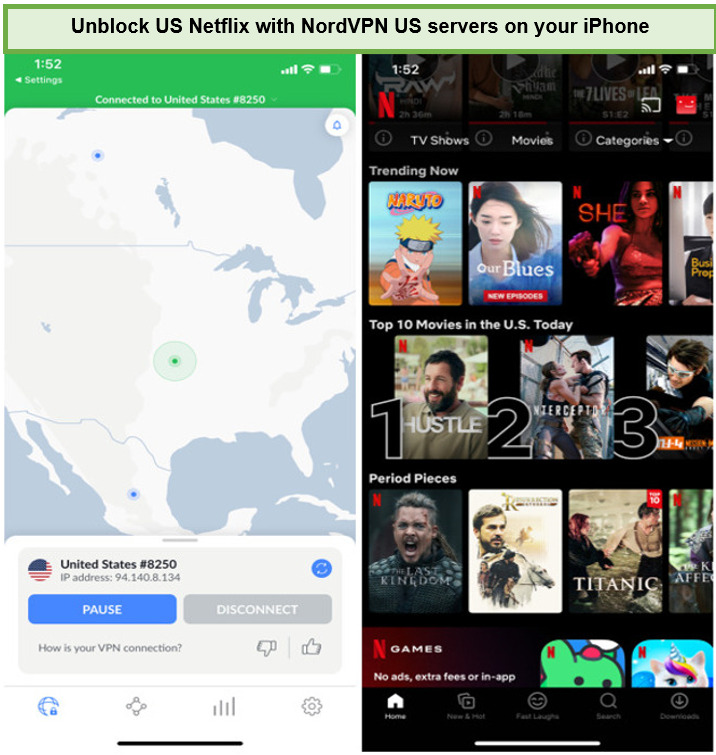
Unblocking Netflix with NordVPN
NordVPN efficiently unlocks various international Netflix libraries, allowing users to bypass geo-restrictions. This feature expands the range of available content, providing access to a broader spectrum of movies and TV shows from different regions.
Using the NordVPN Netflix combination to break the geo-restricted libraries has been a seamless experience. I’ve enjoyed content from the US, UK, Canada, and more without any geo-restriction errors, significantly enhancing my streaming experience.
NordVPN BBC iPlayer Unblock
NordVPN effectively bypasses the geo-blocking of BBC iPlayer, especially for users in the USA. The service provides access to Ultra-HD content on the platform without delays, making it a reliable choice for BBC iPlayer users.
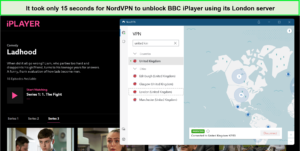
I streamed all content in HD quality without issues.
The combination of NordVPN and BBC iPlayer has been flawless. I’ve enjoyed Ultra-HD content without any buffering or delays, which is impressive considering the typical challenges of streaming such high-quality content from across the globe.
NordVPN unblocks Hulu
NordVPN offers a smooth streaming experience on Hulu, efficiently unblocking the service and reducing buffering times. The VPN’s performance on servers like the United States – Buffalo server provides a near-seamless viewing experience.
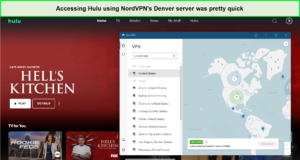
I unblocked Hulu without any delays using NordVPN.
Streaming Hulu with NordVPN has been hassle-free. The brief initial delay is a small price to pay for the otherwise buffer-free experience, making it a great choice for streaming Hulu’s exclusive content.
NordVPN unblocks Disney+
NordVPN provides access to Disney+ and its various international libraries. Connecting to servers like the United States – Denver server, users can enjoy high-definition video quality while accessing a wide range of Disney+ content.
Using Disney+ through NordVPN has allowed me to enjoy their latest TV series in HD quality. The ability to access different regional libraries has significantly expanded my viewing options.
Does NordVPN unblock HBO Max, Amazon Prime, or YouTube TV
NordVPN efficiently unblocks all the international streaming platforms, especially Amazon Prime and HBO Max. It offers swift and hassle-free access to these streaming services, with minimal loading times and uninterrupted streaming once connected to the right server.
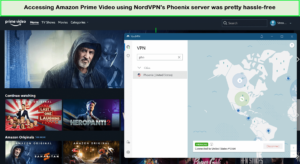
I streamed all Amazon Prime content in Ultra-HD with NordVPN.
I used NordVPN for HBO Max and Amazon Prime. On both platforms, the experience has been smooth and efficient. The streaming quality is consistent, and finding the right server for uninterrupted viewing is straightforward.
Does NordVPN work with streaming boxes?
NordVPN supports a wide range of devices and streaming boxes. You can use NordVPN Kodi, FireStick, and Roku. The service provides comprehensive instructions for easy setup, ensuring users can enjoy their favorite shows on various streaming platforms.
I’ve found using NordVPN with streaming boxes like Roku and FireStick to be a game-changer for my streaming experience. Setting up NordVPN on Roku was straightforward, and it significantly expanded my access to geo-restricted content while maintaining high streaming quality.
Similarly, NordVPN on FireStick enhanced my viewing experience by providing additional layers of privacy and security. The ability to install NordVPN directly on these devices meant that all content streamed through them was protected and unrestricted.
NordVPN Torrenting – Does NordVPN Allow Torrenting?⭐<8.5
NordVPN Torrenting is highly optimized for P2P activities, making it a secure choice for users. With dedicated 6000+ P2P servers featuring AES 256-bit encryption, data leak protection, and a kill switch, NordVPN ensures a secure torrenting experience.
NordVPN offers a selection of P2P-optimized servers in 47 countries, including Switzerland, Poland, Canada, Spain, and the Czech Republic, ideal for regions with strict torrenting regulations. Its server network of over 6000 servers is available for P2P file sharing, automatically redirecting to a P2P-compatible server if torrenting activity is detected on a non-P2P server.
In my testing, NordVPN Torrenting capabilities were exceptional, facilitating the smooth download of large files without significant speed losses. The VPN’s automatic server switch for torrenting activities underscores its reliability and ease of use for P2P file sharing.
On the Internet Service Provider’s connection, I receive an average of 15 MB/s speed in the uTorrent client.
| P2P Server | Download speed | File download – ETA | Speed – (%) drop |
|---|---|---|---|
| Canada | 14.94 Mbps | 5 min 18 sec | 0.4% |
| Brazil | 13.21 Mbps | 7 min 11 sec | 11.93% |
| Germany | 13.97 Mbps | 6 min 23 sec | 6.86% |
| Netherlands | 13.73 Mbps | 7 min 0 sec | 8.46% |
| Sweden | 12.84 Mbps | 8 min 53 sec | 14.4% |
| Australia | 10.01 Mbps | 10 min 45 sec | 33.26% |
| Singapore | 11.32 Mbps | 9min 39 sec | 24.53% |
While I was convinced that NordVPN allows torrenting, I also wanted to see proof of security while downloading torrents with NordVPN. So, I took another security test to confirm that the connection was really secure for torrenting.
Further, a security test confirmed NordVPN’s effectiveness in protecting P2P activities, passing the Torrent Address Detection test. This affirms NordVPN as a safe and secure choice for torrenting, with its comprehensive P2P support and robust security features.
Torrenting Features Comparison: NordVPN, ExpressVPN, and Surfshark
Let’s look at some of the competitors that support torrents and see what they offer compared to NordVPN:
| P2P | NordVPN | ExpressVPN | Surfshark |
|---|---|---|---|
| P2P Support | Yes | Yes | Yes |
| Number of P2P Servers | 6000+ | 3000+ | 3200+ |
| Internet Kill Switch | Yes | Yes | Yes |
NordVPN distinguishes itself with an impressive number of dedicated P2P servers. This extensive server network is crucial for efficient and reliable torrenting, providing users with optimized speeds and reduced risk of connection drops. Furthermore, NordVPN’s commitment to security is evident in its additional features, such as strong encryption and a strict no-logs policy, which are particularly important for safe torrenting practices.
For those interested in how NordVPN compares to specific competitors in the realm of torrenting, I’ve conducted in-depth analyses:
NordVPN vs. VyprVPN: This comparison sheds light on how NordVPN stands against VyprVPN, focusing on aspects such as P2P server availability, torrenting speeds, and the overall security infrastructure of both providers.
NordVPN vs. CyberGhost: In this review, I delve into the differences between NordVPN and CyberGhost, examining their respective strengths and weaknesses in supporting torrent activities, with a special emphasis on server networks and additional security measures.
These comparisons aim to provide a comprehensive understanding of NordVPN’s torrenting capabilities relative to VyprVPN and CyberGhost, helping users determine which VPN service best suits their torrenting needs while ensuring a secure and efficient experience.
NordVPN Compatibility – What Devices Does NordVPN Support?⭐<9.0
NordVPN stands out in the VPN market for its extensive compatibility with a wide array of devices, ensuring users can secure their internet connection regardless of their chosen platform. This compatibility encompasses a variety of operating systems and devices, making NordVPN a versatile choice for diverse user needs.
Primarily, NordVPN offers robust applications for all major operating systems, making it among the best VPNs for multiple devices, including Windows, macOS, Linux, Android, and iOS. Each application is tailored to the specificities of its operating system, ensuring optimal performance and user experience. Whether it’s a PC, a smartphone, or a tablet, NordVPN provides a secure and user-friendly solution.
Here’s a list of all the devices that NordVPN is compatible with:
| Windows | Android |
| macOS | iOS |
| Linux | Android TV |
| Chrome | Firefox |
| Edge | Others |
For those who prefer browser extensions, NordVPN extends its services to Chrome and Firefox users. These extensions are lightweight and efficient, providing quick VPN access and essential features like WebRTC leak protection directly in your browser.
In my experience, the broad device compatibility of NordVPN has been a significant advantage. I’ve seamlessly used NordVPN across different devices and operating systems without any compatibility issues. The ease of installing and using NordVPN on both my laptop and smartphone, coupled with the ability to secure my entire home network via router installation, has provided a comprehensive security solution.
The browser extensions have been particularly useful for quick browsing sessions, offering both convenience and security. Additionally, using NordVPN with my streaming devices like FireStick and exploring the Roku NordVPN combination has opened up a world of content that was previously inaccessible due to geo-restrictions.
The ease with which I could set up NordVPN on my Roku device further illustrates the service’s versatility. NordVPN’s adaptability across these various platforms, including the seamless integration with Roku, showcases its commitment to providing a user-friendly and secure internet experience for everyone, regardless of their device preference.
Is NordVPN Easy to Use?⭐<9.0
Yes, NordVPN is incredibly user-friendly. Simply open the app, hit “Quick Connect,” and you’ll be linked to the nearest and fastest server within seconds. This ensures your connection remains private and your IP address is hidden, enhancing your online anonymity:
Here’s a summarised version of the experience with each platform:
| Platform | Experience |
|---|---|
| iOS | Overall, I had a good experience using on iPhone and iPad |
| Android | The app worked fine mostly, except for a few connectivity issues |
| Windows | Worked quite well. Easy to use and friendly UI. |
| macOS | Offers two different versions of the app with unique features. |
| Linux | It is an open-source app that works through the terminal. GUI isn’t available. |
| Browser | The extension works well on Google Chrome and Firefox |
| Router | The app is compatible with routers that support the OpenVPN protocol |
After testing, below are the detailed experience with NordVPN on major operating systems and devices. Have a look right below:
NordVPN Windows – Can I use NordVPN on Windows?
NordVPN offers a sophisticated and user-friendly client for Windows users. The application is compatible with a range of Windows versions, including Windows 11, 10, 8, and 7, ensuring broad accessibility.
Key features include split tunneling, a kill switch, and a variety of protocol options like NordLynx and OpenVPN (TCP/UDP). The interactive map interface enhances user experience, allowing easy connection to servers worldwide. For IKEv2 protocol users, manual setup is available, providing flexibility in customization.
Using NordVPN on my Windows devices has been a seamless experience. The installation process is straightforward, and the client’s interface is intuitive. Features like split tunneling have been particularly useful, allowing me to manage my VPN connection per app. The reliability and speed of the NordLynx protocol have been impressive, ensuring a smooth and secure online experience.
NordVPN macOS Apps
NordVPN provides two distinct macOS apps – one available directly from their website and another from the Apple App Store. Each version offers unique features: the sideload version includes split tunneling, while the App Store version supports various protocols and includes a built-in kill switch. This dual approach caters to different user preferences and needs, ensuring macOS users have access to a flexible and secure VPN solution.
As a macOS user, I appreciate the choice between the two versions of NordVPN’s app. The sideload version with split tunneling is perfect for customizing my VPN usage, while the App Store version’s simplicity and built-in kill switch offer peace of mind for security. Both versions maintain NordVPN’s standard of quality and performance.
Does NordVPN work with macOS Monterey?
NordVPN fully supports macOS Monterey, along with older versions starting from macOS 10.15 Catalina. This compatibility ensures that users with the latest macOS can benefit from NordVPN’s security and privacy features without any issues. NordVPN’s consistent updates and support for new macOS versions demonstrate their commitment to keeping up with the latest technological advancements.
NordVPN Android – Is NordVPN good for Android?
NordVPN’s Android app stands out for its user-friendliness and comprehensive feature set. The app’s clean interface simplifies server selection and provides access to features like a kill switch and Dark Web Monitoring.
It also includes the NordVPN on Android TV option, expanding its use to a wider range of Android-based devices. Supported protocols include OpenVPN (TCP/UDP) and NordLynx, with the bonus of Double VPN for extra security.
The NordVPN app on my Android device has been a stellar performer. The interface is straightforward, making it easy to connect to the best server for my needs. Features like the kill switch and Dark Web Monitoring add layers of security that are particularly important on mobile devices. The addition of NordVPN on Android TV has also been a great benefit, allowing me to secure my streaming activities easily.
NordVPN iOS – Does NordVPN work with iOS?
NordVPN offers a robust iOS app that is both user-friendly and feature-packed. It supports a range of protocols, including IKEv2, NordLynx, OpenVPN (TCP/UDP), and Double VPN, providing a comprehensive VPN experience for iPhone users. The app includes features like Dark Web Monitoring and a kill switch, enhancing security and privacy.
NordVPN’s iOS app is compatible with devices running iOS 11.0 or above, making it one of the best VPN choices for iPad, iPhone, and iPod users.
My experience with NordVPN on iPhone and other iOS devces has been exceptional. The app is easy to navigate and offers a wide range of features that cater to various needs. The variety of protocols, especially the inclusion of NordLynx, ensures fast and secure connections. The kill switch and Dark Web Monitoring features bring an added sense of security, which is crucial for mobile devices.
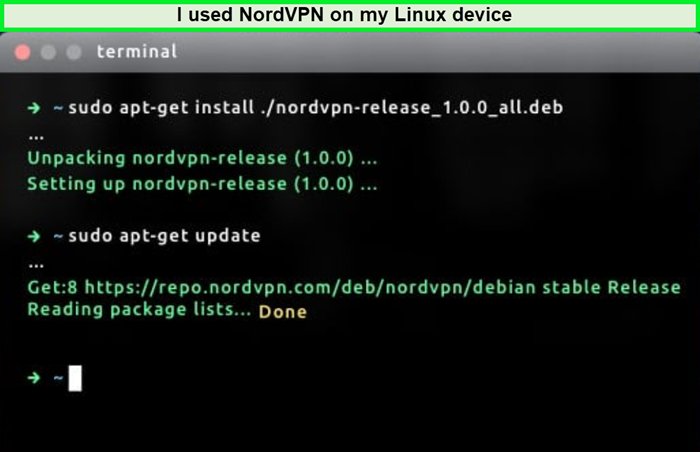
NordVPN Linux – Does NordVPN work with Linux?
NordVPN’s CLI-based applications provide comprehensive support for Linux users. While it lacks a graphical user interface (GUI), its compatibility with various Linux distributions like Ubuntu, Fedora, and Linux Mint makes it a solid choice for tech-savvy users.
NordVPN on Linux offers RPM and Debian packages and supports community-made Arch Linux ports. The Linux app is open-source and includes features like DNS leak protection and NordLynx, though it can improve its command response speed.
As a Linux user, I’ve found NordVPN’s CLI-based app quite functional. The open-source nature is a big plus, allowing the community to customize and improve it. While the absence of a GUI might be a downside for some, the DNS leak protection and the performance of NordLynx have been commendable. There’s potential for further enhancement, especially regarding user interface and response times.
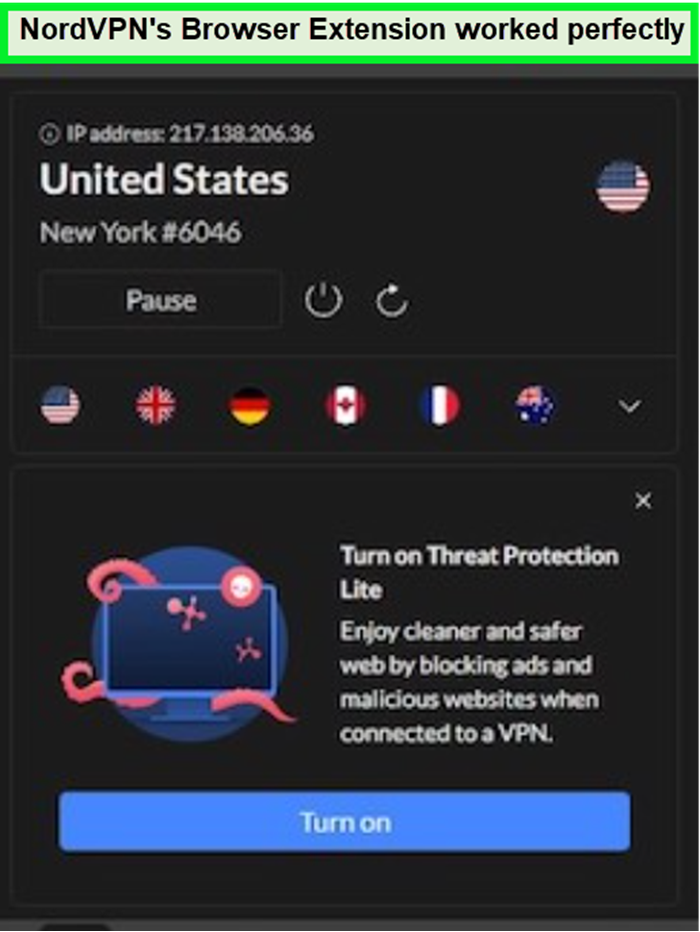
Does NordVPN have browser extensions?
NordVPN offers browser extensions for Chrome and Firefox that enhance online security. These extensions encrypt browser traffic and provide features like WebRTC leak protection and CyberSec. Users can enjoy a safe browsing experience with the added convenience of split tunneling, although this feature is not available on macOS. The extensions are particularly useful for quick and secure browsing sessions.
The NordVPN extensions for Chrome and Firefox have been indispensable tools for my online activities. The encryption and WebRTC leak protection ensure my browsing is secure, and the CyberSec feature effectively blocks unwanted ads and potential threats. The ease of use and the added security these extensions provide make them a valuable addition to my online security toolkit.
Can you run NordVPN on a router?
NordVPN can be set up on routers that support the OpenVPN client, extending VPN benefits to all devices connected to the network. This setup is ideal for users who prefer not to install a VPN on each device separately. NordVPN is compatible with various router models, and the installation process varies depending on the router type. This feature allows users to secure devices like gaming consoles that do not natively support VPN apps.
Setting up NordVPN on the router was a straightforward process that has greatly simplified securing my entire home network. With NordVPN running on the router, every device, including those that don’t support VPN applications like gaming consoles, benefits from continuous protection and privacy. This universal coverage has been a major advantage of using NordVPN in my home.
NordVPN for Kodi, Chromecast, Xbox, and Raspberry Pi
While NordVPN does offer easy-to-use and straightforward applications for common operating systems such as Windows, macOS, Android, and iOS, setting up NordVPN on complicated devices such as Kodi, Chromecast, Xbox, and Raspberry Pi can be difficult for you if you don’t have basic operational knowledge of the platform.
Set up NordVPN on the following devices with just a couple of easy steps:
To my satisfaction, I connected the VPN with the Chromecast. The enabling process was very easy and simple. After making the NordVPN Chromecast combo, I did a thorough test to ensure smooth streaming and compatibility. The NordVPN Chromecast integration worked flawlessly, allowing me to cast content from various regions without any geo-restrictions.
How to Install and Set Up NordVPN
To install and set up NordVPN, you have two primary options: downloading it from an app store or directly from the NordVPN website. This dual approach caters to users worldwide, especially in regions where app store access might be restricted, allowing for the alternative of downloading an APK file directly.
Here’s a simple step-by-step guide to get you started:
- Visit the NordVPN website or your device’s app store, if accessible, and look for the option to download NordVPN.
- Select a subscription plan that suits your needs. NordVPN offers a 30-day money-back guarantee, giving you the freedom to try the service risk-free.
- Complete the checkout process, where you’ll be asked for basic information, including your email address.
- Download the NordVPN application onto the devices you intend to use it on.
- Follow the provided instructions to install the app on your device, ensuring a secure and private browsing experience.
Compatibility Comparison: NordVPN, ExpressVPN, and Surfshark
If I compare ExpressVPN and Surfshark there’s no surprise that all three quality VPN providers support the most basic and common operating systems and platforms operated by their users.
| Devices | NordVPN | ExpressVPN | Surfshark |
|---|---|---|---|
| Windows | Yes | Yes | Yes |
| macOS | Yes | Yes | Yes |
| Android | Yes | Yes | Yes |
| iOS | Yes | Yes | Yes |
| Linux | Yes | Yes | Yes |
| Firestick | Yes | Yes | Yes |
| Android TV | Yes | Yes | Yes |
| Router | Yes | Yes | Yes |
While comparing NordVPN with its competitors, ExpressVPN and Surfshark, I found ExpressVPN to have an edge in terms of device compatibility. Although NordVPN offers robust support for multiple devices and up to 6 simultaneous connections, ExpressVPN excels in its wide-ranging device compatibility, allowing it to connect 8 devices.
This includes support for a variety of platforms, operating systems, and even some devices that are less common in the VPN usage scenarios.
Bypass Censorship⭐9.0
In terms of bypassing censorship in restrictive countries, NordVPN is an excellent choice. It can bypass censorship in countries like Saudi Arabia, Oman, Russia, Qatar, and many more, thanks to its excellent security features. I also witness its compatibility by using the NordVPN Russian region and unblocking all geo-restricted sites without any hassle.
Furthermore, it allows you to establish a secure connection to the internet along with additional features which ensure your privacy. NordVPN primarily offers obfuscated servers in Hong Kong, Canada, France, Germany, and many more countries. These servers add an additional layer of security as you access censored content without any restrictions.
Here’s a list of NordVPN’s obfuscated servers:
| NordVPN Obfuscated servers |
|---|
| Canada |
| France |
| Germany |
| Hong Kong |
| Japan |
| Italy |
| Netherlands |
| Poland |
| Singapore |
| Spain |
| Sweden |
| Switzerland |
| Turkey |
| United Arab Emirates |
| United Kingdom |
| United States |
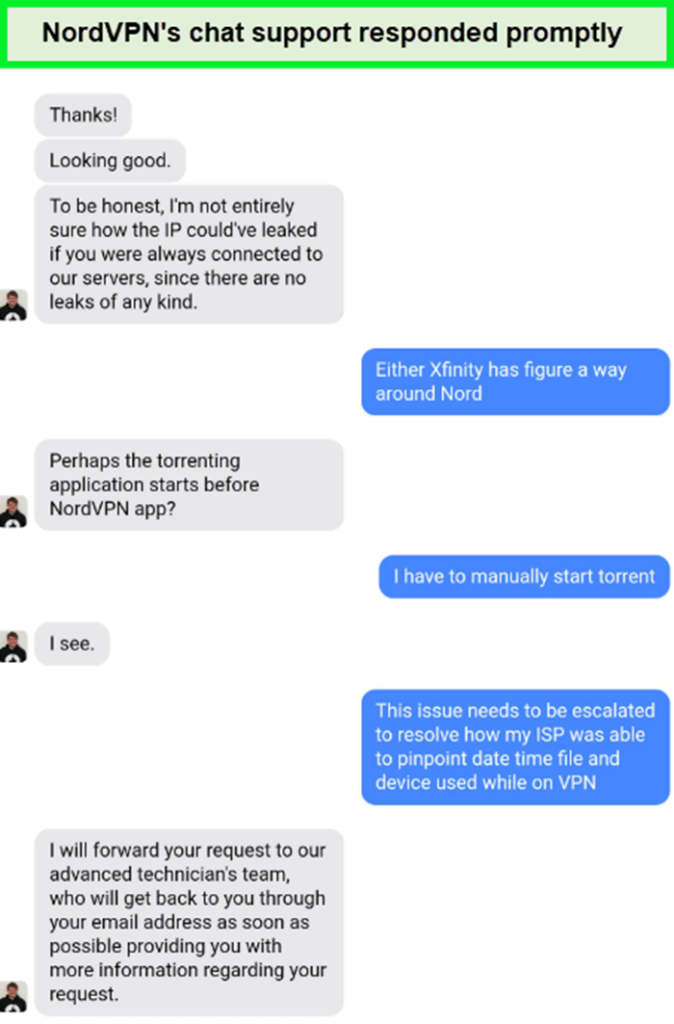
NordVPN Customer Support – Is it Fast and Reliable?⭐<9.0
NordVPN Customer Support is both fast and reliable, offering round-the-clock assistance through live chat, email, and a comprehensive knowledge base. The live chat feature is particularly commendable, with agents available 24/7 to provide prompt responses. In my experience, a query about NordVPN’s performance in China was addressed in just 30 seconds, showcasing the efficiency of their support.
 |
|
| 24/7 live chat | ✅ |
| ✅ | |
| Phone line | ❌ |
| Guides or articles | ✅ |
| FAQs | ✅ |
For more detailed inquiries or when live chat isn’t your preference, NordVPN’s email support is equally dependable. My email query was answered within 6 hours, a respectable timeframe in the NordVPN customer service realm. Moreover, NordVPN’s website hosts an extensive help section filled with guides, FAQs, and tutorials, aiding in the self-resolution of common issues.
It’s evident that NordVPN’s customer support stands out in the VPN industry. The presence of a Chatbot for immediate assistance with common problems, coupled with the knowledge and helpfulness of live support agents, underscores the quality of service. The fact that you can access live chat support without even registering is a testament to NordVPN’s commitment to user satisfaction and accessibility.
Regarding queries about NordVPN’s functionality in China, the support team informed me that while NordVPN operates in China, specific protocols and manual connections might be required, particularly the NordLynx protocol for Windows devices and manual setups for Android, iOS, and macOS. This level of detailed support ensures users in restrictive regions can still access reliable VPN services.
People’s Opinions about NordVPN review Reddit ⭐<8.0
If you head to Reddit, you will discover various NordVPN reviews. You’ll find users who will praise this service, while many of them will have multiple NordVPN complaints for you. Deep down, it is obvious that NordVPN is a customer-centric product determined to provide online anonymity with access to global content, and it can be clearly seen from NordVPN’s Reddit reviews.
Let’s take a look at a NordVPN Reddit review left by one of their satisfied users and learn whether is NordVPN legit:
Quick Comparison of NordVPN with Three Other Best VPNs in 2024
Here is a quick comparison between NordVPN, ExpressVPN, Surfshark, and CyberGhost:
| VPNs |  |
 |
 |
 |
|---|---|---|---|---|
| Jurisdiction | The British Virgin Islands | The Netherlands | Panama | Romania |
| Worldwide Servers | 3000+ servers in 105 countries | 3200+ servers in 100 countries | 6000+ servers in 61 countries | 11651+ servers in 100 countries |
| Security | AES 256-bit | AES 256-bit | AES 256-bit | AES 256-bit |
| Leaks | No IP, DNS & WebRTC | No IP, DNS & WebRTC | No IP, DNS & WebRTC | No IP, DNS & WebRTC |
| Avg. Speed | 89.42 Mbps | 81.32 Mbps | 83.82 Mbps | 75.47 Mbps |
| Multi-Logins | 5 | Unlimited | 6 | 7 |
| Unblocks | HBO Max, Netflix US, Hulu, BBC iPlayer, and more | HBO Max, Netflix US, Hulu, BBC iPlayer, and more | HBO Max, Netflix US, Hulu, BBC iPlayer, and more | HBO Max, Netflix US, Hulu, BBC iPlayer, and more |
| Compatibility | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers | Windows, Mac, Android, iOS, Linux, routers |
| Best For | Overall Best VPN | Fastest VPN Service | Best for Geo-Unblocking | Best for Private Browsing |
| Pricing | $6.67/mo - Save up to 49% with exclusive 1-year plans + 3 months free | $2.49/mo - Save up to 77% with exclusive 2-year plan + 30-day money-back guarantee | $3.99/mo - Save up to 63% with exclusive 2-year plan + 3 months free for a friend | $2.03/mo - Save up to 84% with exclusive 2-year plans + 4 months free |
Streaming services you can access using NordVPN
I tested around 50+ servers, including US, British, Canadian, Australian, and other regions. As a result, I unblocked this entire list of streaming platforms with NordVPN:
| American | British | Canadian | Australian | Other Regions |
| Amazon Prime Video | Sky TV | CBC Gem | Tenplay | German TV |
| Showtime | BBC iPlayer USA | Crave TV | 9Now | DStv |
| Disney Plus | Channel 5 | City TV | Foxtel | Hotstar |
| ESPN+ | Sky sport | Hayu | Stan | Rai TV |
| MLB.tv | Eurosport | – | Optus Sports | ViuTV |
| YouTube TV | ITV | – | Kayo Sports | Telecinco |
| MTV | Channel 4 | – | – | SonyLIV |
| Vudu | BT Sport | – | – | Showmax |
| Crackle | UK TVPlayer | – | – | – |
| beIN Sports | – | – | – | – |
| Sling TV | – | – | – | – |
| Bravo TV | – | – | – | – |
| Starz | – | – | – | – |
FAQs: NordVPN Review
Is it OK to use NordVPN?
Yes, NordVPN is highly recommended. It stands out as a top-tier VPN by offering a blend of security, speed, and a range of additional features for users to explore and customize their experience.
Can I be tracked if I use NordVPN?
Yes, with NordVPN, which upholds a stringent no-logs policy, your browsing activities and IP address remain untraceable. Nonetheless, logging into websites or utilizing apps on your device may still allow for some level of tracking.
Is NordVPN worth getting?
Yes, NordVPN is considered well worth the investment. User feedback consistently ranks it among the top VPNs for 2024, highlighting its fast speeds, robust online security features, and excellent streaming and torrenting support. Its capabilities extend to web browsing tools as well, making it a highly recommended option, according to user NordVPN reviews.
Can my internet provider see what I search with NordVPN?
No, when using NordVPN, your internet provider cannot see your online activities. They will only be aware that your actual online traffic is concealed. Consequently, they won’t have access to information such as the websites you visit or the specific web pages you browse and the duration of your visits.
Does NordVPN block router history?
Yes, NordVPN effectively obscures your browsing history from your router. By encrypting the data transmitted between your device and the VPN server, which lies beyond your router, your ISP remains in the dark about the IP addresses you connect to, as all your online activities are securely encrypted.
Can you cancel NordVPN at any time?
Yes, you can cancel your NordVPN subscription whenever you choose. However, it’s important to remember that cancelling a recurring subscription beyond the initial 30-day purchase period makes you ineligible for a refund.
Does NordVPN work in China?
Yes, NordVPN is among the VPNs that operate effectively in China. However, there may be instances when connecting to certain servers could encounter difficulties, especially if those servers are recognized as part of a VPN tunnel and subsequently blocked.
Does NordVPN offer the SOCKS5 proxy?
Yes, your NordVPN subscription includes access to the SOCKS5 proxy. This feature is particularly beneficial for use with torrenting clients, adding an extra layer of convenience to your VPN service.
Is NordVPN safe for Netflix?
Yes, using NordVPN for Netflix is both safe and legal. NordVPN is recognized for its reliability and security, enabling users to surf the web with anonymity. It stands out as one of the limited VPN services that successfully navigate Netflix’s intensified restrictions on VPN usage.
Is NordVPN faster than ExpressVPN?
No, ExpressVPN generally provides faster speeds compared to NordVPN, along with a broader selection of server locations, approximately 100 more. The optimal VPN choice, particularly in terms of speed and server availability, may lean towards ExpressVPN, depending on your desired country and server location for connection.
Final Verdict – Is NordVPN Worth the Money?
NordVPN excels in the VPN market with its robust security, user-friendly features, and reliable performance. It stands out for its AES-256 encryption and NordLynx protocol, making it a top choice for secure and private online activities, from streaming to browsing in restrictive regions. In my NordVPN review, I’ve found these features not only meet but often exceed user expectations, emphasizing its strength as a versatile and secure VPN solution.
Summing it up, NordVPN provides excellent value with comprehensive security features and an extensive server network. It stands as my top recommendation for those in search of a dependable VPN solution, guaranteeing a secure, fast, and unrestricted internet experience. When considering a NordVPN rating, it consistently proves itself as a top contender in the industry.

With every client update you have to provide your creds to login again and your old settings are lost (you have to set custom dns again, split tunneling, disable ‘help us improve’ etc.) At the moment even freaking youtube doesn’t work with this crap. Support treats you like an idiot tells you to reinstall the client no matter what issue you have. Stay away!
Hey there, sorry to hear about that. Can you tell us what operating system you’re using. Perhaps we can help you manage your system cache or get your issue highlighted to NordVPN.
Hoping to hear from you soon.
We’ve been using nordvpn for few years and everything was fine until we recently renewed with a discounted 2 year offer. Things worked fine for a few weeks then suddenly we were disconnected for no reason. We tried everything to reconnect but couldn’t even login to nord account. We had this problem on multiple devices. Nothing worked no matter what we tried. We tried support for help but no joy. We wanted refund but they said after 30 days they don’t refund. They took our money, gave vpn for few weeks then disconnected! Very dodgy! I don’t recommend nordvpn. We feel disappointed and conned.
Hey Jay, Thanks for your feedback. We are sorry to hear that the service did not come up to your expectations. You can try other great services like ExpressVPN, and Surfshark. You will not be disappointed.
I don’t know how they did it but there is some huge conspiracy regarding NordVPN. Everyone gives them a 10/10 perfect score and offer coupons which makes it seem too good to be true, well it is. Have gigabit internet? not anymore you don’t. prepare to be limited to downloading at 1.5mbps across the board. this has nothing to do with traffic or server or locations, there is a straight up cap on speed. the congestion will factor into the stability of that “speed”, but it will inevitably fall thanks to the auto connect algorithm. anyone having too good of an experience will get bombarded with the next wave of people auto connecting, should your experience be too good.
I never had this kind of experience, ever, with PIA. There were no hard caps on speeds and you could roulette yourself into actually getting on a good server which reflected your speed. My stupid self believed all the hype and ended up committing for 3 freakin years because it was only $99. Was such a terrible mistake.
Hey there,
Truly disappointed to hear you had such a terrible experience with NordVPN. In our testing, NordVPN performed exceptionally well, however, since you might be looking for an alternative, I suggest you checkout PureVPN review.
Just signed up for 3 years. Big mistake. I have broadband that gives me 240mbs on ookla.. When I turn on Nord I get 92mbs. This is a ridiculous drop in speed! Should have checked my speed sooner while I could still drop out. My bad.
Hey George,
Sorry to hear that. Have you tried switching to a server closer to you? You can also try switching to a different protocol through Settings > Advanced Settings > Protocols.
I had my own doubts, but once the audit results came in I’m completely confident with their service again.
A very bold move by the NordVPN indeed. But I wish they could publicly release the Audit report for everyone to see, instead just limiting it to NordVPN subscribers.
I like NordVPN app. Using it 3 years, they improved a lot of things here, add thousands of new servers all around the world, more useful features as cyber sec, smart play and created apps for streaming services.
Couldn’t have agreed more with you Frede.
The profile(?) page has abbreviations and esoteric terms, I am sure, are meaningless to the average user. The support page has a loop, so that if the question is not answered, loops back ad infinitum. Tried support; it has no intelligible way to add an ISP other than the few preferred. Much frustration trying to utilize the program, or, get help. The 24/7 support does not have chat, Email access, or, a phone number. How pray tell, does one use the VPN? My desktop has the NordVPN icon, but clicking on it does nothing. The tutorial, as they say in the vernacular, Sucks! There is no tutorial. If I can not use NordVPN, kindly refund my money, or, I will challenge the charge if it appears in my charge account. Nick M.
Hey Nick,
Extremely sorry you had to face such issues. I have escalated your query to the concern department of NordVPN, they should get back to you soon.
Is it true that NordVPN unblocks Netflix USA? I am currently using PIA and its pretty bad with Netflix. I am thinking about switching over.
Hi Hoffman,
It is true. NordVPN is one of the few VPN service that works well with Netflix.
When I connected to NordVPN UK server, it was showing me Malaysian server instead? How this possible?
Hi Ryan,
There must be a glitch in NordVPN’s tunneling system for this to happen. You should contact the support staff of NordVPN to sort this out.
Long time NordVPN user. My biggest problem with NordVPN is the lack of a good Linux client. Of course, setting up OpenVPN is not a big deal, but you will not benefit from dynamic server selection that picks a server that is not overloaded. It doesn’t look anything like that is on the roadmap so I am probably going to try ExpressVPN when my subscription expires. They seem to have solid Linux support.
Hi Arend,
Thanks for your valuable feedback. We agree with you. NordVPN being a top VPN provider should definitely have a Linux client.
There is no almost Linux support. The link for CLI app reffers to nordvpn.0.0.1.deb package. When I found on their ftp ver 1.0.6.deb. The app is Command Line Interface only, automaticaly chooses your remote server if no params. My impression that it is very beginner stage made, like just to fill the gap. The Network-Manager OpenVPN plug-in drop list supports only about 40 servers, you need to choose from their 5000+ servers.
NO GUI app for Linux !!!
Android app is very low profile as well, no Kill Switch, sudden drops.
My rating to NordVPN after 8 months of use is about 6/10, tried it on many devices and Op.Systems
Hey Vendetta,
Thanks for pointing that out. I did get a chance to tryout their Linux app and you’re right, it is definitely not up to their standards. NordVPN should fix this issue ASAP.
The Android app, on the other hand, worked great for me. Don’t know why you’re facing sudden drops. Just for reference, I use NordVPN on my galaxy S8+.
Pros:
-Netflix
-price (if you buy on deal)
-BBC iplayer
-fast torrenting
-lots servers
-cyber-sec feature
-browser extensions
Cons:
-doesn’t show location of servers (cities)
-onion over vpn very slow
Basically it is a VPN for everyday users, good for streaming. Not recommended if you want to do something fishy…
Hi Ronald,
Interesting points. NordVPN is the go-to VPN of everyday users.
Wow, the comments here are really merciless. My experience however has been positive, so either these people here are shills or extremely unlucky. Furthermore webRTC leaks most likely mean you have some malware downloaded and has nothing to do with quality of service… IF you are already compromised before connecting to a server how in the world you could become secure after connecting?
Hello Paul,
Everyone has their preferences when it comes to VPNs. We are glad to know you had a positive experience with the service.
NordVPN’s connection used to break quite often (now it’s getting better), and this does not depend on the “PC-ability” of the user. I’ve also experienced blackouts lasting even days. And c’mon, their Windows client Sucks, looks like the work of a child. Their linux “client” is nothing else than openvpn, that you must install, configure and run by yourself. But this, being the work of someone else, at least works!!
Hello Mario,
Hope you are the satisfied with some of the updates NordVPN has brought to its system.
The correct coupon for 70% discount is
** 70offyear **
Dear Tony,
Thanks for the info.
Friendly customer care department and big advantage they have live chat available 24/7 because some main players have just tickets system and you have to wait for hours for a reply and then, again and again, tons of time for each reply. Speeds are just perfect near ISP. Of course it depends on how far away the nearest server but from over 1100 you could find the best for you. And it’s quite the only one which still works with US Netflix
Hello Bridgewo,
There is no doubt, not Netflix’s accessibility is the biggest strength of NordVPN.
Between March and May this service was very good. June rolled around and something changed, the servers would just kill the data stream while remaining connected. sometimes it would take hours, other times minutes. some days the service is unusable as the loss of data stream would be so frequent nothing was usable. I have a ticket with Nord over 120 entries long, all I get is continuous change of techs who do not read the thread and request what has already been done. the replies from tech are now averaging over a week. between friends and family whom I recommended Nord to, 9 in all, we are all experiencing the same problem. this ranges from Toronto, Hamilton, Niagara Ontario, Oregon, Arizona, Florida, and West Virginia, and all but one have open tickets, Nord says I’m the only one with this problem.
Really?? even when I send them the ticket numbers of the others they insist I’m the only one. I got a 3 day trial with HMA 2 weeks ago and did not have a single loss of the data stream. same with IPVanish last week, so the problem is with Nord AFAIC. Nord does not the will, or expertise to fix this and last week refused to refund the unused part of the 2 years I paid for. they have no phone number and refuse to call, so you are stuck with chats which lead to a waste of time, and their ticket system which they reply to when someone else in their tech team decides to reply (11 to date).
I have access to 3 different isp services and public wifi, the data stream dies on all, and on all my devices, pc, ipad, iphone, android phone, android box, and xbox.
I have been with 7 different VPN providers over the years, this one has to be the worst so far. I chose nord because they are away from the 14 eyes, and the 1 month I took before signing up for 2 years was flawless.
Dear Tony,
I am sorry you had such an unpleasant experience with NordVPN. I hope the company has reached out to you and fixed your issues.
You forgot to tell to the people that NORDVPN is not useful for watching netxflix in linux (almost you sacrifice A LOT performance using a stupid VM).
Smart Play, not available in Linux, is secure proxy service that helps to overcome geographical restrictions put on by several websites. Smart Play re-routes the user’s requests through a server located at a place where access to such blocked websites is allowed. This makes the websites think the user is physically present in such place, thereby granting it the access.
Thanks for the info stupidcache. We will look into that.
I am active NordVPN user and also their beta tester.
So I can say, that those guys know what they are doing. Nord is really safe. Also they put huge effort on Netflix. I’ve tested several VPNS when was trying to access USA Netflix. Many of them say the work with Netflix, but in reality only Nord showed good result.
Glad you had a good experience Leek.
Tor hides all your internet traffic by wrapping your connection into 3 different layers. It’s like an onion where these layers are stripped as they pass through each node. The only node where your browser activity is known is at the exit node. By adding a VPN to the framework and using Tor, you can hide your traffic from being read by anyone. With a Tor + VPN, you hide the traffic at the exit node as well, making it impossible (almost) for anyone to see what you are up to.
Well explained P.P. It is true that Tor + VPN is a killer combination to acquire online privacy.
Well, if you are worried that your VPN will read your internet traffic then you should change your VPN. That’s why there is a big deal about whether the VPN keeps logs or not, the payment method it offers (Bitcoin instead of credit card) so that no records can be linked back to you.
Running a Tor locally through your VPN is some issues. For starters, you will be running the basic SSL connection with all its disadvantages and passing of keys. In addition to that, your entry point will be known as you will be running everything through the VPN and all your internet traffic from the laptop, PC, Smartphone and whatever will be passing through a single place, the VPN server. So it really doesn’t matter if you use a Tor or a VPN, your ISP will know that you are trying to hide your IP address and internet activities.
On the other hand, using a double VPN makes much more sense. Well, if you don’t trust your VPN or the entry point of Tor, then using a double VPN can provide you some security. But, Tor doesn’t hide your traffic beyond the basic SSL and since your internet traffic is passing through multiple VPN servers, you are just creating a lot of latency for yourself. A better way protecting your traffic from being read by your VPN is connecting to your destination with SSL through the VPN.
Hi kurtC,
Thanks for your valuable feedback.
As much as I love Nord, you shouldn’t really be using their TOR VPN. It’s better to use their double VPN along with Tor, instead of just using TOR VPN. What Tor does is that it decrypts your VPN traffic and then encrypts it again before sending it over Tor network. Using a double VPN means you add more security and 2 hops before it reaches Tor.
Hi Osborn,
You have a really valid point. Double does provide foolproof security.
I think their Tor VPN is really useful and I have been using it for a while. However, the lack of information and documentations available for servers is a bit irritating. I mean, it would be good that the pushed routes are a bit more concerned about the IP address of the destination server, instead of assuming that you want all your traffic to be pushed through 0.0.0.0/1 route and then to the outside.
Hello Normie,
NordVPN should definitely take your suggestions into considerations.
I have been using NordVPN on Linux and I am very happy with their service. They now offer VPN clients for Android and iOS devices as well but previously they only offered it on Windows. But won’t have any problems in using NordVPN on any device by using the .ovpn configuration file. I am using their service on Linux and really like it how they offer CA and TLS certificates for download separately along with .ovpn files. This makes it easier for me to configure the service with Linux Network Manager. However, one problem that I faced was that the zip file didn’t contain some of the servers they offered. If they can fix this then NordVPN is a top notch service.
Their customer support is also very good and the encryption levels are also decent. They offer AES 256 encryption and RSA 4096 bit for key exchange, which is pretty good considering it’s the strongest encryption out there. If I am not wrong, they only offer TCP 443 and UDP 1194 ports but it also offers LZO Compression, which is a good sign. I only wish they also provided lower encryption keys for mobile devices so that the battery doesn’t run out quickly.
The speeds are also decent but very inconsistent at times. Not all servers are quick at all times as some are fast but others are slow. Although they offer wide selection of servers, I really don’t think their servers are top notch. Their performance can be seen during the holiday season as during Christmas, there was immense load on servers and I got very slow speeds. However, it really depends on your connection as well. If you have a fast connection then it should not matter but if your internet connection isn’t lightening fast then you can face bottlenecks.
NordVPN is pretty big on preserving its users privacy as they claim to keep no logs of your internet activities. This is a good sign and also that the company is based in Panama, making it free any kind of foreign jurisdiction. Also, they accept Bitcoin as payment which good for privacy. You can pay for their anonymously. One important note, NordVPN offers its own Tor over VPN service. Although having a double VPN does beef up your security but I wouldn’t advice to use the Tor VPN offered by Nord. This is because your internet traffic will be decrypted before sending it over Tor, so it kinds of defeats the purpose of having double security.
Hi jjones,
Thanks for telling us about your experience with NordVPN. You have laid out the merits of this VPN service pretty well.
NordVPN ticks all the right boxes of being the best VPN. I am very happy with their service and would recommend it to anyone who is new to using a VPN.
Hi fnsm,
It is always good to hear from a satisfied VPN user. Glad that you are happy with the service.
I recently bought NordVPN a week ago and the speeds are awesome. Previously I used PIA (Private Internet Access) for more than a year but there were many problems with it, and I really didn’t like their user interface, it was ugly to say the least.
I selected NordVPN because it’s cheaper than PIA and it offers great servers options. I can connect to any location of my choice and access different streaming services. Like if you want to watch Netflix USA, there are servers available for that and you can enjoy your favorite shows and movies in high quality.
The security and anonymity provided by NordVPN is also pretty good. The protocols allow me to switch between high security to high performance streaming. You can check out NordVPN using their 3 day free trial by contacting their customer support. If I remember correctly, I signed up for their service but didn’t pay yet. I then wrote an email to their customer support and they activated my 3 day free trial.
Hi Manwithoutfear,
Good to hear that NordVPN is meeting your expectations.
Very bad service.
See my conversation on customer service.
Yana
Hi. I want moneyback
Brian в чате
Brian
Hello, may I ask what went wrong and why do you wish to cancel our service?
Yana
Slow program errors. IP addresses are in the blacklist. Once connected, you can identify my real ip on webrtc.
overall I am very unhappy
Brian
WebRTC is a browser leak. You need to disable it on your browser: https://nordvpn.com/blog/important-notice-browser-security-hole-detected/
May I ask what services you were unable to access?
Yana
I want moneyback
I do not like your service as a whole
Brian
I see that you have paid via bitcoin, I am sorry, but payments via bitcoin is not refundable, please check our terms of service: https://nordvpn.com/terms-of-service/
Yana
wtf?
why?!
Brian
This our policy, you agreed with our terms of service upon purchasing your account.
Yana
This is the most disgusting site vpn that I’ve ever met
I will write reviews about you as the worst vpn provider.
It’s outrageous!
I will write about this in all forums and blogs!
You stole my money!
Brian
We do not, our terms of service clearly states that we do not refund bitcoin.
If you have any complaints, I would suggest to contact our sales team by email at support@nordvpn.com
Yana
Do you you have no right can decide to return the money or not!
You provide a service – I pay the money.
The service is not necessary – you return me the money!
You illegally hold my money!
You’ll soon see at each site where you are – a review of your service.
Brian
No, we don’t. Everything is legal. We provide money back guarantee for 30 days, however payments via bitcoin are not refundable. I can’t provide a refund against our ToS, however you can write a complaint to our sales team at support@nordvpn.com
Yana
You know yourself, what you say? You decide to return money or not for yourself! Unless it can be legally ?!
Why do I have someone to complain and write email, to take my money! My money!
Brian
You paid your money for the service and agreed to the terms of service before making your payment.
These terms are the same now as they were when you have purchased the subscription.
Yana
Your terms are illegal! Who gave you the right to make such rules? Do you think that strange incomprehensible rules like your site to be perceived above the law? What you are kind of nonsense? There is a law on consumer protection! And I do not care what you have there for the rules! You submit to this law!
I do not care for your rules, when speech goes about the law. And the law requires you to give me back my money! No matter which way I paid for!
Hi Yana,
It is unfortunate that you didn’t like the service. However, most VPNs do not offer refunds for Bitcoin.
I dont know how they can be most recommended logless VPN for god sick.
– They leak your IPv6
– No switch kill for internet connection
— but worst of all THEY LEAK YOUR REAL IP—
If you using Windows (7) like me you are fuck up.
I was surfing all day and i normally do not turn off my PC but only switch it to sleep mode and even I set automatic reconnect and EVERY TIME i turn my PC into sleep mode and then woke up my PC their official application showed me that i am “CONNECTED” with green status but in real i was not connected and all of time i was surfing under MY REAL ADDRESS.
Sad to hear that!
I recommend you to send an email to them if you have any issues.
As a comment below mentioned, you’re likely leaking WebRTC requests which is caused by the browser not by NordVpn.
Signed up with a 70% discount and was super easy. The app is excellent and the speed is perfect.
Anyone reading this, research some more yourself. Nord is solid.
I currently have Nordvpn installed.
Although It is clearly stating that it is connected to Russia ISP 213.183.56.210
It is is fact connecting to US 45.55.199.109 New York.
Discvovered this when Amazon UK stated that it could not deliver to US.
Checked ‘What is my ip address’, and yes it confirms New Youk.
Very bad this, beware!
Hello Charlie,
Thank you for your feedback.
It is quite unfortunate that you face such issues with NordVPN.
Why don’t you try emailing them?
NORD is VERY unstable and slow. It is not unusual to have to reconnect 10 times a day, and has hour+ long blackout periods.
The worst part is, to get a new connection; you often have to bounce from one location to another which is the antithesis of why we want VPN.
They also are crooks who do not honor their word and give a refund.
STAY AWAY, there are MUCH better service for close to the same price !!
Tech Advisor,
I am sorry you had a bad experience with the service. I hope you find a suitable alternative.
NordVPN
claim to be offering 70%. On their registration form they enter the code “70off”
automatically. I tried to register for what appears to be a great offer. After
clicking register it simply says “ERROR Coupon code “70off” is not valid use a
valid coupon only”. Its their own code, they inserted! I then had to suffer
what they claim to be “customer service” having a futile discussion with this
imbesile with a purile attitude and contradictory
statements:
*** Molly joined the chat ***
(09:44:14)
Molly: Hello. How may I help you today?
(09:44:19)
Visitor 39343896: Your site isn’t working properly
(09:45:21)
Visitor 39343896: I’m trying to sign up and your site
is offering 70% off, its automatically putting that into the registration
process with the code “70off”, but when I press register is say the
coupon is not valid.
(09:45:42)
Visitor 39343896: Very frustrating when its my first
experience of your service, not a great start
(09:45:54)
Molly: Yes, we are aware off this. Sale most likely ended and someone forgot
to take the banner down. Sorry for the inconvenience.
(09:46:10)
Visitor 39343896: It says he sale doesn’t end for 3
days!
(09:46:13)
Molly: You may email us at support@nordvpn.com and we might still offer you a
dealbreaker like 70% discount.
(09:47:08)
Visitor 39343896: I’m expecting more seeing as its
still on your site, I’m notifying you off the issue, its my first experience
with you and I spent 5 minutes writing a message before you came online
(09:47:25)
Visitor 39343896: I don’t expect to take up more of
my time when I can easily go to a competitor
(09:48:22)
Molly: We do not force our potential clients to choose 🙂
(09:48:35)
Molly: Sorry for the inconvenience.
(09:49:09)
Visitor 39343896: OK, if thats your attitude, I’ll
happily post my review of my experience with NordVPN and take my business
elsewhere
(09:50:45)
Molly: There is no attitude sir, we just do not force our potential customers
to choose us by compromising their own decision.
You sound like a real douche. NordVPN is actually really stable and very easy to setup. If you’re leaking your real IP, then take two seconds to actually read up why and how to fix it. It has nothing to do with NordVPN, your system is most likely leaking WebRTC requests which you’d know you have to fix if you’d taken two seconds to research.
I’ve used NordVPN for 8 months and have no issues. The problems you’ve describe all sound like you have no idea how to use a PC, they are not NordVPN issues. You should simply stop using PCs since they’re obviously too hard for you to grasp. Use a public library from now on or ask someone to teach you PC basics.