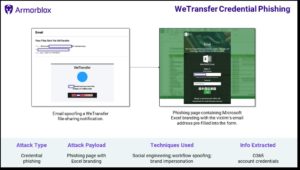
A report by Armorblox claimed that cybercriminals have found their way into the WeTransfer hosting system and are now carrying out multiple phishing attacks. In these attacks, the spoofed email ends up leading to a cloned page with Microsoft Excel branding, which aims to retrieve the Office 365 email credentials of people who fall prey to these attacks.
For your information, WeTransfer is a file-sharing service used to transfer files too large to be sent through email.
Armorblox Over WeTransfer Phishing Attacks
The phishing email looks incredibly authentic and can deceive even a regular WeTransfer user anytime. It bears the name of the sender of the files as well as the ‘View Files Sent Via WeTransfer’ option.
The email body further contains multiple references to the organization, so the email receiver doesn’t question its legitimacy. It further reveals two links sent and a link to view those files. When the victim of the attack clicks on the link, it leads to the phishing page of Microsoft Excel.
The Microsoft Excel page displays a blurred-out spreadsheet at the back with a form in the front which requires the victim to log in. The form already contains the victim’s email address, endorsing its legitimacy every step of the way.
The domain sending all these emails is known to be a Japanese web hosting service named ‘valueserver[.]jp’, which was previously involved in another phishing attack case last year, as reported by Laur Telliskivi, an Infosec analyst.
What Techniques are Used in the Attack?
Multiple techniques have been used in the attack to lure victims and bypass the security filters of conventional emails. One of these includes social engineering, which creates urgency and trust in the victim by sending in the email title, sender’s name, and content in the email.
The second technique used in the attack, which is worth mentioning, is brand impersonation. The HTML of the phishing email is exceptionally similar to WeTransfer, and the phishing page is designed to look exactly like Microsoft Excel’s actual login page. However, the only fishy thing that sets them apart is that Microsoft is spelled like ‘MicroSoft’ on the phishing page.
In the End, How to Protect Your Data from Phishing Email Scammers
Phishing attacks are likely to increase in the future. Here are a few tips to protect yourself from phishing scammers:
- Read every email carefully and look for minor inconsistencies, including the sender’s name, domain name, email address, and more.
- Carefully check the language used in the email.
- Set up multi-factor authentication (MFA) on all business and personal accounts.
- Use a different password for all accounts.
- Set up antivirus with a VPN for added encryption on all devices.