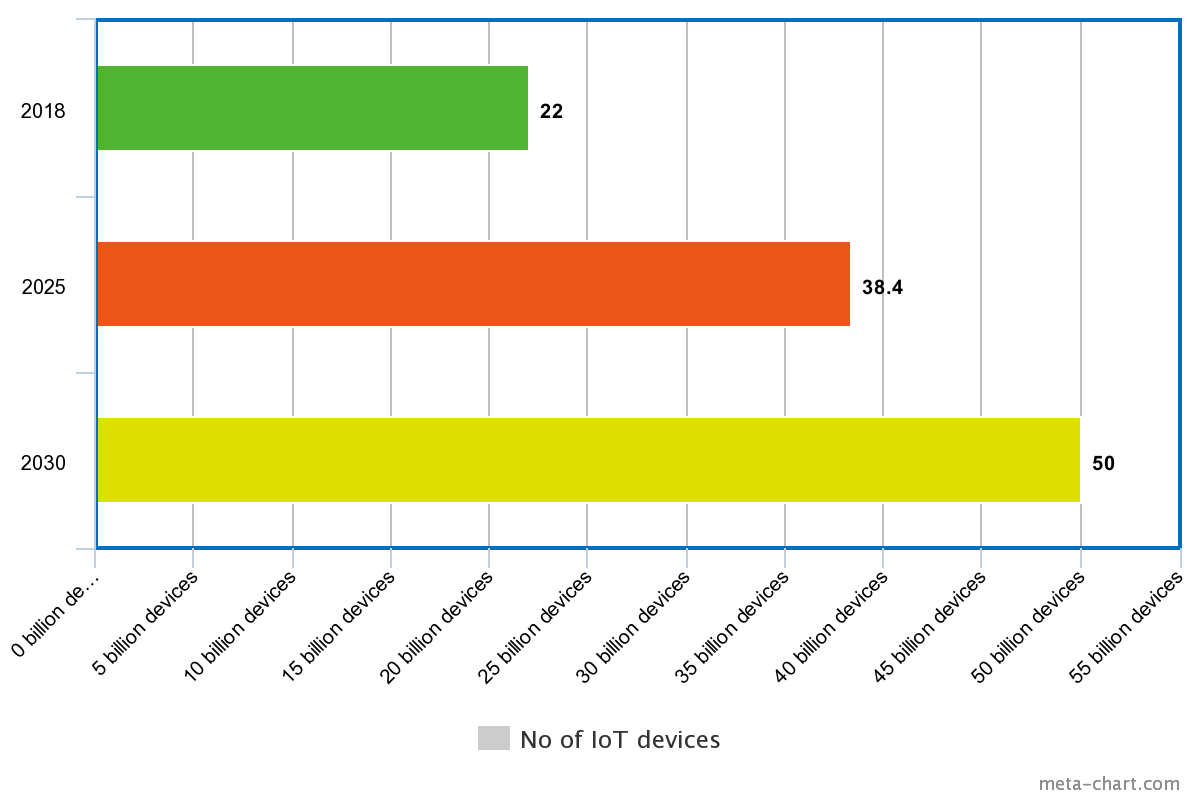
The long-awaited high tide of the IoT industry is just around the corner. It was estimated that the smart home market will grow by $54 billion by 2022. And predictions show that by 2050, there will be more than 100 billion IoT-connected devices in the world. But there are too many risks related to these IoT connected devices.
Have you heard how hackers accessed a baby monitor? Or Iran hacked a US drone? Or you only care about how an IoT device can switch on your bedroom lights?
What is IoT?
IoT (Internet of Things) refers to the connection of physical devices through a cloud-based network. Every physical device which includes your coffee maker, Apple Watch, baby monitor, smart refrigerator, or faucet that has a sensor and internet connectivity is an IoT device. Simply put, any physical device that you can monitor or control by using an internet connection is considered an IoT device.
But hackers can access these IoT connected devices. This is the reason why protecting your data is important. It is estimated that the amount of data generated by IoT devices is expected to reach 73.1 ZB (zettabytes) by 2025. And you have to protect this information from cyber-attackers.
Due to IoT, humans are creating a huge amount of data. And IoT is putting humans at risk of data exposure as well. With such an enormous amount of data, the risk of security breaches also increases.
Security Challenges of IoT
IoT is becoming a threat to humans because it does not have standard security protocols. As more organizations and cities are going to use IoT devices in the coming years, it must have an extra layer of security.
Man-in-the-Middle Attack (MiTM)
During a MiTM attack, hackers will try to connect your device to a rogue internet connection. And you will have no clue that you are using a different network. And, if hackers can successfully perform a MiTM attack then they can control your internet searches and access your private data.
Network Security
Authentication is another security challenge of IoT devices because they create and share unprotected data on the cloud. The security of IoT connected devices depends on a base station which is your Wi-Fi, and hackers can easily hack it anytime.
Data Security
Five IoT devices need five encryption keys. You can use a single encryption key to lock or unlock multiple IoT connected devices. But, using a single encryption key for multiple devices is risky. Because if hackers can get access to a single IoT device then they can control all connected devices.
Web Interface
The web interface of IoT connected devices must be protected with a security protocol. Every IoT device, ranging from your smart microwave to a smart light bulb should be continuously upgraded over time to enhance security. But after an upgrade, the manufacturers must also test IoT connected devices before selling them to users.
Recent Attacks on IoT Connected Devices
IoT is transforming from the Internet of Things to the Internet of Threats.
Pet Feeder Goes Offline
The above story is an example of a device malfunctioning. Imagine if your pet is starving for a week? Just because your IoT device has stopped working due to internet connectivity issues.
Unsafe Baby Monitors
The baby monitor has a weak password that hackers used to control a baby monitor. But how? Weak encryption is a sweet spot for hackers to control your IoT-connected device.
Robbing the Bank of Chile
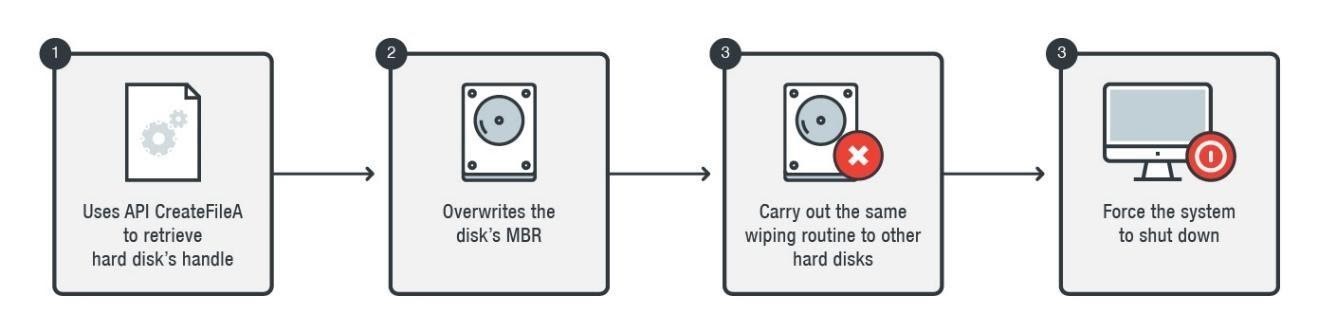
Hackers used a virus, named KillDisk, to penetrate Bank of Chile’s computers and servers. The hackers shut down the entire system, put it on reboot, and stole up to $10 million on SWISS wire transfers. The above picture is a glimpse of how hackers infiltrated and attacked Banco de Chile through IoT connections.
Iran Hacked a US Drone
Iranian hackers got access to the USA’s command center and hacked one of their drones. Later, hackers showed bird’s eye footage of the drone and landed it safely somewhere. By hacking GPS navigation on the drone, Iranian hackers were able to access and control a US drone.
When a drone is using GPS navigation it automatically runs on autopilot, which exposes its security protocols. So it was easier for hackers to target and control a US drone while it is navigating the perimeters.
Researchers Hacked a Driverless Car
A few researchers were checking the security protocols of Fiat cars. There is an Uconnect feature in the Jeep that has internet connectivity that researchers hacked easily to control Fiat Jeep. Proving that the manufacturers of driverless cars have to streamline their control units for better security.
There are many unprotected access points in IoT connected devices that are important to secure. As many companies outsource IoT-driven apps and home devices, their security protocols are not strong enough against cyberattacks. Companies cannot create security-driven processes without knowing about the real flaws in IoT connected devices.
What Experts Say about IoT Connected Devices?
Many cyber-security experts have shared their opinions on the security flaws and dangers of IoT connected devices.
Jothy Rosenberg – CEO of Dover Microsystems
The problem IoT has is that the processors of IoT devices use a Von Neumann architecture, which is 75 years old and traces back to 1945. This means our processors are simple and have no way to know if what they are doing is the intent of the application developer or if they are doing an attackers bidding.
Amy Smith-Technology Analyst at FitSmallBusiness.com
One of the biggest risks is the lack of security knowledge among consumers. Users of IoT devices need to ensure they’re changing the default network names and passwords whenever they connect their devices to Wi-Fi. Otherwise, they risk exposing their data to hackers.
Emily Healy – Cyber-security expert at Secrutiny
In our 2022 predictions, we noted that IoT will be targeted as a new route to breach internal environments. That camera or smart TV or heating controller makes a difference. The speed to market for vendors is paramount as competition is high; it’s a land grab for customers.
Jake Rowlands – Wildfire
The influx of new IoT devices entering the workplace presents a multitude of challenges as IT teams are struggling to maintain device security. For every new device brought into the workplace, a CIO must consider the impact on the wider IT and security ecosystem, which can keep enterprises safe from potential cyber-attacks.
How IoT will be making a Huge Impact on Our Lives
Analyzing Data Accurately
There is a massive amount of healthcare data, and IoT devices will be used to take care of tedious tasks like segmenting this data into specific orders. As IoT-connected devices can create accurate scans and detailed health reports, doctors can speed up data processing.
Adapting to Consumer Needs
IoT will be used to predict how consumers are going to use utilities, such as water, electricity, and food. IoT-enabled devices will help in forecasting consumer needs and influencing the agricultural industry.
Building Smarter Cities
As I have discussed previously, few cities are already using IoT-backed devices to build a smart city, which will be free of traffic, air pollution, and road accidents. By using IoT, many cities will create a cloud-backed system to check air pollution, traffic management system, and create data of citizens.
Safeguarding Blockchain Technology
As IoT is not connected to a decentralized system, it enhances the risk of exposure to malware attacks or hacking. This is the reason why Blockchain and IoT can be a perfect blend because IoT needs to rely on a decentralized system with heavy security protocols.
What’s Next for IoT?
As IoT connected devices will be common in just a few years, security is the biggest concern for users. IoT connected devices need better security protocols as well as regular firmware upgrades to combat growing threats.
For this to happen, security regulators must create security-backed policies to make sure every IoT device manufacturer is prioritizing security.
Furthermore, IoT device users must also know how to prevent security breaches. Developers must ensure that IoT devices have a strong passcode, secure interface, and safe internet connection upon deployment.
Here are a few things that leading organizations must consider when executing the design of IoT devices.
- Ensuring the right team have the authority to manage IoT device security
- Adding more product-savvy resources in security teams
- Assessing how IoT-driven data is protected and processed to prevent attacks
- Using risk-assessment models and past threats to integrate security protocols in IoT devices
- Incorporating industry-specific teams for designing secure IoT devices
In this way, we can try to cut back the security breaches on IoT connected devices in the future and ensure high security. Boosting security is a challenge for IoT device manufacturers and these devices will remain at risk as long as we are using obsolete security methods. The security arrangements will have to keep catching up as we advance in technology.
That is our only hope if we are to curb the threat posed by hackers in an era where digital devices are well on their way to outnumbering people.
