Following the forensic investigation, Zimperium’s zLab’s threat research team discovered undetected apps on mobile using Zimperium’s z9 malware engine. They determined that the undetected malware is part of a Trojan family that uses social engineering techniques to hijack Facebook accounts.
The Zimperium zLabs team discovered an Android Trojan that has spread to 144 countries. Codenamed FlyTrap, this malware hides behind applications to steal social credentials from its thousands of victims and spread misinformation. #WeSecureMobile #FlyTraphttps://t.co/h69wwatoFH pic.twitter.com/N3CgXElY7v
— ZIMPERIUM (@ZIMPERIUM) August 9, 2021
The research team discovered evidence that points out to malicious parties in Vietnam running this social media hijacking campaign since March 2021. The malware was initially distributed via Google Play Store and third-party applications.
zLabs reported its findings to Google, who verified the information and removed malicious apps from the Play Store. However, these apps are still available on third-party app stores, “highlighting the risk of sideloaded applications to mobile endpoints and user data,” points out Zimperium.
zLabs also provided a map showing the distribution of FlyTrap victims across 144 countries.
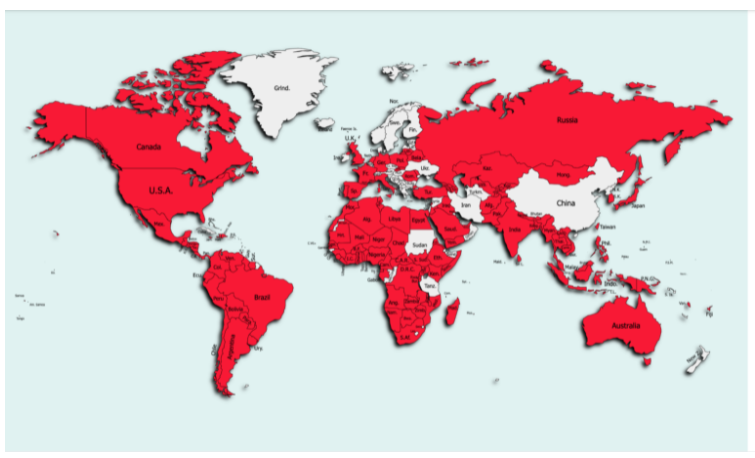
FlyTrap victims distribution map. (Image: Zimperium)
What is FlyTrap Trojan?
FlyTrap trojan embedded in applications poses a threat to the target’s social identity by hijacking their Facebook accounts by injecting the malware on their Android devices. It collects the following user information of the victims:
- Facebook ID
- Email address
- IP address
- Location
- Cookies associated with the Facebook account
These hijacked Facebook accounts can be used to spread the malware from one victim to another as well as spreading disinformation campaigns using the target’s geolocation.
How Does FlyTrap Malware Work?
The cybercriminals behind FlyTrap use various appealing methods such as free Netflix coupons, Google AdWords coupons, and voting for the best football team or players. Initially, the application tricked users into trusting the app and downloading it. After downloading the app, it engaged the user by displaying different pages or asking them to vote for the best team or more.
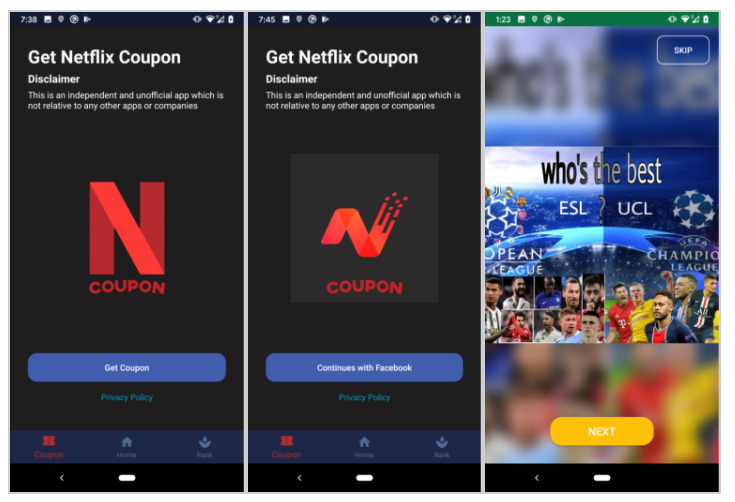
(Image: Zimperium)
It then shows the user Facebook’s legitimate login page and asks them to log in to their account to be able to cast their vote and collect the coupon code. Once the user logs in and takes part in the “fake voting”, it displays the fake coupon code and a message stating that the “coupon code expired,” as shown in the screenshots below:
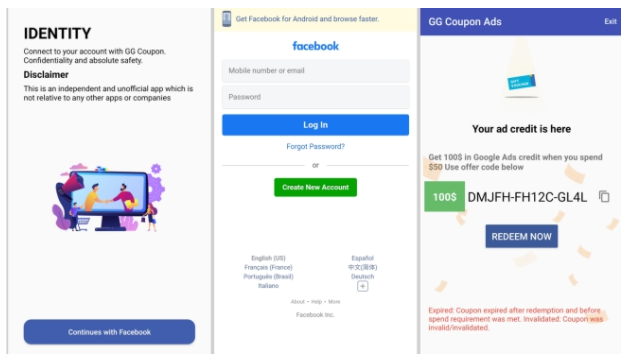
(Image: Zimperium)
Once the user’s logs in to their Facebook account, the malware uses JavaScript injection to hijack targets Facebook ID, email address, IP address and location by using the malicious JS code.
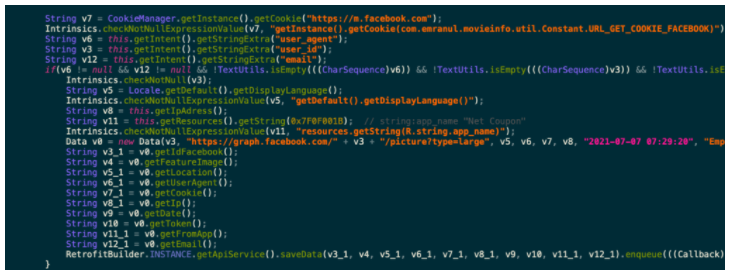
Code screenshot containing the type of data that will be exfiltrated to the Command and Control Centre server. (Image: Zimperium)
The manipulation of web resources is called cross-principal manipulation (XPM). For more information, you can check out this study, “An Empirical Study of Web Resource Manipulation In Real-world Mobile Applications.” After successful login to Facebook, the victim initiates the data exfiltration process, as can be seen below:
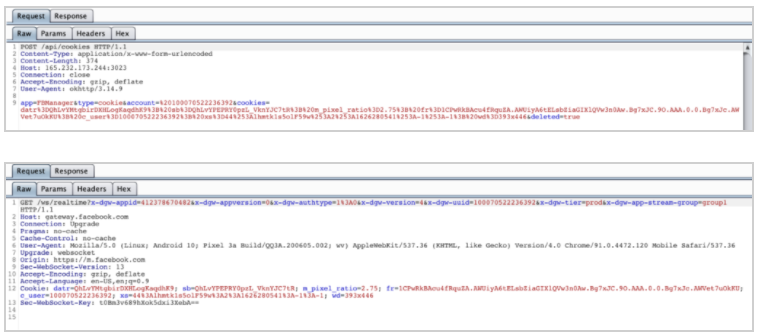
FlyTrap data exfiltration in process. (Image: Zimperium)
The Command and Control server then uses the Facebook login credentials to access harvested data. What’s worst is that due to security vulnerabilities in the Command and Control server, the entire database of stolen information can be exposed to anyone on the internet.
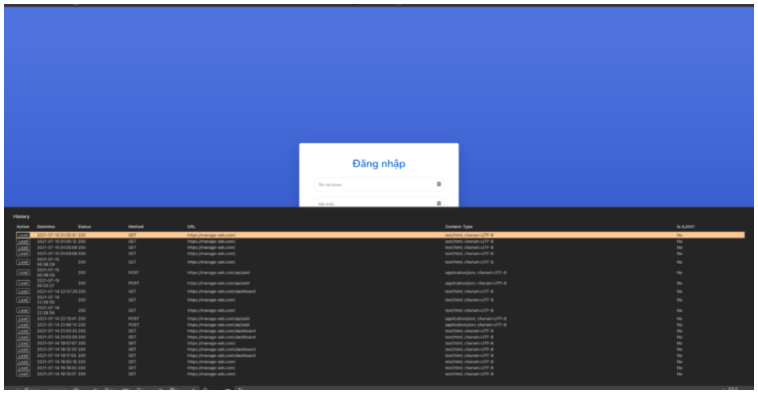
Command and Control server storing hijacked sessions. (Image: Zimperium)
FlyTrap Trojan Android Applications
Zimperium’s zLab has released the following list of indicators of compromise as seen in FlyTrap malware Android applications:
- com.luxcarad.cardid : GG Voucher
- com.gardenguides.plantingfree : Vote European Football
- com.free_coupon.gg_free_coupon : GG Coupon Ads
- com.m_application.app_moi_6 : GG Voucher Ads
- com.free.voucher : GG Voucher
- com.ynsuper.chatfuel : Chatfuel
- Com.free_coupon.net_coupo n : Net Coupon
- com.movie.net_coupon : Net Coupon
- com.euro2021 : EURO 2021 Official
Command and Control Servers:
- hxxp://47.57.237.26
- hxxp://165.232.173.244:3023
- hxxps://manage-ads.com
- hxxp://quanlysanpham.work
How to Protect your Android Device?
FlyTrap Trojan is just one example of the ever-increasing and prevalent security threats aimed at stealing personal information. Another recent malware targeting Android users was the Joker Malware that also used Google Play Store to infect devices.
Zimperium’s director of endpoint security, Richard Melick, said that Android users could decrease the chance of infection by blocking the installation of apps from untrusted resources in the background. This is also available in the recent Android security update.
If you suspect that your Facebook account has been compromised, log out of all devices immediately. Melik also advised,
“Overall, it is about being aware of what an application is asking for. If you need to connect to your social media accounts to get access to a coupon or deal, pause and ask why. What could the site/ coupon company now use that data for?”
To ensure that your Android devices are protected from malware, we recommend using anti-virus/ malware software and a VPN for Android. You can also get a VPN that offers an antivirus feature as well like Norton Security, McAfee Safe Connect and more.
