Call center scammers are using Justin Bieber’s upcoming world tour tickets, The Weekend’s concert, and fake gun purchases to spread malware, and stealing almost $50,000 per attack, reports Proofpoint.
Cybersecurity company, Proofpoint reported on Thursday regarding an uprise in call-center-based scams, with threat actors stealing as high as $50,000 an attack in some instances.
Researchers Selena Larson, Sam Scholten, and Timothy Kromphardt say that their company Proofpoint sees thousands of call-center-based cyberattacks each day. Some use fake malicious call centers to scam people, while others use fake malicious call centers to spread malware that can be used for future attacks.
Proofpoint further revealed that the activity is tied mostly to individuals working in the Indian cities of Kolkata, Mumbai, and New Delhi. Cybercriminals are using different ways to scam people presenting themselves as “Justin Bieber ticket sellers, COVID-relief fund services, online retailers, computer security services, or financial support programs.”
Financially Motivated Call Center Attacks Explained
The attacks begin when the victims are sent an email along with phone numbers of “customer service” that they can contact for claiming relief funds, concert tickets at a discount, and more.
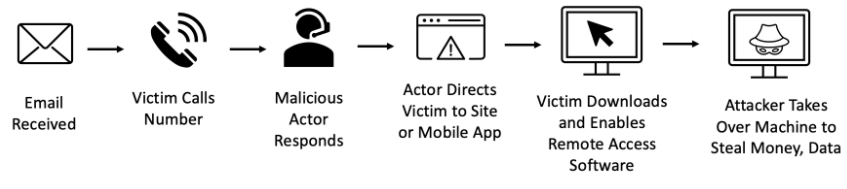
Financially motivated call center attack path. (Image: Proofpoint)
Once the victim calls on the number, they are directed to an infected site or app. It installs software used for remote access on their devices such as AnyDesk, Zoho, Teamviewer, etc. It provides device access to cybercriminals.
Often, the victims are advised to log in to their bank accounts online to purchase gift cards or get a refund. Once they are connected, the attackers blackout the screen, taking over and stealing the money.
Malware-focused Call-Center Attacks Explained
In malware-focused attacks, like the infamous BazaCall, the criminals use elaborate measures and themes to lure victims such as fake movie sites, Justin Bieber concert tickets sellers, lingerie sites, and more.
The victims are often directed to click on a link or download a form to get a refund, or special discounts. Instead, they are infected with malware.
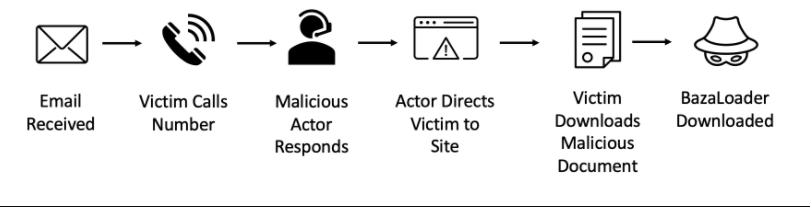
BazaCall malware attack path. (Image: Proofpoint)
Most campaigns use pop culture themes to lure victims. Some posing as ticket sellers to the upcoming Justin Bieber world tour 2022, The Weekend concerts, and more.
“Once the attackers have obtained access to the device, they can access banking, email, and other private accounts or download follow-on malware including ransomware.” – Proofpoint researchers.
Proofpoint also said that when their researchers called on the number in an email received by scammers, they were immediately placed on hold with Justin Bieber’s music. The analyst was then asked to visit a malicious website as a way to solve a dispute of concert ticket sales. Once the malicious document with BazaLoader was downloaded on the victim’s system, the attacker hung up.
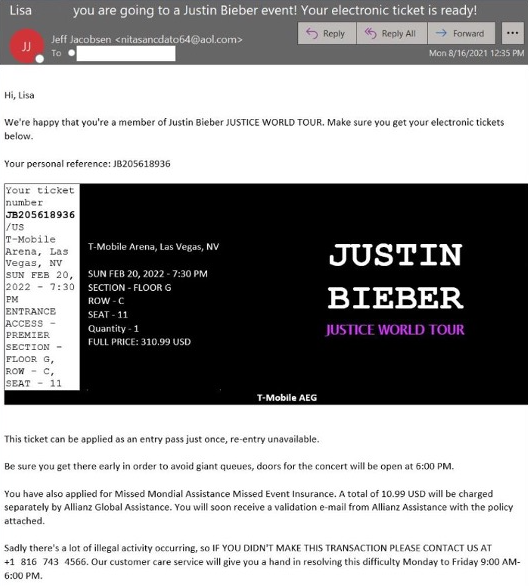
Image: Proofpoint.
Call Center Scam Threat Actors
Although it is difficult to exactly narrow down the activity to a specific group, Proofpoint researchers have identified multiple clusters located in India with TOAD threats. Most activity is identified in three Indian cities: New Delhi, Mumbai, and Kolkata.
Using the information shared on forums and YouTube, Proofpoint was able to pin down physical locations of activity clusters of these threat actors in India, as shown in the following map below:
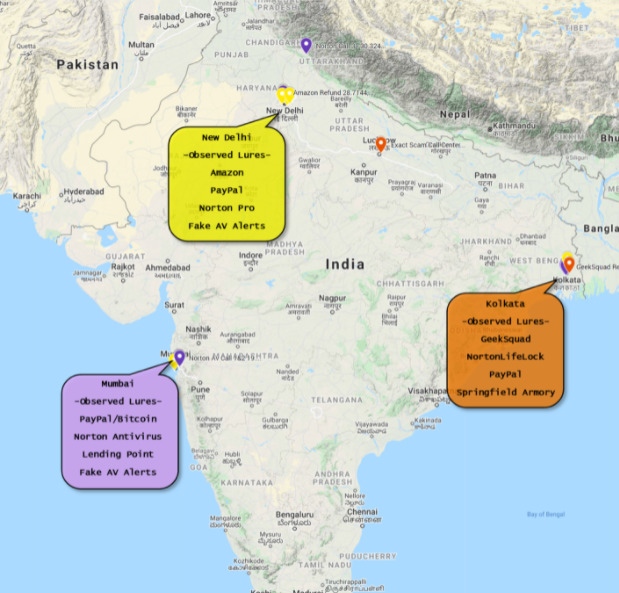
Image: Proofpoint
The threat actors reportedly targeted people in the US, Germany, Australia, and India, posing as tech support. According to the BBC, the earning of threat actors start at Rupee 1 for every $1 and may increase up to $50,000 per month.
According to John Bambenek, Netenrich principal threat hunter, call center scams are not new and have been used in the past as well. He also said that these techniques don’t scale and “it’s not uncommon for defenders to call these numbers to tie up the time of the attackers.”
The threat actors are no doubt getting creative with their lures, using the latest pop sensation to hook victims. Proofpoint has also seen BazaCall scammers target employees of large organizations as well, leading to ransomware attacks.
We have also seen multiple attacks leveraging the sensational Netflix hit series Squid Game – the recent Squid Game cryptocurrency scam and Squid Game malware apps.
Here are some tips to protect yourself against vishing scams like BazaCaller:
- When you receive marketing emails, read them carefully and look for grammatical mistakes, and more to spot fake emails. DO NOT click on any links.
- When visiting websites, look for verified marks to tell the difference between fake and authentic apps.
- Use anti-virus software that will give you a heads-up when you open a malicious website. There are VPNs that offer antivirus features as well that you can use to double security.
- Use multi-factor authentication (MFA) on all online accounts.
- Ensure your email/web security is updated and start using security tools such as encrypted VPNs that include anti-phishing capabilities.
- If you receive any fraudulent email or phishing email, you can forward it to local authorities for further investigation. For people in the US, you can forward the email at reportphishing@apwg.org.
